One may be curious to understand how the network intruder to know what ports are open on a computer? Or maybe how they detect which services are running in the system that too without any prior permission from the network administrator.
Well, anyone can do this stuff and even more than that with the help of Nmap tool which is one of the best Port Scanner used by many experts in network security, network researchers and administrators.
Suggested Read: 19 Useful NMAP Commands You Should Know
There are plenty of scanning techniques that can be used in Nmap. This article is intended to provide a the basic overview on top 10 Nmap scanning techniques.
- TCP Connect Scan (-sT)
- TCP SYN Scan (-sS)
- Version Detection (-sV)
- UDP Scan (-sU)
- OS Fingerprinting (-O)
- Scan OS Information (-A)
- Scan Top Ports (-F)
- Scan Targets from a File (-iL)
- TCP ACK Scan (-sA)
- Ping Scan (-sP)
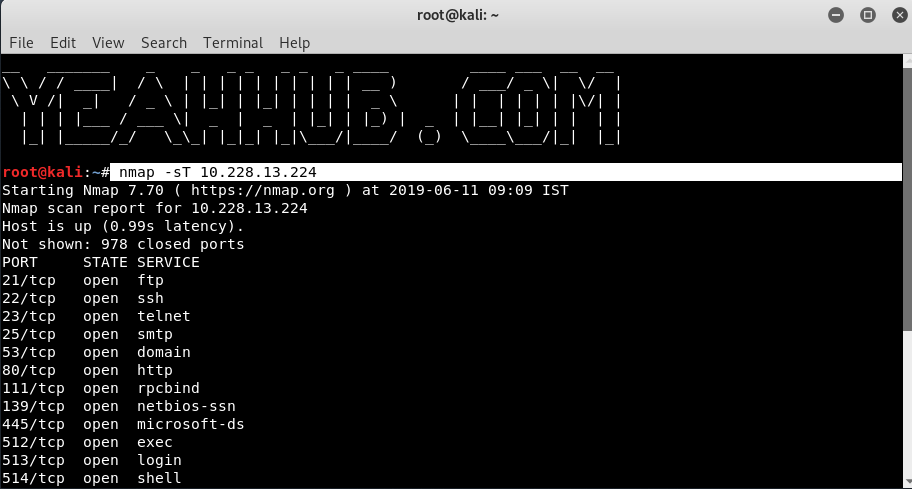
[#1] – TCP Connect Port Scan
Syntax: nmap -sT <IP Address>
TCP connect scan is the default TCP scan type when SYN scan is not an option. This is the case when a user does not have raw packet privileges or is scanning IPv6 networks.
The TCP Connect Scan is a simple probe that attempts to directly connect to the remote system without using any stealth
[#2] – TCP SYN Port Scan
Syntax: nmap -sS <IP Address>
This type of scan won’t establish a TCP connection. It will scan by sending a SYN flag packet and if the port is open, then a SYN/ACK will be send back as a response by the target machine, thus result in a half embryo connection.
Since a full connection wont establish, the connection info will not be logged by the Firewalls/IDSs and hence it is widely known as Stealth scan. If a RST pack is received as a response, then probably the post is closed.
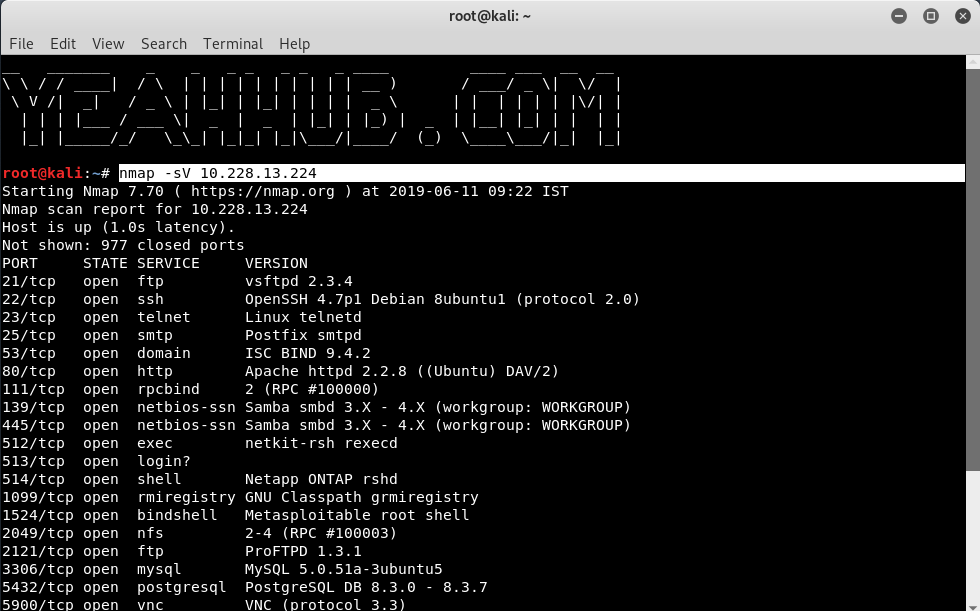
[#3]- Version Scan
Syntax: nmap -sV <IP Address>
Version Detection collects information about the specific service running on an open port, including the product name and version number.
This information can be used in determining an entry point for an attack. The -sV option enables version detection, and the -A option enables both OS fingerprinting and version detection
[#4] – UDP Port Scan
Syntax: nmap -sU <IP Address>
UDP scan works by sending a UDP packet to the targeted port. If no response is received, then the port will be considered as Open | filtered.
Filtered because some firewalls wont respond to the blocked UDP ports. If the port is closed, then an ICMP response (ICMP port unreachable error type 3, code 3) will be send by the target device.
