A network is compromised of systems with addresses and on those systems you have services. That address is called an “IP Address” and the Service could be many things but is basically software that is running on the system and accessible over the network on a port number.
Here are some common ports that you will find when using port scanning:
- Port 21 – FTP (File Transfer Protocol)
- Port 22 – SSH (Secure Shell)
- Port 23 – Telnet
- Port 25 – SMTP (Simple Mail Transfer Protocol)
- Port 53 – DNS (Domain Name Server)
- Port 80 – HTTP (Hyper Text Transfer Protocol)
- Port 110 – POP3 (Post Office Protocol)
- Port 143 – IMAP (Internet Message Access Protocol)
- Port 443 – HTTPS (Secure Hyper Text Transfer Protocol)
Port Facts –
- The ports 0 to 1023 belong to the standardised ports, which the Internet Assigned Numbers Authority (IANA) are mostly responsible for assigning.
- The port numbers 1024 to 49151 are reserved for registered services by default. However, these are also assigned to client programs, especially when it comes to Linux systems.
- The ports 49152 to 65535 dynamically assign operating systems to clients.
There are so many port scanning tools are available but you can also use the following Linux commands to scan open ports against any target machine.
An open port is one that has allowed a full three way TCP connection to be established. The port scanner in this case has found a port that responded as available to the scan and the connection was established. Secondary data from an open port is known as a banner, this is a text response that includes the type and sometimes version of the server listening.
[#1] Scanning open ports using ss command –
The ss command works like any command on the Linux platform. The ss command is used to dump socket statistics and displays information in similar fashion (although simpler and faster) to netstat as explained below.
The ss command can also display even more TCP and state information than most other tools like netstat or lsof.
To display listening TCP Connections using ss, the command is:
Command: ss -tl
Where, t stands for TCP port and l stands for listening sockets.
To display listening UDP Connections, the command is:
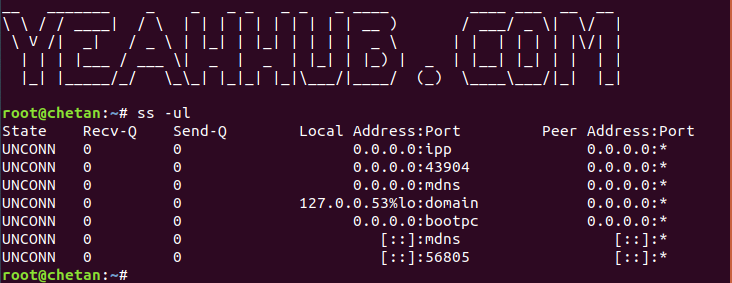
Command: ss -ul
Where u stands for UDP port.
And in case, if you want to display both TCP and UDP connections, the command is:
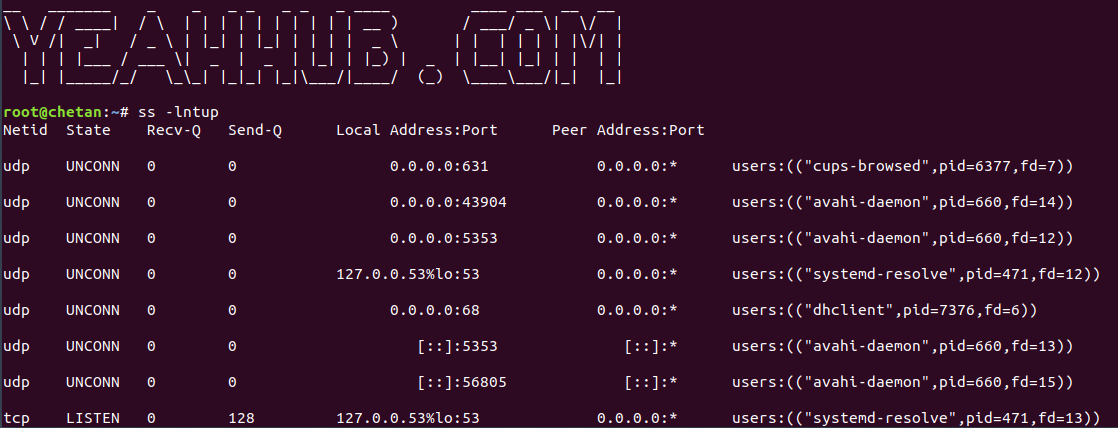
Command: ss -lntup
Where p stands for process name
If you want to display all socket connections, then you can simply use ss command.
