Microsoft recently fixed RCE (Remote Code Execution) Vulnerability in CredSSP in March Updates of Windows. CredSSP (Credential Security Support Provider Protocol) is a security protocol that lets applications delegate user’s NTLM or kerbros credentials from clients to servers for remote authentication over TLS channel.
This vulnerability could allow a MITM attack where user credentials are relayed and used to run code on the remote system against an RDP session.
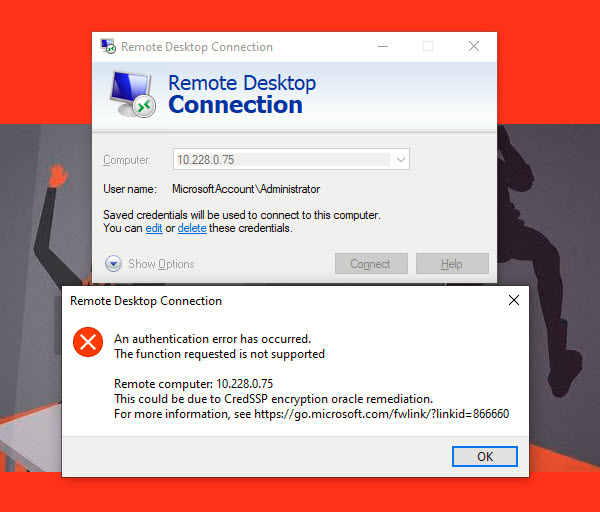
In recent update, Windows 10 users are facing the following CredSSP error due to a vulnerability that allows an attacker to run arbitrary code execution against an running RDP Session.
According to Microsoft – “Mitigation consists of installing the update on all eligible client and server operating systems and then using included Group Policy settings or registry-based equivalents to manage the setting options on the client and server computers. We recommend that administrators apply the policy and set it to “Force updated clients” or Mitigated on client and server computers as soon as possible. These changes will require a reboot of the affected systems.”
This vulnerability has been fixed in latest update of Windows but many users are facing the above error while logging into remote system using RDP. This is because, either your OS has not updated to latest or the system that the user intends to connect is not fully updated which reflects the CredSSP error and displays a message to the user “An authentication error has occurred. The function requested is not supported. This could be due to CredSSP encryption oracle remediation.”
With Local Group Policy Editor, you can easily fix this error. Open the Group Policy Editor by typing “gpedit.msc” in your RUN command.
Navigate to “Administrative Templates” -> “System” -> “Credentials Delegation” under Computer Configuration.
Right click on “Encryption Oracle Remediation” settings and choose EDIT.
Now choose “Enabled” button and choose the protection level to “Vulnerable” as shown below:
Click Apply and then OK to fix CredSSP Encryption Oracle Remediation Error. Once you apply above changes, your RDP will work properly without any error.
Encryption Oracle Remediation policy offers 3 available values to protect against CredSSP vulnerability: Force
- Updated Clients – the highest protection level when the RDP server blocks the connection from non-patched clients. Usually, this policy should be enabled after you have completely updated the entire infrastructure and added the latest security updates to the Windows install images for servers and workstations.
- Mitigated – in this mode, an outgoing remote RDP connection to RDP servers with a vulnerable version of CredSSP is blocked. However, other services using CredSSP work fin.
- Vulnerable – the lowest level of protection when connecting to an RDP server with a vulnerable version of CredSSP is allowed.
In case, if you don’t have Group Policy Editor (In case of Windows 10 Home Editions), then the same can be done with the help of Registry Editor that allows RDP connection to servers with unpatched version of CredSSP.
Step 1 – Press WIN+R keys together to launch RUN dialog box. Now type regedit and press Enter. It’ll open Registry Editor.
Step 2 – Now go to following key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
Step 3 – Create a new key under System key and set its name as CredSSP
Step 4 – Create another new key under CredSSP key and set its name as Parameters
Step 5 – Now select Parameters key and in right-side pane create a new DWORD AllowEncryptionOracle and set its value to 2.
Restart your computer to take effect.
Furthermore, if you update your windows in both level i.e. at Client Side and at Server level, then this error will go away. All third-party clients or servers must use the latest version of the CredSSP protocol. Please contact the vendors to determine if their software is compatible with the latest CredSSP protocol.
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times
- [Metasploit] Upgrading Normal Command Shell to Meterpreter Shell