
Nmap supports many scanning technologies, such as: UDP, TCP connect(), TCP SYN (half-open scan), ftp proxy (bounce attack), reverse flag, ICMP, FIN, ACK scan, Xmas Tree, SYN Scan and null scan.
Nmap also provides some advanced features, such as: detecting operating system types through TCP/IP stack features, secret scanning, dynamic delay and retransmission calculations, parallel scanning, detecting closed hosts by parallel ping scanning, decoy scanning, avoiding Open port filtering detection, direct RPC scanning (no port mapping), fragment scanning, and flexible target and port settings.
nmap always gives the well known port service name (if possible), port number, status, and protocol information. The status of each port is: open, filtered, unfiltered.
- The open state means that the target host can accept connections on this port using the accept() system call.
- The filtered state indicates that firewalls, packet filtering, and other network security software mask this port and prohibit nmap from detecting if it is open.
- Unfiltered means: This port is closed, and there is no firewall/packet filtering software to isolate nmap’s detection attempts.
Normally, the status of a port is basically unfiltered. The port in the unfiltered state is displayed only when most of the scanned ports are in the filtered state.
Suggested Read:
- Save Nmap Output to a File with 4 different ways
- Testing Methods for HTTPS with OpenSSL, Curl and Nmap
- TCP & SYN Scanning with Metasploit Framework without NMAP
- 5 Books Considered the – Best Nmap Books Ever Written
Depending on the functional options used, nmap can also report the following characteristics of the remote host: the operating system used, the TCP sequence, the username of the application running on each port, the DNS name, whether the host address is a spoofed address, and Something else.
Example 1 – Ping Scan
Sometimes you just want to know which hosts are running on the network at this time. Nmap can do this by sending an ICMP echo request packet to each IP address in the network you specify.
It will respond if the host is running. Unfortunately, some sites such as microsoft.com block ICMP echo request packets.
However, by default, nmap can also send TCP ack packets to port 80. If you receive a RST packet, it means the host is running.
The third technique usd by nmap is to send a SYN packet and then wait for an RST or SYN/ACK packet. For non-root users, nmap uses the connect() method.
Command: nmap -sP <Target>

Example 2- Standard Service Detection
This is the command to scan for running service. Nmap contains a database of more than 2000+ well-known services and associated ports.
Command: nmap -sV <Target> -p 1-65535

Example 3 – TCP Syn Scan
Since it is not necessary to open all TCP connections, it is usually called half-open. You can issue a TCP sync packet (SYN) and wait for a response.
- If the other party returns a SYN|ACK (response) packet, it indicates that the target port is listening;
- if the RST packet is returned, it means that the target port has no listener;
- if a SYN|ACK packet is received, the source host will immediately issue a RST (reset).
The packet is disconnected from the target host, which is actually done automatically by our operating system kernel. The biggest benefit of this technology is that few systems can log this into the system log. However, you always need root privileges to customize the SYN packet.
Command: nmap -sS <Target> -p 80

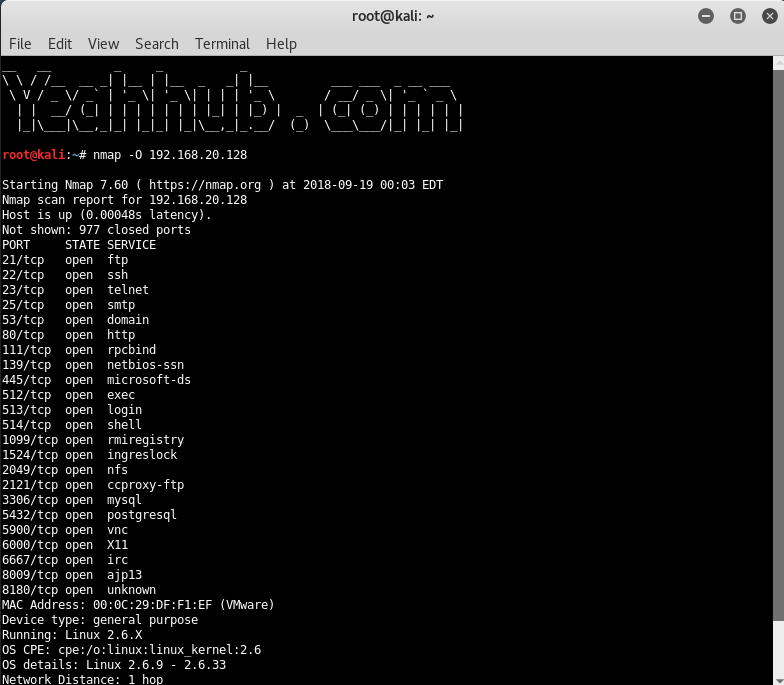
Example 4 – Detect Operating System
This is the command to scan and search for the OS (and the OS version) on a host. This command will provide valuable information for the enumeration phase of your network security assessment.
Command: nmap -O <Target>
Example 5 – Detect OS and Services
Nmap is one of the most popular tools used for the enumeration of a targeted host. Nmap can use scans that provide the OS, version, and service detection for individual or multiple devices.
Detection scans are critical to the enumeration process when conducting penetration testing of a network. It is important to know where vulnerable machines are located on the network so they can be fixed or replaced before they are attacked.
Many attackers will use these scans to figure out what payloads would be most effective on a victim’s device. The OS scan works by using the TCP/IP stack fingerprinting method. The services scan works by using the Nmap-service-probes database to enumerate details of services running on a targeted host.
Command: nmap -A <Target>

- Top 7 Commercial Linux Distributions
- Why Do I Need a Website?
- Reinforcement Learning in Real-world Applications: The Latest Successes and Challenges
- Various Python Libraries for developing RESTful APIs
- Top 7 NodeJS Frameworks You Need To Know
- How Buying Instagram Followers Can Help Businesses Soar
- How To Find Gaps In Your Cybersecurity And How To Address Them
- How to close the site from indexing using robots.txt
- Internet Security With VPN – Why Do You Need It
- How to Fix The DLL Missing Error in Windows 7?








