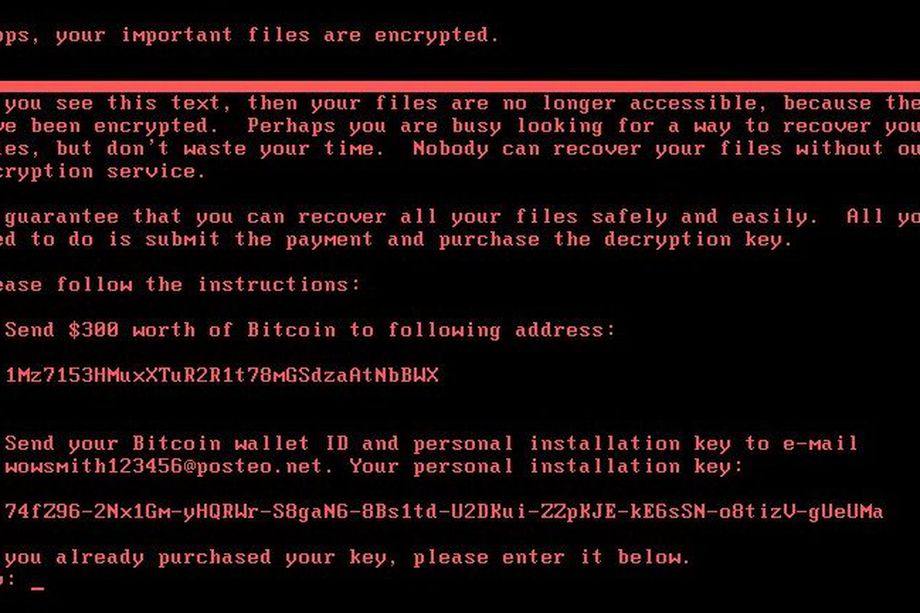
As you all knows, recently Petya Ransomware comes into existence and affected more than 65+ countries. Many organizations in Europe and the US have been affected by this ransomware attack. Although its not a ransomware attack but its a wiper attack which directly attacks your operating system files.
– Global shipping company “Maersk” was also taken down by this Petya Ransomware attack by 28th June 2017.
– FedEx’s Dutch operations have been significantly affected by the Petya Worm.
– Some Airlines and Banks were also reported by Petya Ransomware attack.
If you have been infected –
1) Do Not Pay – You will not only be financing criminals, but it is unlikely that you will regain access to your files. This is particularly relevant in the case of Petya, as the email account used to manage ransom demands has been blocked, thus disabling attacker’s access to the only communication channel known at the moment.
Read More: 3 Bitcoin Addresses has been identified – Ransomware Attack 12 May 2017
2) Report it to your national police or cyber cell – Make sure that you keep a copy of the phishing email received from the attackers and provide it to the police. This will help law enforcement with their investigation.
Read More: You can also register your complaint at IC3 portal.
3) Disconnect the infected device from the internet – If the infected device is part of a network, try to isolate it as soon as possible, in order to prevent the infection from spreading to other machines. You can then format the hard drive, reinstall the OS and apps, run any available updates, and finally, restore the locked files from your back-up drive.

If you have not been infected –
1) Keep all apps and OS up to date – Making sure that you install all Microsoft patches as soon as they are made available. If the device offers the option of automatic updates, take it.
Read More: To know more about Microsoft Security Updates.
2) Back-up your data – Even if you are affected by ransomware, you can easily retrieve your files. It is best to create two back-up copies: one to be stored in the cloud and one to store physically.
For complete backup of your system, you can either use external Hard drive/Thumb drive or you can also save your data on CLOUD such as One drive or Dropbox. Cloud backups are easy to create and maintain.
3) Use Robust Security Products – To protect your system from all threats, including ransomware.
4) Do not use high privileges accounts – Never use Fully Administrative rights user accounts. Create a local user account and then use it for your daily business.
5) Do not click on attachment or Links that accompany suspicious or unexpected emails, even if they seem to be coming from a trusted party such as a bank or an online store. Trust no one.
You may also like:- Top 7 Commercial Linux Distributions
- Why Do I Need a Website?
- Reinforcement Learning in Real-world Applications: The Latest Successes and Challenges
- Various Python Libraries for developing RESTful APIs
- Top 7 NodeJS Frameworks You Need To Know
- How Buying Instagram Followers Can Help Businesses Soar
- How To Find Gaps In Your Cybersecurity And How To Address Them
- How to close the site from indexing using robots.txt
- Internet Security With VPN – Why Do You Need It
- How to Fix The DLL Missing Error in Windows 7?








