
As we come to rely more and more on massively interconnected networks, the stability and security of those networks becomes more vital than ever. The world of business has adopted information technology to help streamline processes, increase productivity, and cut costs.
As such, a company’s IT infrastructure is often a core asset, and many businesses would cease to function if disaster (whether natural or digital) were to significantly disrupt their network operations. At the same time, the widespread adoption of the Internet as a global communications medium has also brought computer networks out of the business and academic world and into our personal lives. That largest of networks is now used not only for information and entertainment, but also as a means to keep in touch with friends, family, and loved ones.
One of the first things you should do after a fresh operating system install is see what services are running and remove any unneeded services from the system startup process. You could use a port scanner i.e. Nmap and run it against the host.
Nmap is the oldest, most popular, and most feature-rich of the three scanners. First released in 1997, it has seen four major releases in the past decade. Nmap is widely available for most Unix platforms as well as Windows, and has both command-line and graphical interfaces. Nmap has been integrated into a number of commercial security products as well.
Also Read: 5 Books considered the “Best Nmap Books Ever Written”
Also, Nmap can also be fooled if the system is using firewall rules. With proper firewall rules, a service can be completely invisible to Nmap unless certain criteria (such as the source IP address) also match. When you have shell access to the server itself, it is usually more efficient to find open ports using programs that were installed with the operating system.
The purpose of network scanning is to identify which IP addresses have computers attached, and which applications are running on those computers.
By default, Nmap displays results of the scan to the terminal, but it is often preferable to save the results to a file for later inspection. This is particularly useful when scanning a large network as the scan output can span tens of pages. Some tools even take Nmap scan files as input, which is yet another reason to save the scan results to a file. Nmap can store the results of its scans in four different formats:
Normal Nmap Output
This is the same format as what is displayed to the terminal during a scan. The only difference is that the command-line options are printed at the top of the file as a reminder of what the scan was configured to do, and some runtime warnings are omitted.
Syntax: nmap -oN </path/filename.txt> <target>
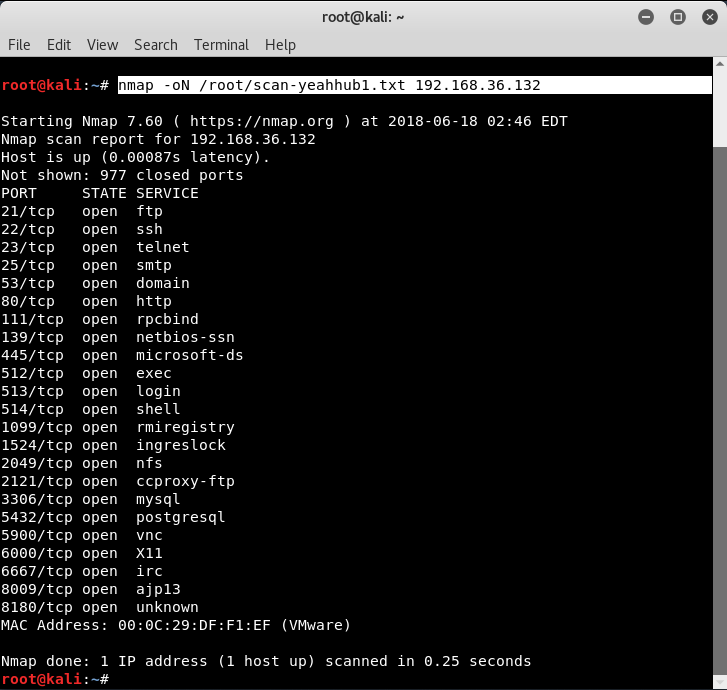
Grepable Nmap Output
This format presents the results with one host per line in a concise fashion, meant to be easily processed with Unix text tools such as grep, sed, awk, and diff. Because of the condensed nature of this format, not all scan output may be preserved this way.
Syntax: nmap -oX </path/filename.xml> <target>
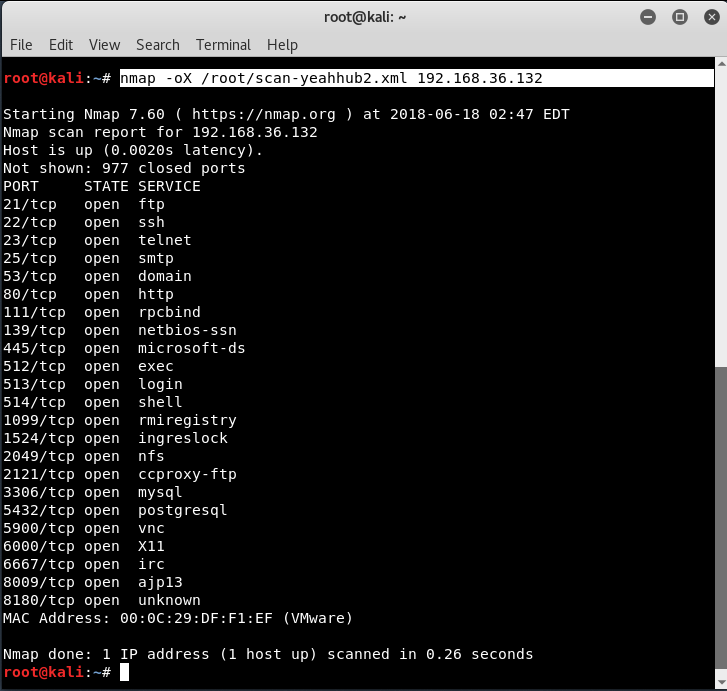
XML Nmap Output
This is the most powerful format, as the entire scan results are represented in highly structured XML for easy parsing by third-party applications. Unlike the Grepable format, all scan output is present in these files.
Syntax: nmap -oG </path/filename.txt> <target>

Script Kiddie Nmap Output
This format is presented solely as a joke and is simply the Normal output passed through a text-mangling filter.
Syntax: nmap -oS </path/filename.txt> <target>

These various output formats can be selected with the -o type filename option, where the type is N, G, X, or S. An additional option, -oA basename, is supported to simultaneously write the scan output in the Normal, Grepable, and XML formats. With this option, the files are named basename.nmap, basename.gnmap, and basename.xml. Multiple output formats can be specified using -o flags as well. For example, to write the output of a scan in normal and XML formats simultaneously, you would type:
You may also like:Syntax: nmap –oN normal_output –oX xml_output target
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








