
Footprinting is the process of collecting as much information as possible about a target network, for identifying various ways to intrude into an organization’s network system.
Out of the many useful auxiliary modules that metasploit has, one is called search_email_collector which searches Google, Bing and Yahoo for email addresses associated to a particular domain.
Email harvesting is the process of obtaining lists of email addresses using various methods. You can check on your own what emails, attackers are going to find about your domain using Metasploit’s module, Search Engine Domain Email Address Collector. This module uses Google, Bing and Yahoo to create a list of valid email addresses for the target domain. This is useful in automated information gathering during a penetration test program.
The module name is “auxiliary/gather/search_email_collector“, this is the one we are going to use.
Command: use auxiliary/gather/search_email_collector
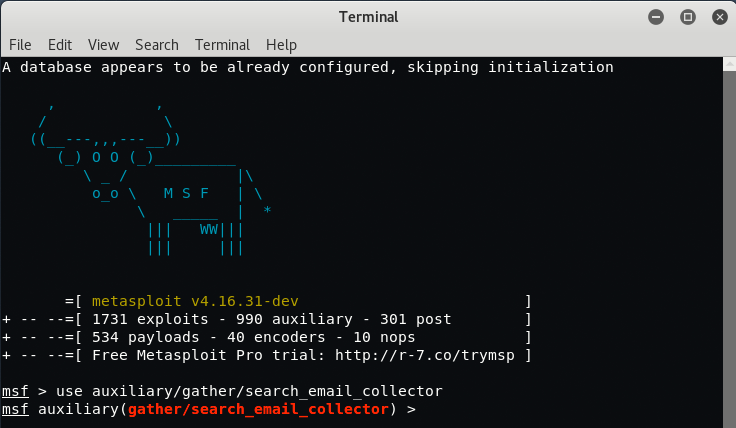
By typing “show options“, you’ll be able to see that options which this module required and out of all options, the most important is to set the domain parameter.
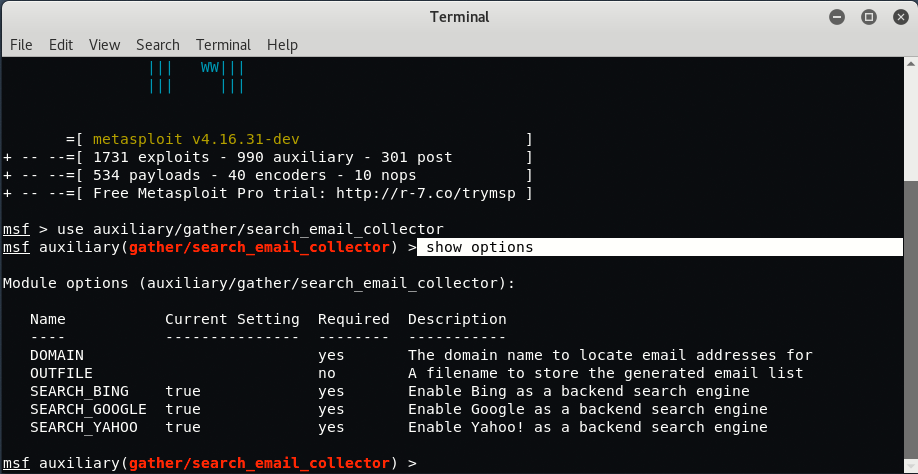
To set the domain parameter, type “set DOMAIN <domain name>” and run the scanner.
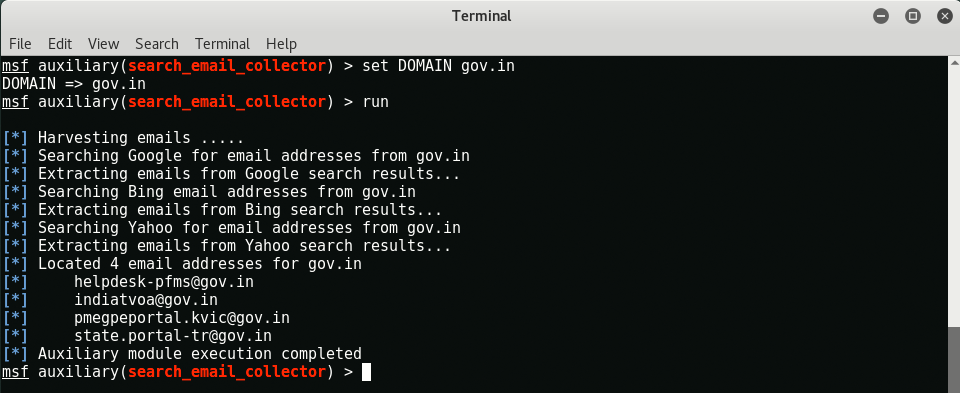
By default google, Bing and yahoo all 3 are selected for email harvesting. Email harvesting can be used by hackers to carry out a phishing campaign against an entire organisation.
This is one aspect of how emails can be misused. Computer users, who are often unaware of phishing attacks can fall victim and end up loosing confidential information to the hackers or getting their system’s compromised. In the worst case, if a hacker gets control of a single machine inside an organisations network, it might open for him the path to access and exploit the entire network of the organisation.
You can also use “theharvester” tool for email harvesting.