[#2] Scanning open ports using netstat –
Netstat, derived from the words network and statistics is a program that’s controlled via commands issued in the command line.
It delivers basic statistics on all network activities and informs users on which ports and addresses the corresponding connections (TCP, UDP) are running and which ports are open for tasks.
To check all open ports with netstat, the command is:
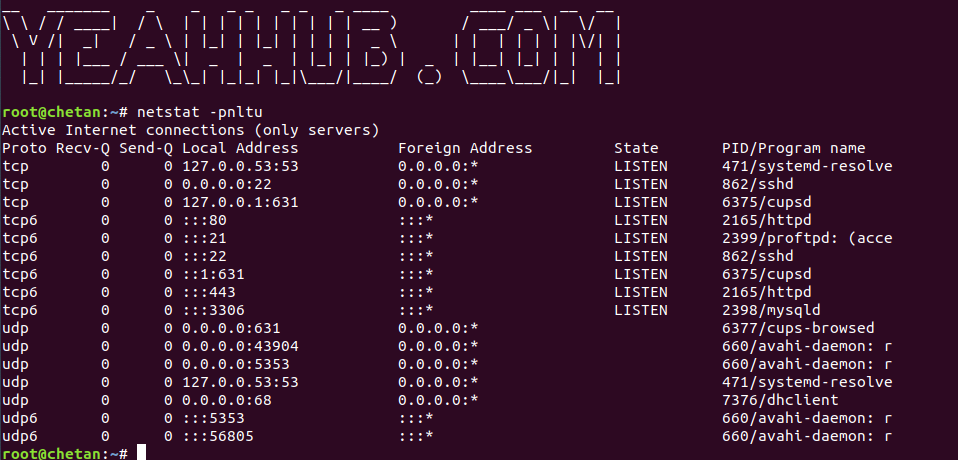
Command: netstat -pnltu
Where p stands for process ID associated with service, n stands for numerical no. of the port running, l stands for listening sockets, t stands for TCP connection and u stands for UDP connection.
In Windows operating systems, you can use the netstat services via the command line (cmd.exe).
[#3] Scanning open ports using lsof command –
lsof is a command line utility for all Unix and Linux like operating systems to check “list of open files”.
lsof command is mainly used to retrieve information about files that are opened by various processes. Open files in a system can be of different type like disk files, network sockets, named pipes and devices.
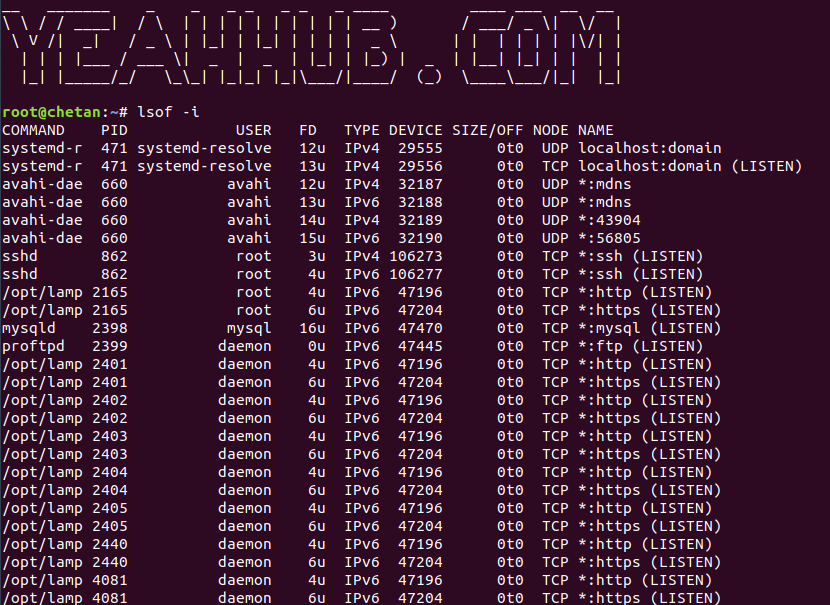
To display open ports, type the following command:
Command: lsof -i
And in case if you want to display only open sockets, then you can use:
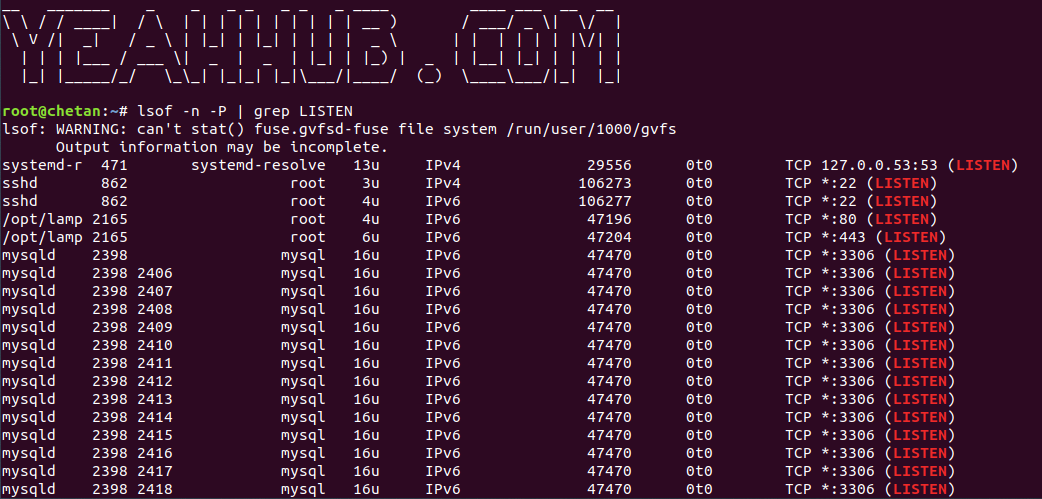
Command: lsof -n -P | grep LISTEN
To display only TCP connections, type:
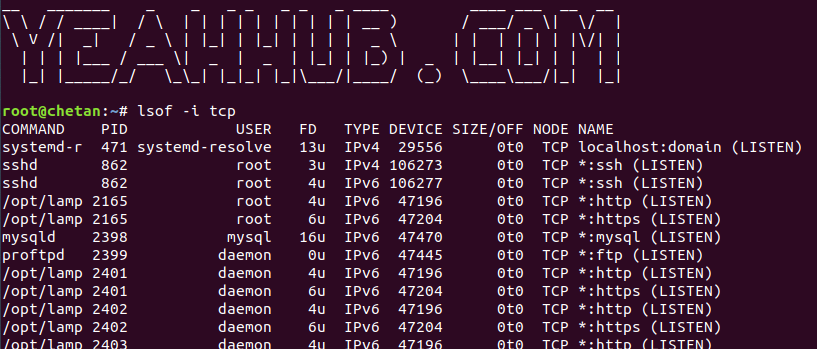
Command: lsof -i tcp
[#4] Scanning open ports using Nmap –
