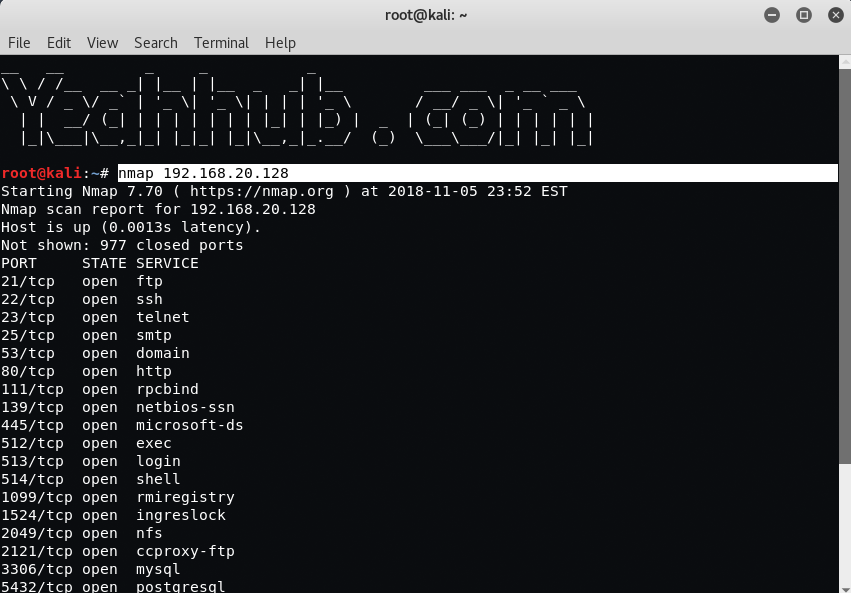
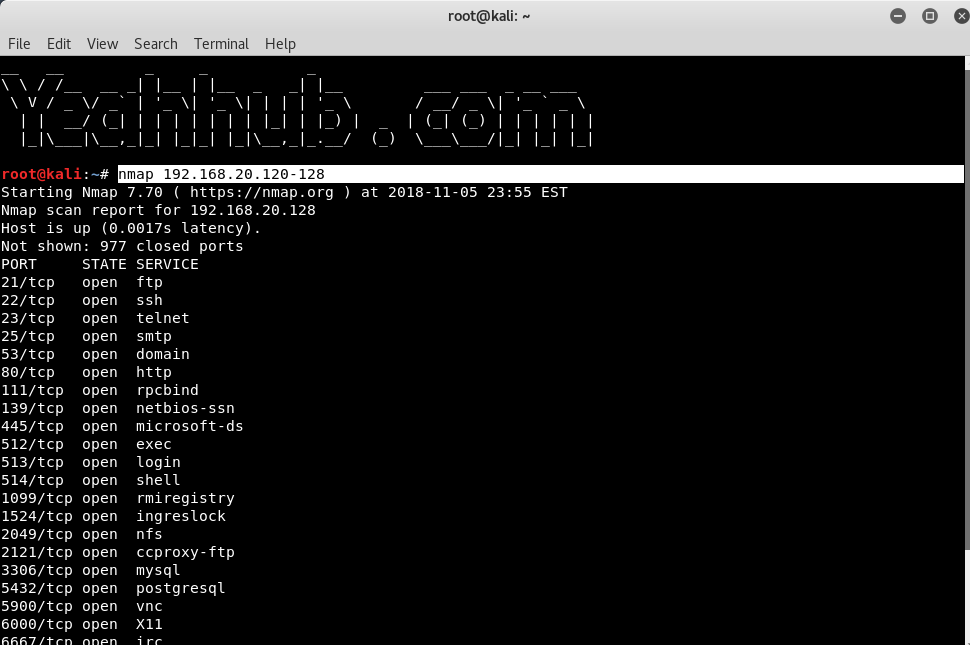
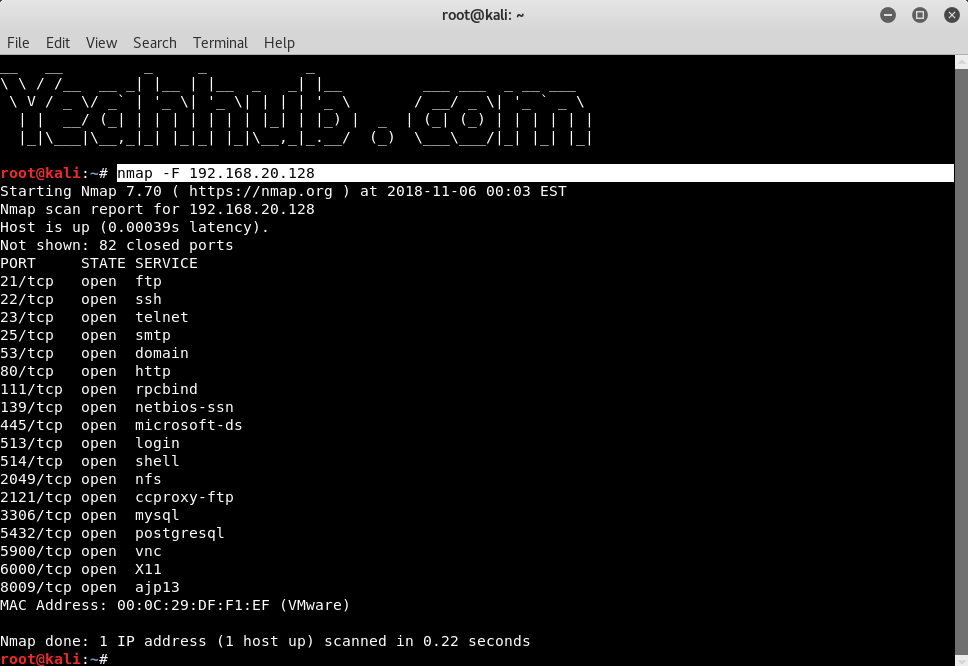
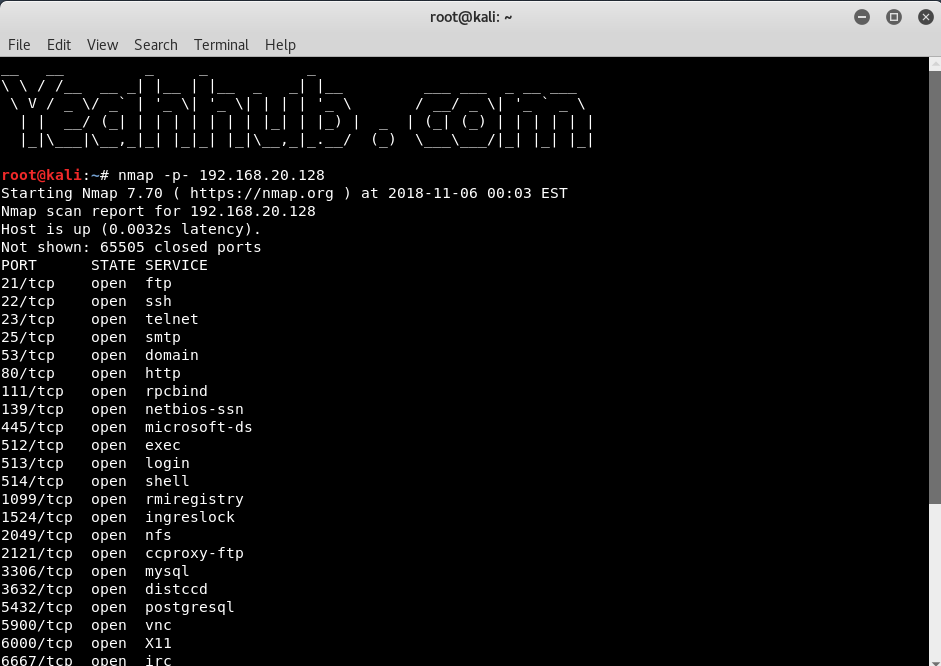
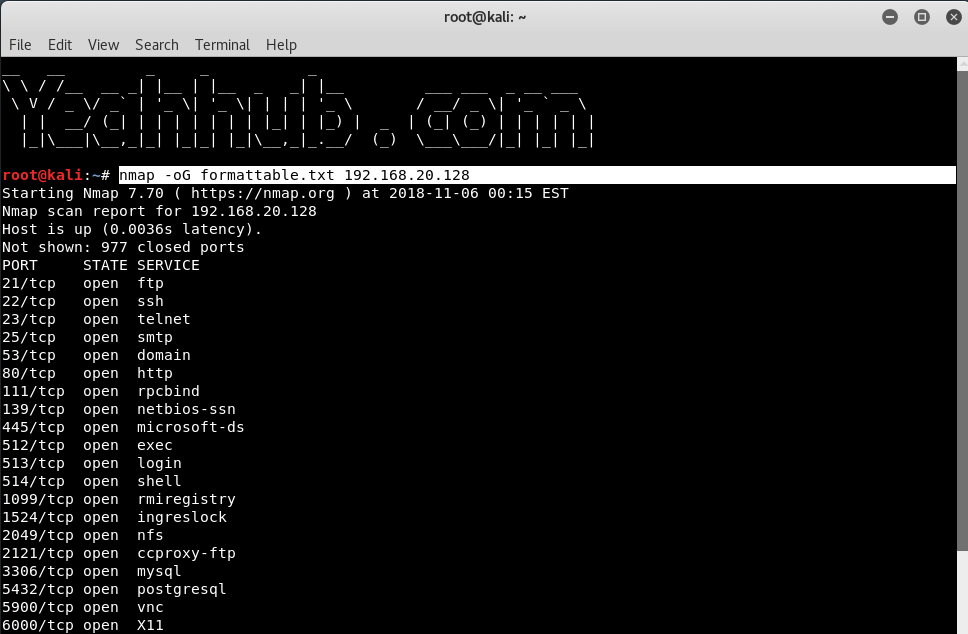
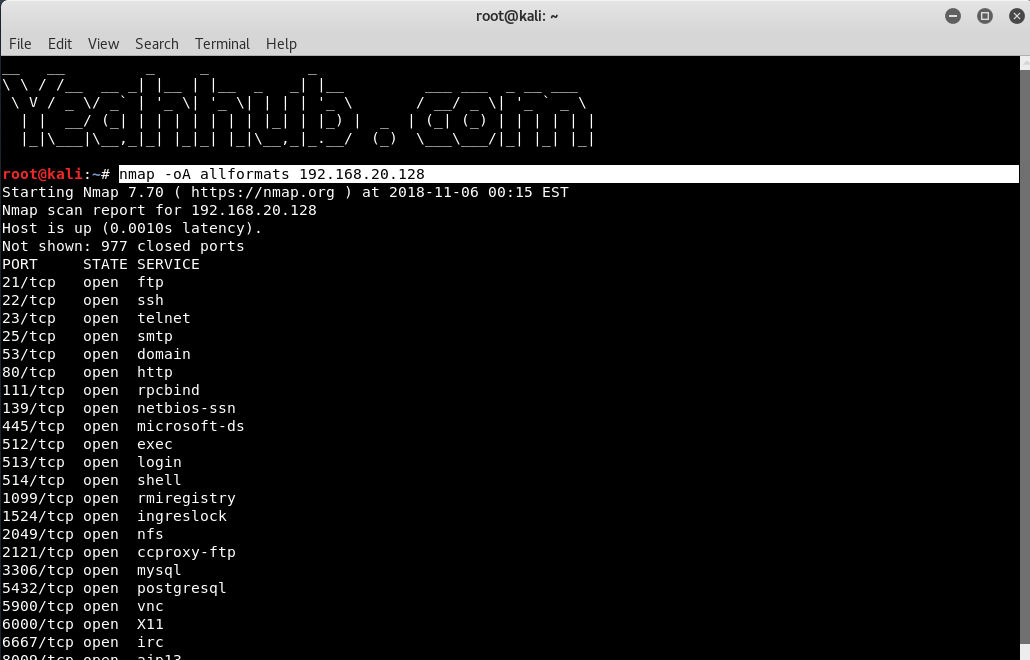
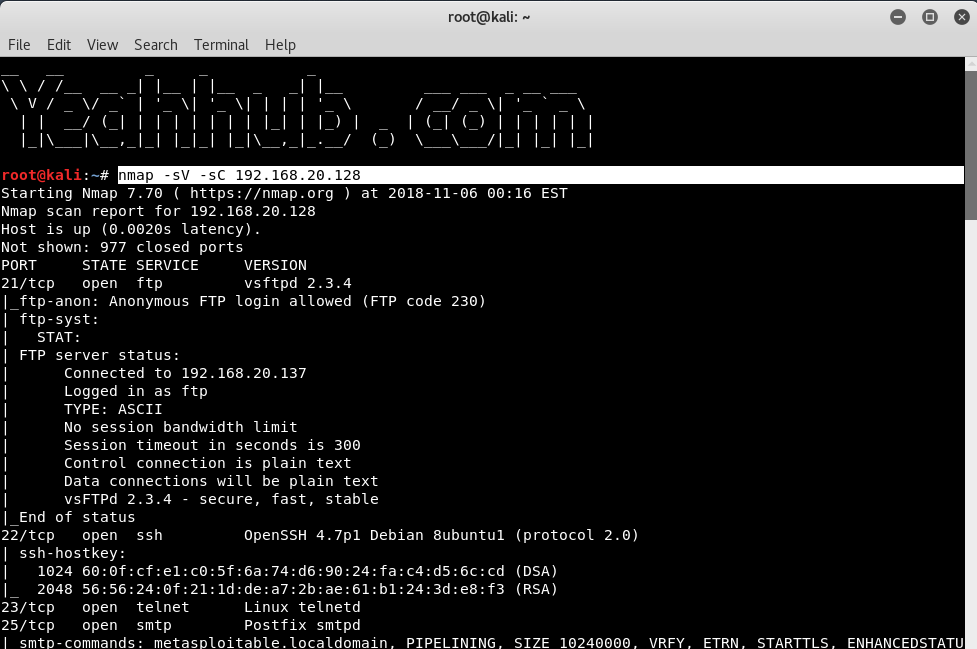
