
One may be curious to understand how the network intruder to know what ports are open on a computer? Or maybe how they detect which services are running in the system that too…
Read more
Nmap is a free tool that can be used to conduct various sorts of scans on networks. Normally, when people think of Nmap, they assume it’s used to conduct some sort of nefarious…
Read more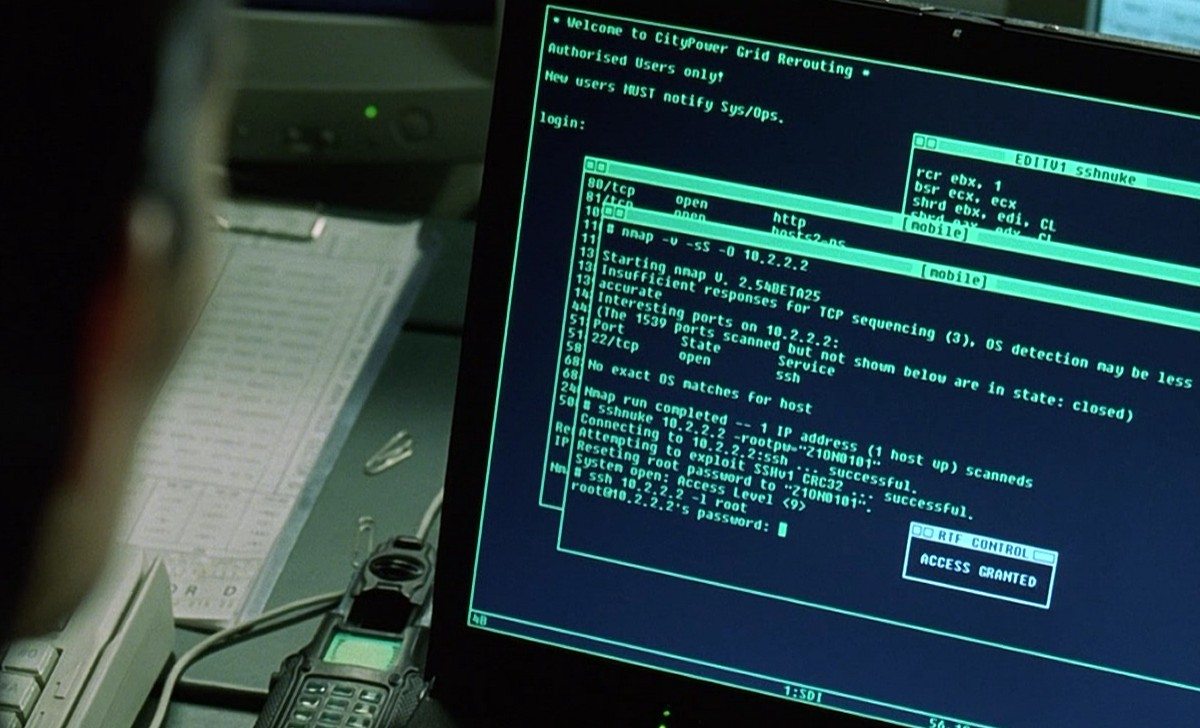
Nmap supports many scanning technologies, such as: UDP, TCP connect(), TCP SYN (half-open scan), ftp proxy (bounce attack), reverse flag, ICMP, FIN, ACK scan, Xmas Tree, SYN Scan and null scan. Nmap also…
Read more