
OWASP means The Open Web Application Security Project is a worldwide free and open community focused on improving the security of application software. Their mission is to make application security “Visible” so that people and organizations can make informed decisions about their risks.
OWASP is a non-profit chartiable organization that ensures the ongoing availability and support for their work.
Recently they just published the “Release Candidate” Version but by the mid of 2017, they will soon release 3 more versions i.e. “Alpha Version“, “Beta Version” and “Release Version“.
- Alpha Version is the draft version and is very rough in nature.
- Beta Version is the next highest level.
- Release Version is the final version which maintains quality in books title’s lifecycle.
At OWASP you’ll find:
- Application security tools and standards
- Complete books on application security testing, secure code development, and secure code review
- Standard security controls and libraries
- Local chapters worldwide
- Cutting edge research
- Extensive conferences worldwide
- Mailing lists
The goal of the Top 10 project is to raise awareness about application security by identifying some of the most critical risks facing organizations. The Top 10 project is referenced by many standards, books, tools, and organizations, including MITRE, PCI DSS, DISA, FTC, and many more.
The OWASP Top 10 was first released in 2003, with minor updates in 2004 and 2007. The 2010 version was revamped to prioritize by risk, not just prevalence, and this pattern was continued in 2013 and now they released the latest update after following 2013 is Owasp Top 10 – 2017.
You must use this “OWASP Top 10” to protect your application from secuirty risks. Developers always learn from their mistakes. Executives should start thinking about how to manage the risk that software applications and APIs create in their enterprise.
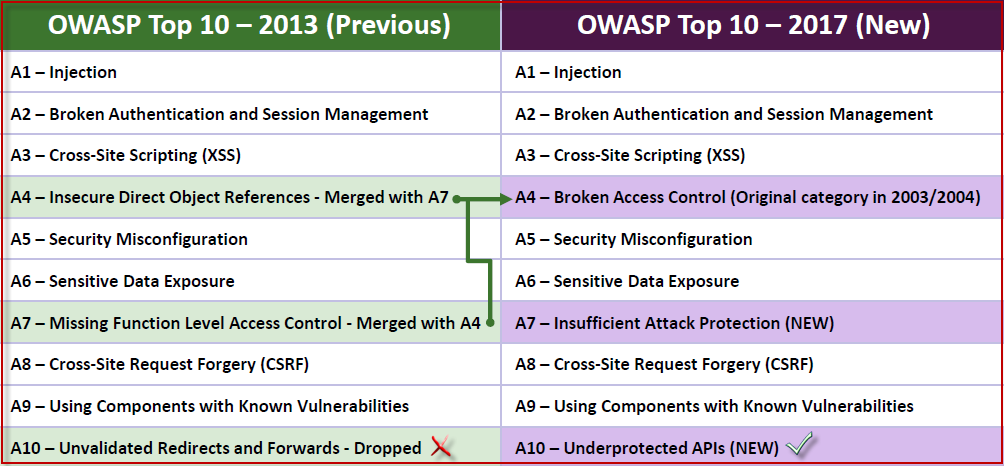
In OWASP 2017 Update, they’ve added two major vulnerabilities:
- Insufficient Attack Detection and Prevention which is on Number – A7
- Underprotected APIs which is on Number – A10
Besides that they’ve merged two points from OWASP 2013 i.e. for A4 + A7 is now replaced with Broken Access Control and for OWASP-Top10(2013)(Unvalidated Redirects and Forwards) A10 point is dropped and replaced with “Underprotected APIs”
The Top 10 items are selected and prioritized according to this prevalence data, in combination with consensus estimates of exploitability, detectability, and impact.
But there are 100s of issues that could affect the overall security of a web application and for this you can follow this Web Application Security Checklist.
In this 2017 release, they made the following changes:
- Merged 2013-A4: Insecure Direct Object References and 2013-A7: Missing Function Level Access Control back into 2017-A4:
Broken Access Control. In 2007, they’ve split Broken Access Control into these two categories to bring more attention to each half of the access control problem (data and functionality) - Added 2017-A7: Insufficient Attack Protection:
Based on the data call, the majority of applications and APIs lack basic capabilities to detect, prevent, and respond to both manual and automated attacks. Application and API owners also need to be able to deploy patches quickly to protect against attacks. - Added 2017-A10: Underprotected APIs:
Modern applications and APIs often involve rich client applications, such as JavaScript in the browser and mobile apps, that connect to an API of some kind (SOAP/XML, REST/JSON, RPC, GWT, etc.). These APIs are often unprotected and contain numerous vulnerabilities. - Dropped: 2013-A10: Unvalidated Redirects and Forwards:
In 2010, they added this category to raise awareness of this problem. However, the data shows that this issue isn’t as prevalent as expected. So after being in the last two releases of the Top 10, this time it didn’t make the cut.

Here is the complete list of OWASP top 10 from A1 to A10 for 2017 release.
- A1 – Injection
- A2 – Broken Authentication and Session Management
- A3 – Cross-Site Scripting
- A4 – Broken Access Control (*New)
- A5 – Security Misconfiguration
- A6 – Sensitive Data Exposure
- A7 – Insufficient Attack Protection (*New)
- A8 – Cross-Site Request Forgery
- A9 – Using Components with Known Vulnerabilities
- A10 – Underprotected APIs (*New)
- Top 7 Commercial Linux Distributions
- Why Do I Need a Website?
- Reinforcement Learning in Real-world Applications: The Latest Successes and Challenges
- Various Python Libraries for developing RESTful APIs
- Top 7 NodeJS Frameworks You Need To Know
- How Buying Instagram Followers Can Help Businesses Soar
- How To Find Gaps In Your Cybersecurity And How To Address Them
- How to close the site from indexing using robots.txt
- Internet Security With VPN – Why Do You Need It
- How to Fix The DLL Missing Error in Windows 7?