Nmap is one of the free, opensource network security scanner, usually used for network discovery and security auditing. Among other thing, you can also use NMAP for scanning open ports, monitor hosts and network inventory purposes.
In Kali Linux, Nmap is already pre-installed in it but in case of Ubuntu or any other Linux distro, you can install nmap by typing “sudo apt install nmap” command.
For Windows OS, the Nmap installation package comes with a front-end GUI for Nmap called Zenmap, used to control Nmap from a user interface rather than a command-line.
Suggested Read:
- Top 30 Basic NMAP Commands for Beginners
- Top 10 NMAP Widely Used Commands
- 5 Most Commonly Used Nmap Commands
- 19 Useful NMAP Commands You Should Know
- Save Nmap Output to a File with 4 different ways
To scan for open TCP ports, type:
Command: nmap -sT -O localhost
The above command will initiate a TCP connect scan against the target host. A TCP connect scan is the default scan performed if a TCP SYN scan is not possible. This type of scan requests that the underlying operating system try to connect with the target host/port using the ‘connect’ system call.
And for UDP, the command is:
Command: nmap -sU localhost
The above command will initiate a UDP port scan against the target host. A UDP scan sends a UDP packet to the target port(s). If a response is received, the port is classified as Open. If no response is received after multiple transmissions, the port is classified as open/filtered.
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Top 10 Dangerous Viruses of all times
- [Metasploit] Upgrading Normal Command Shell to Meterpreter Shell