
One may be curious to understand how the network intruder to know what ports are open on a computer? Or maybe how they detect which services are running in the system that too…
Read more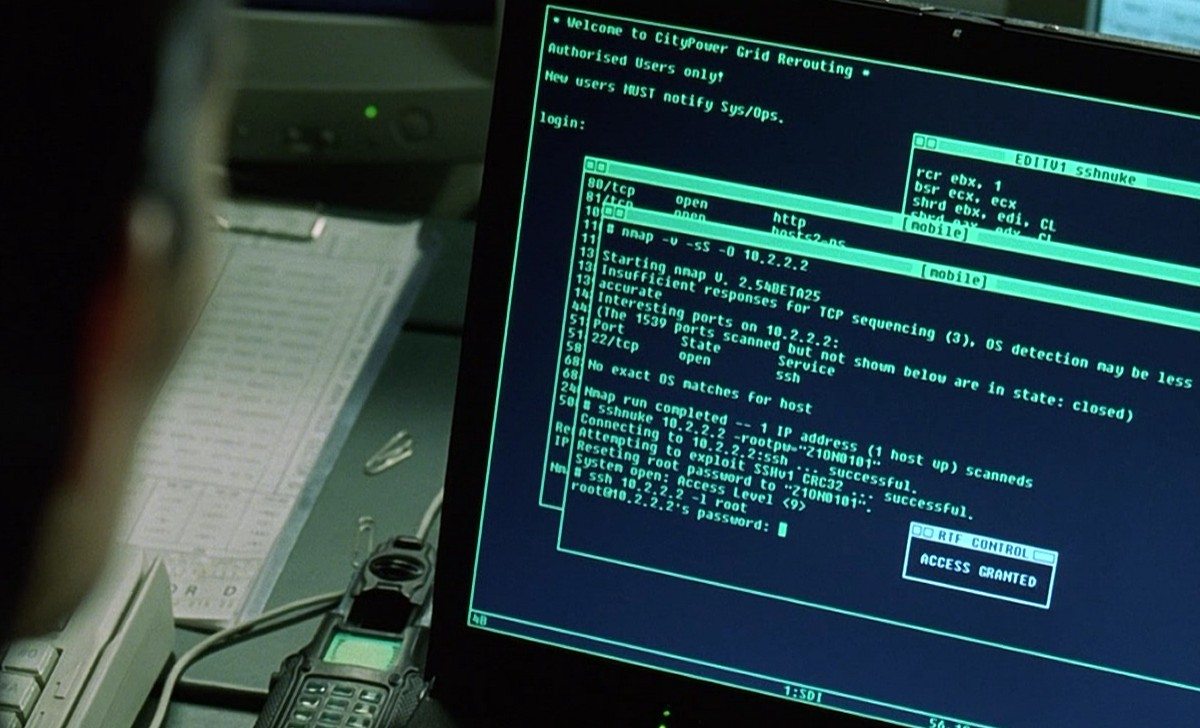
Nmap supports many scanning technologies, such as: UDP, TCP connect(), TCP SYN (half-open scan), ftp proxy (bounce attack), reverse flag, ICMP, FIN, ACK scan, Xmas Tree, SYN Scan and null scan. Nmap also…
Read more
As we come to rely more and more on massively interconnected networks, the stability and security of those networks becomes more vital than ever. The world of business has adopted information technology to help…
Read more
Nmap (Network Mapper) is a security scanner, originally written by Gordon Lyon used to discover hosts and services on a computer network, thus building a “map” of the network. Typical uses of Nmap:…
Read more