
Cryptography is essentially used for converting plain text into cipher text to ensure confidentiality. If a user has the appropriate key, the cipher text can be reversed to get the original plain text. A message digest or hash is a technique used to verify and assure the integrity of data.
Unlike encryption, a message digest is a one-way function. This means you cannot recover the original data from the hashed data. Using a particular algorithm, if we calculate the message digest of a string, then the message digest will remain unchanged as long as the string remains unchanged. Even the least change, like adding a space or punctuation mark will completely change its corresponding message digest value. The message digest algorithm transforms input of any length into output of fixed length.
Here is the below list which commonly used message digest algorithms along with their respective output strength in bits.
- MD2 = 128 bits (Designed in 1989)
- MD4 = 128 bits (Designed in 1990)
- MD5 = 128 bits (Designed in 1991)
- MD6 = up to 512 bits
- SHA-1 = 160 bits
- SHA-224 = 224 bits
- SHA-256 = 256 bits
- SHA-384 = 384 bits
- Tiger = 192 bits
- Whirlpool = 512 bits
Message digests are widely used in cryptography, digital signatures, and for validating the authenticity of digital evidence. There are many free tools and websites available that help you calculate the message digest of a file or a string. One such website is http://onlinemd5.com/.
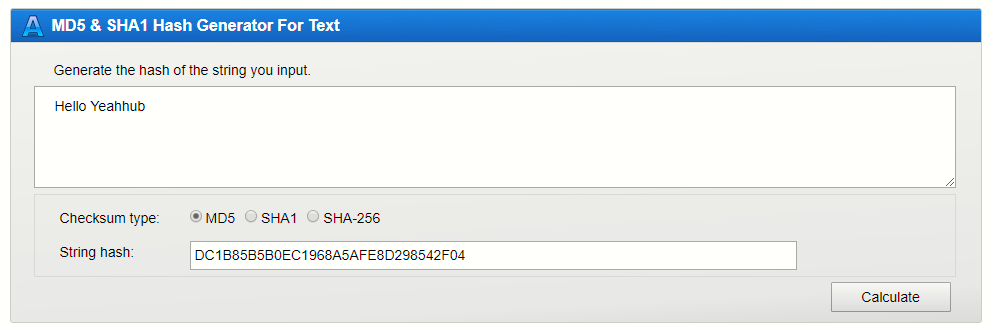
MD5
- Computes 128-bit hash value
- Widely used for file integrity checking
SHA-1
- Computes 160-bit hash value
- NIST approved message digest algorithm
HAVAL
- Computes between 128 and 256 bit hash
- Between 3 and 5 rounds
RIPEMD-160
- Developed in Europe published in 1996
- Patent-free
- Top 7 Commercial Linux Distributions
- Why Do I Need a Website?
- Reinforcement Learning in Real-world Applications: The Latest Successes and Challenges
- Various Python Libraries for developing RESTful APIs
- Top 7 NodeJS Frameworks You Need To Know
- How Buying Instagram Followers Can Help Businesses Soar
- How To Find Gaps In Your Cybersecurity And How To Address Them
- How to close the site from indexing using robots.txt
- Internet Security With VPN – Why Do You Need It
- How to Fix The DLL Missing Error in Windows 7?








