
Even though news about another celebrity’s hacked cloud storage – from Jennifer Lawrence to Hilary Clinton – appear regularly, many people think their personal information is not attractive to cyber criminals. However, practice…
Read more
So, you have decided to buy cryptocurrency with debit card online and have no idea how to do that. This review is going to help you out. If you were looking for a…
Read more
Do you want to make money online but avoid getting ripped off? So here are the best 7 legit ways to earn money online as mentioned below: Cinstaller – Cinstaller is a great…
Read more
Wireless Networks have become ubiquitous in today’s world. Millions of people use it worldwide every day at their homes, offices and public hotspots to logon to the Internet and do both personal and…
Read more
Have you ever thought about setting up a business online? If not, where have you been for the last 5 or 10 years? It’s the new American dream, encompassing all the usual ideas…
Read more
SEO (Search Engine Optimization) is the activity of optimizing Web pages or whole sites in order to make them more search engine friendly, thus getting higher positions in search results. SEO is sometimes…
Read more
Python is an interpreted, object-oriented, high-level programming language. Python can be ran on almost any OS. While it is not native to Windows machines, it is native to most Linux distributions. The great…
Read more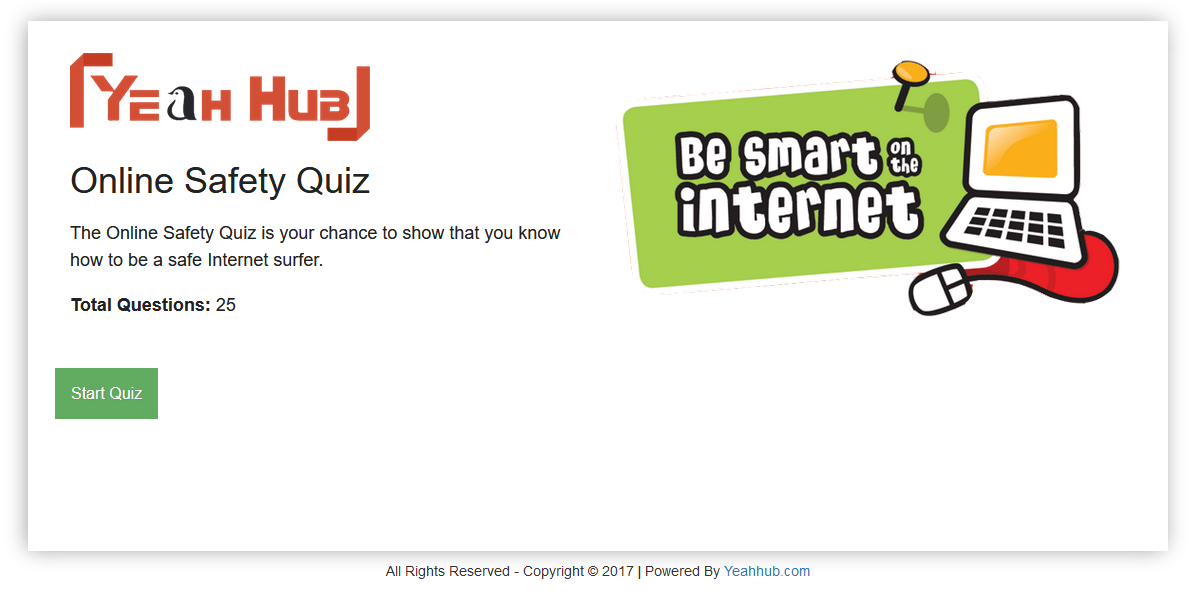
Part of Safer Internet Day, this Online Quiz invites children, young people, parents, grandparents and teachers to create a better internet together by exploring what to do in different situations that may arise…
Read more
With the help of ready made vulnerable applications, you actually get a good enhancement of your skills because it provides you an environment where you can break and hack legally allowing you to…
Read more
Before to starting, we’ll setup a virtual pentesting lab with the help of Web For Pentester toolkit which is totally based on Debian OS. As you all knows most of the web applications…
Read more
Well with the help of honeypot, you can easily monitor your own OS and can track every activity of the hacker or you can say that, its the best way to hack the…
Read more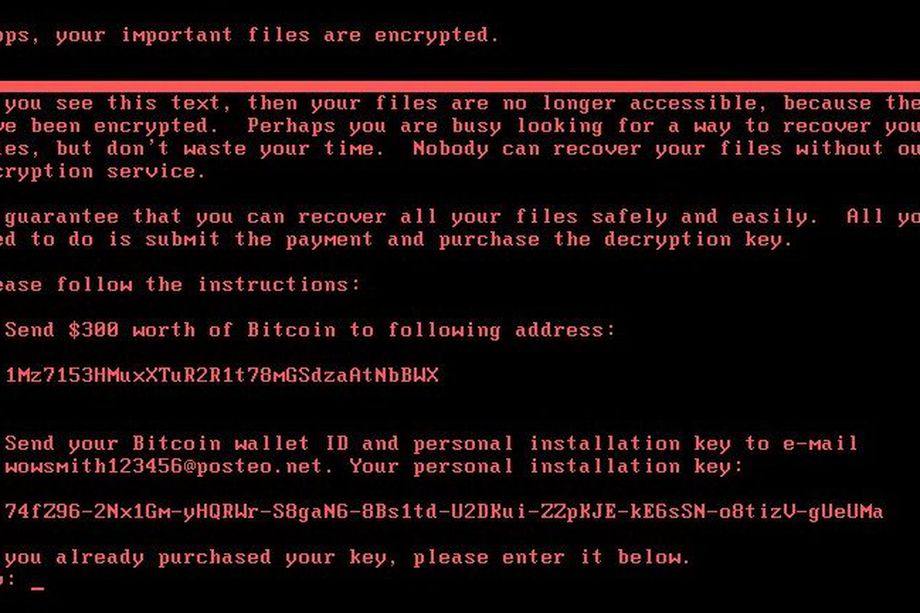
As you all knows, recently Petya Ransomware comes into existence and affected more than 65+ countries. Many organizations in Europe and the US have been affected by this ransomware attack. Although its not…
Read more
As you all knows Wannacry or Wcry Ransomware already created a havoc across the globe and now within the span of just 2 months, a new ransomware named as Petya Ransomware hits globally…
Read more
Google is clearly the best general-purpose search engine on the Web. But most people don’t use it to its best advantage. Do you just plug in a keyword or two and hope for…
Read more
Microsoft has just announced “Visual Studio Dev Essentials” and here’s the really awesome bit: If you sign up through above link which is free ofcourse then you’ll get all of the hidden offers…
Read more
OWASP means The Open Web Application Security Project is a worldwide free and open community focused on improving the security of application software. Their mission is to make application security “Visible” so that…
Read more
Step 20 – Once you have a handshake captured (see the WPA Handshake: [MAC Address] on top in previous article, if it’s there, then you have the handshake), then type 1 and enter to…
Read more
Step 7 – After running Fluxion by typing this command “sudo ./fluxion“, the first step is to select the language. Currently Fluxion supports 6 languages i.e. German, English, Romanian, Turkish, Spanish and Chinese….
Read more
As you all knows in Wireless Networks, there are so many encryption protocols are there i.e. WEP, WPA and WPA2 and out of that WEP is one of the most weakest protocol which…
Read more
At some point, most web programmers are going to need to learn databases. They’re the premier way to store information in an online environment, and they’re often the most efficient solution. But do…
Read more
One of the defining features of PHP(Hypertext Preprocessor) is the versatility it offers for connection to, and manipulation with databases. In this article, we look at some features of the PHP with MySQL…
Read more