[#5] – OS Fingerprinting
Syntax: nmap -O <IP Address>
With -O (Capital O) or –osscan-guess, you can easily detect the target Operating System behind it using TCP/IP stack fingerprinting. Nmap sends a series of TCP and UDP packets to the remote host and examines the responses. After performing dozens of tests, Nmap compares the results to its database and prints out the OS details if there is a match.
[#6] – Scan OS Information
Syntax: nmap -A <IP Address>
With Nmap, you can detect which OS and version is running on the remote host. To enable OS & version detection, script scanning and traceroute, you can use “-A” option with NMAP.
This type of scan uses the ACK flags. Unlike other scans, ACK scan is not used to determine whether the port is Open or Closed.
It is used to map out firewall rule-sets, determining whether they are stateful or not and which ports are filtered. Stateful Firewalls, will respond with a RST packet as the sequence is not in order.
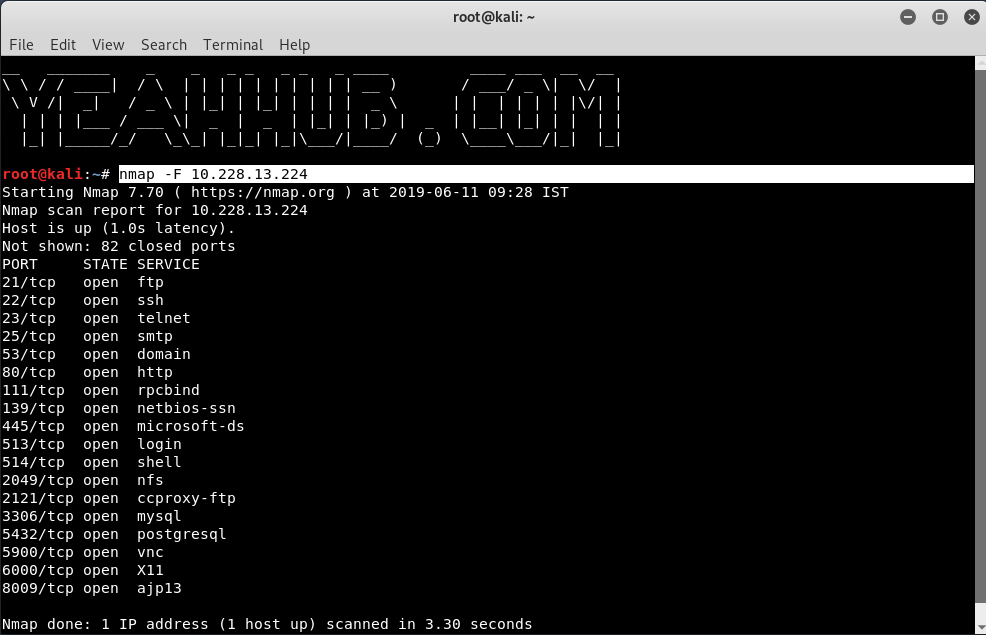
[#7] – Scan Top Ports (Fast Mode)
Syntax: nmap -F <IP Address>
Instead of scanning as many ports as the default scan does, the fast scan only scans a few.
Using “–top-ports” parameter along with a specific number also lets you scan the top X most common ports for that host.
Example: nmap –top-ports 20 10.228.13.224
[#8] – Scan Targets from a File
Syntax: nmap -iL targets.txt
In this case, Nmap is also useful to read files that contain hosts and IP addresses inside.
[#9] – TCP ACK Port Scan
Syntax: nmap -sA <IP Address>
This type of scan uses the ACK flags. Unlike other scans, ACK scan is not used to determine whether the port is Open or Closed.
It is used to map out firewall rule-sets, determining whether they are stateful or not and which ports are filtered. Stateful Firewalls, will respond with a RST packet as the sequence is not in order.
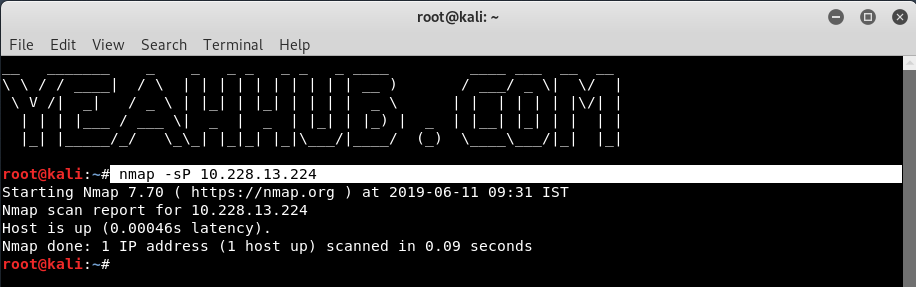
[#10] – Ping Scan
Syntax: nmap -sP <IP Address>
This types of scan is used to detect which computers or devices are online, rather than which ports are open.
In this, Nmap sends an ICMP ECHO REQUEST packet to the destination system. If an ICMP ECHO REPLY is received, the system is considered as up, and ICMP packets are not blocked.
If there is no response to the ICMP ping request, Nmap will try a “TCP Ping”, to determine whether ICMP is blocked, or if the host is really not online.
You may also like:- Top 7 Commercial Linux Distributions
- Why Do I Need a Website?
- Reinforcement Learning in Real-world Applications: The Latest Successes and Challenges
- Various Python Libraries for developing RESTful APIs
- Top 7 NodeJS Frameworks You Need To Know
- How Buying Instagram Followers Can Help Businesses Soar
- How To Find Gaps In Your Cybersecurity And How To Address Them
- How to close the site from indexing using robots.txt
- Internet Security With VPN – Why Do You Need It
- How to Fix The DLL Missing Error in Windows 7?