In Greek mythology, Medusa was a monster, a Gorgon, generally described as a winged human female with living venomous snakes in place of hair.
Medusa is a speedy, parallel, and modular, login brute-forcer. The goal is to support as many services which allow remote authentication as possible.
Download Link – http://www.foofus.net/jmk/tools/medusa-2.0.tar.gz
The author considers following items as some of the key features of this application:
- Thread-based parallel testing. Brute-force testing can be performed against multiple hosts, users or passwords concurrently.
- Flexible user input. Target information (host/user/password) can be specified in a variety of ways. For example, each item can be either a single entry or a file containing multiple entries. Additionally, a combination file format allows the user to refine their target listing.
- Modular design. Each service module exists as an independent .mod file. This means that no modifications are necessary to the core application in order to extend the supported list of services for brute-forcing.
- Multiple protocols supported. Many services are currently supported (e.g. SMB, HTTP, POP3, MS-SQL, SSHv2, among others).
Also Read: Bruteforce SSH Using Hydra, Ncrack And Medusa – Kali Linux 2017
Medusa tool is already pre-installed in every Kali Linux version which you can easily use by typing “medusa” from your Linux terminal.
Syntax: medusa -h

Case: In our VM, metasploitable2 machine is installed and running whose IP is 192.168.36.132.
As we all knows the username of Metasploitable2 machine is “msfadmin” and a SSH service is already open in that machine so to crack the password of this VM machine, type the below command in your terminal:
Command: medusa -h 192.168.36.132 -u medusa -P /root/dictionary.txt -M ssh -n 22
Where -h = defines your target hostname,
-u = defines username,
-P = a dictionary file,
-M = the module to execute like SSH, FTP etc,
-n = port number wrt to module

Most Popular Passwords –
| Rank | Password | Number of Instances |
| 1 | 123456 | 290,731 |
| 2 | 12345 | 79,078 |
| 3 | 123456789 | 76,790 |
| 4 | Password | 61,958 |
| 5 | iloveyou | 51,622 |
| 6 | princess | 35,231 |
| 7 | rockyou | 22,588 |
| 8 | 1234567 | 21,726 |
| 9 | 12345678 | 20,553 |
| 10 | abc123 | 17,542 |
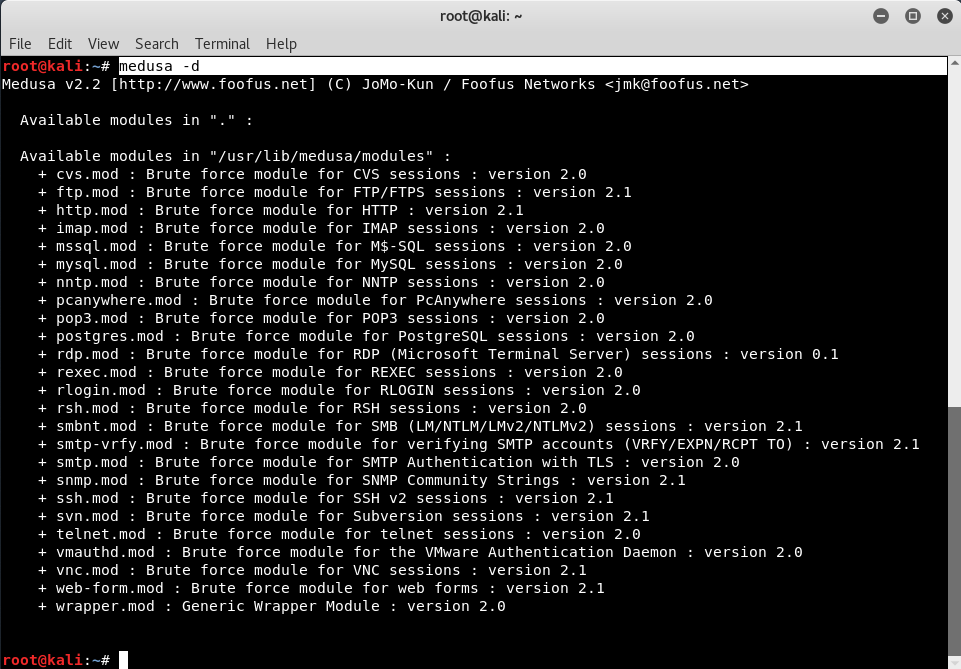
To display all service modules, type “medusa -d”