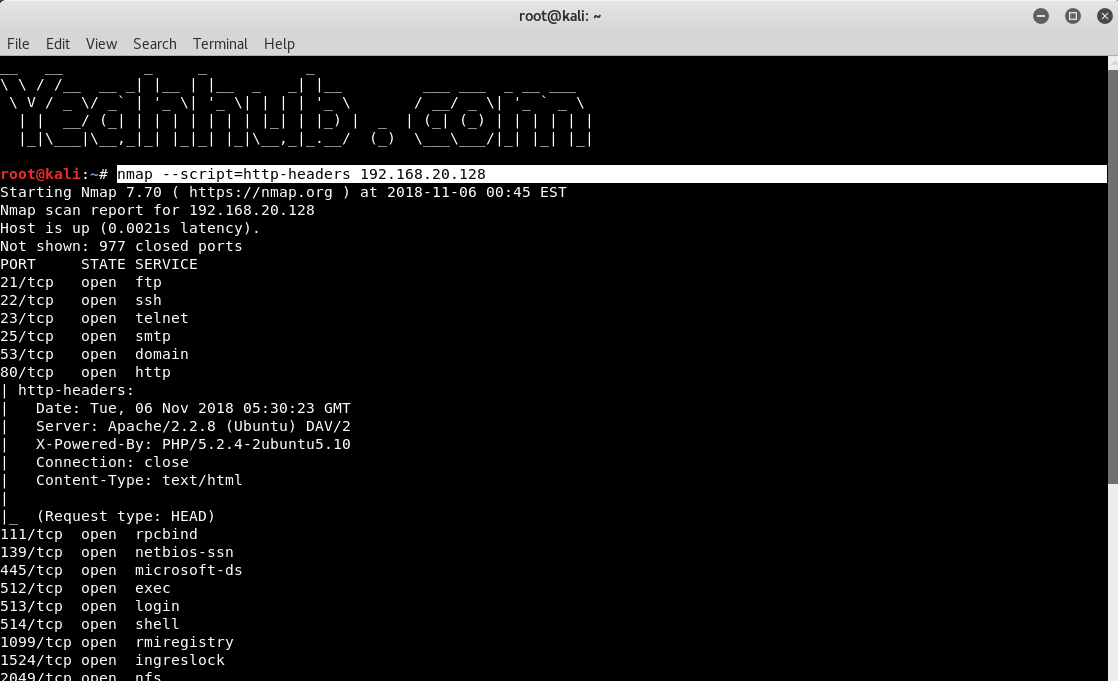
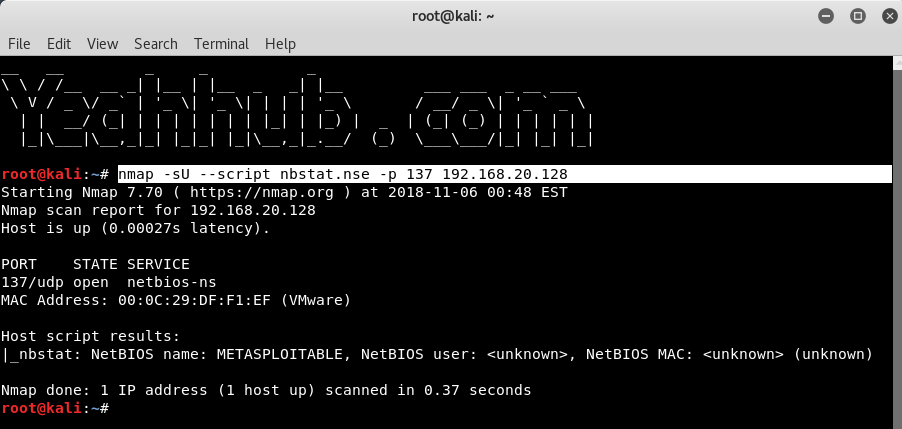
Nmap is a free tool that can be used to conduct various sorts of scans on networks. Normally, when people think of Nmap, they assume it’s used to conduct some sort of nefarious network reconnaissance in