
vBulletin is a professional, affordable community forum solution. It gives you an instant community that lets your users to interact, take part in discussions, ask questions, give answers and express opinions.
The latest version of vBulletin is vBulletin 5 Connect and vBulletin Cloud.
List of Features –
- Full support for the Akismet anti-spam service stamps out comment spam.
- Unlimited Hierarchy of forums
- Support BB Code/HTML in posts
- Extensive personalization
- Engaging social functionality
- Optimised mobile experience
- Excellent customer support
The newest release of vBulletin 5 Connect includes many major features. From a search engine optimization to user management panel. You could use the RSS support, interface localization, moderator control panel, captcha, login strike system etc.
OWASP VBScan is an opensource project in perl programming language to detect VBulletin CMS vulnerabilities and analyses them. VBScan tool is a best tool for specially pentesters who want to test the security of the website.
The latest version of OWASP VBScan is 0.1.7.1.
Installation of VBScan in Kali Linux –
To install VBScan, please type “git clone https://github.com/rezasp/vbscan.git” in your Kali Linux machine.

To run this tool, type “perl vbscan.pl” which shows the welcome screen including the banner and usage options.

Before to run this tool, change the permissions by typing “chmod +x vbscan.pl” in your same terminal.
Now the tool is ready to scan all the vBulletin related vulnerabilities. To find vulnerable vBulletin sites, you can use this Google Dork – “inurl:”search.php?search_type=1“.
To run VBScan, type “perl vbscan.pl http://example.com”
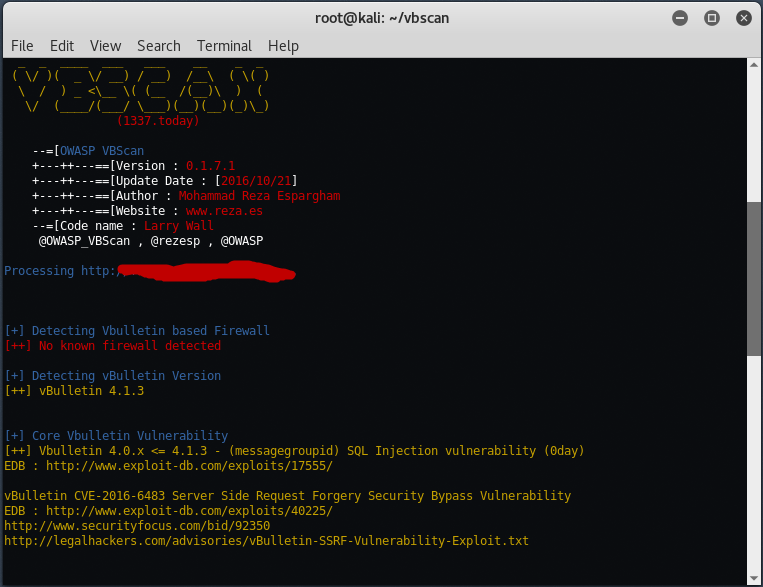
As you see that this tool will automatically detects the vBulletin version and based on that version, it will lists all the vulnerabilities present in that particularly version.
The vulnerabilities which VBScan uses are –
- [+] Detecting Vbulletin based Firewall
- [+] Detecting vBulletin Version
- [+] Core Vbulletin Vulnerability
- [+] Checking apache info/status files
- [+] Checking admincp/modcp path
- [+] Checking upgrade.php to find admincp
- [+] Checking validator.php
- [+] Checking robots.txt existing
- [+] Checking c99 xml shell in admincp/subscriptions.php
- [+] Finding common backup files name
- [+] Finding common log files name
- [+] Checking config.php.x for disclure config file
- [+] Checking faq.php RCE backdoor
- [+] Checking vBSEO 3.x – LFI (Local File Inclusion) vulnerability
- [+] Checking vBulletin vBExperience 3 ‘sortorder’ Parameter Cross Site Scripting Vulnerability
- [+] Checking arcade.php SQLI Vulnerability
- [+] Checking vBulletin YUI 2.9.0 XSS
- [+] Checking for html tags status
- [+] Checking Vbulletin 5.x – Remote Code Execution Exploit
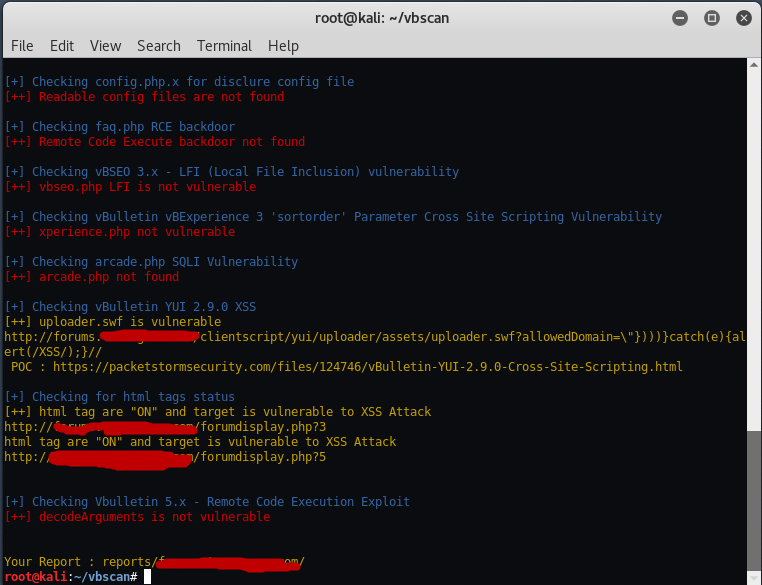
As you can see this tool has fetched all the exploits for the specific vBulletin version. There’s lot of vulnerabilities sites you can search them using dorks and report to admins to patch them.
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- The Intricate Process of Designing and Developing Online Casino Slot Games
- Bella Protocol vs. Traditional Banking: A New Era of Financial Services
- How Does Spam Score Affect SEO?
- Top Email Marketing Applications for Effective Campaigns
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Can Jews and Evangelical Christians Co-Exist?
- What Will Be Digital Information Technology in 2023








