Step 20 – Once you have a handshake captured (see the WPA Handshake: [MAC Address] on top in previous article, if it’s there, then you have the handshake), then type 1 and enter to check the handshake. If everything’s fine,
you’ll go to the next step.
For best way, always choose “Web Interface” method. Because by selecting “Bruteforce” simply means trying to attack via a pre-saved dictionary list where chances are very less to get the key.

Step 21 – Here you need to select the login page design/language. If you are targeting in a public area, then we always recommend you to select the “English” one by typing Number “1“.
This offers a variety of login pages that you can use to phish the network’s password.

Step 22 – After making your decision, you’ll see multiple windows. DHCP and DNS requests are being handled in
left two windows, while the right two are status reporting window and deauth window.
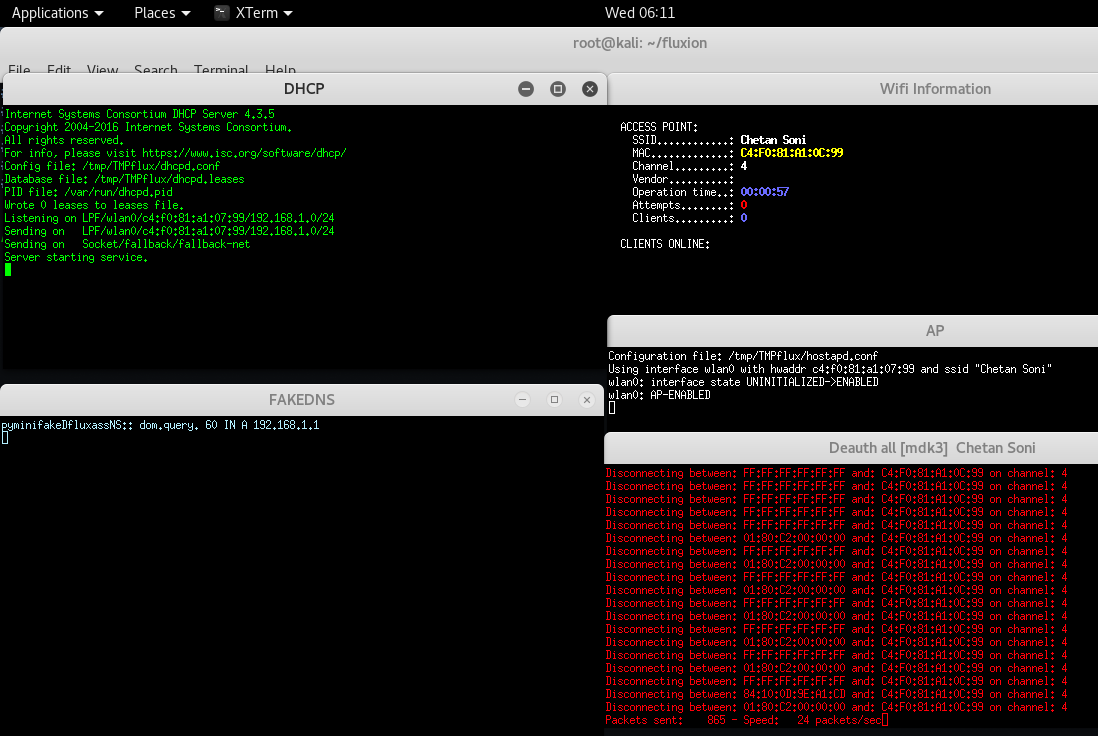
Step 23 – In other side, you can see two networks with same name, but the difference is that one is having security which is real network and other is a fake network without security which we created from this fluxion tool.

Step 24 – So basically the complete scenario is, the user who is using that wireless network named as “Chetan Soni” got disconnected due to deauthentication which is running in above step and he is continuously trying to connect but mistakenly he got connected with ours fake network.

Step 25 – In below screen, as soon as he connected with Fake AP named as “Chetan Soni“, a DHCP service will automatically gets into action and opens a Phishing Link in user’s browser.

Step 26 – After connecting to the network, the user got a notification saying that “Sign in to Network“.
As soon as the user enters his original wi-fi password into that fake login page, the script ran the password against the handshake we had captured earlier to verify if it is indeed correct.
Note how the handshake is a luxury, not a necessity in this method. It just ensures that we can verify if the password submitted by the fake AP client is correct or not.
If we don’t have the handshake, then we lose this ability, but assuming the client will type the correct password, we can still make the attack work.

Step 27 – If user filled correct password, then it display a message i.e. “Your connection will be restored in a few moments.“.

Step 28 – WOHOOOO, we got the key in a clear text format.

If your fake AP has more signal strength than the real one, then a person who doesn’t know about WPA or WPA2 and open networks could very easily end up connecting to your network instead. So, overall this attack has a fair chance of succeeding.
For any kind of doubt/query/help, feel free to mail at yeahhub@gmail.com
Back to Fluxion – Part 1……….
Back to Fluxion – Part 2……….
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times









FYI: this is old, fluxion is now here: https://github.com/FluxionNetwork/fluxion