preparation for an attack. But as with all powerful tools, Nmap can be used for far more than breaking into networks.
One very important aspect of NMAP to remember is that these scans should be ran with Root or Administrator access depending on the type of system you are using. This is required because the scans send raw packets which require privileged system access.
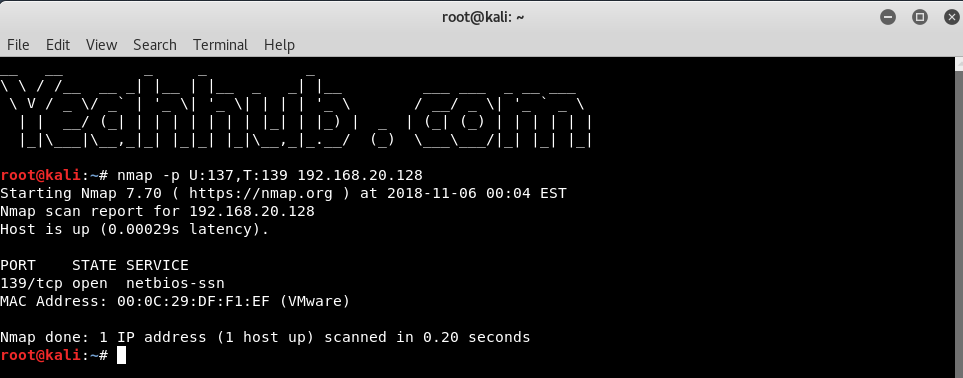
Of the scan types listed below table, only the connect and ftp bounce scans can be ran without privileged access. The last thing to remember is that these scans can only be ran one at a time except if you are running a UDP and TCP scan at the same time.
Now let us take a look at the parameters NMAP uses to perform the different types of system scans. Remember the basic command line format for nmap is:
Syntax: nmap <scan type> <options> <target>
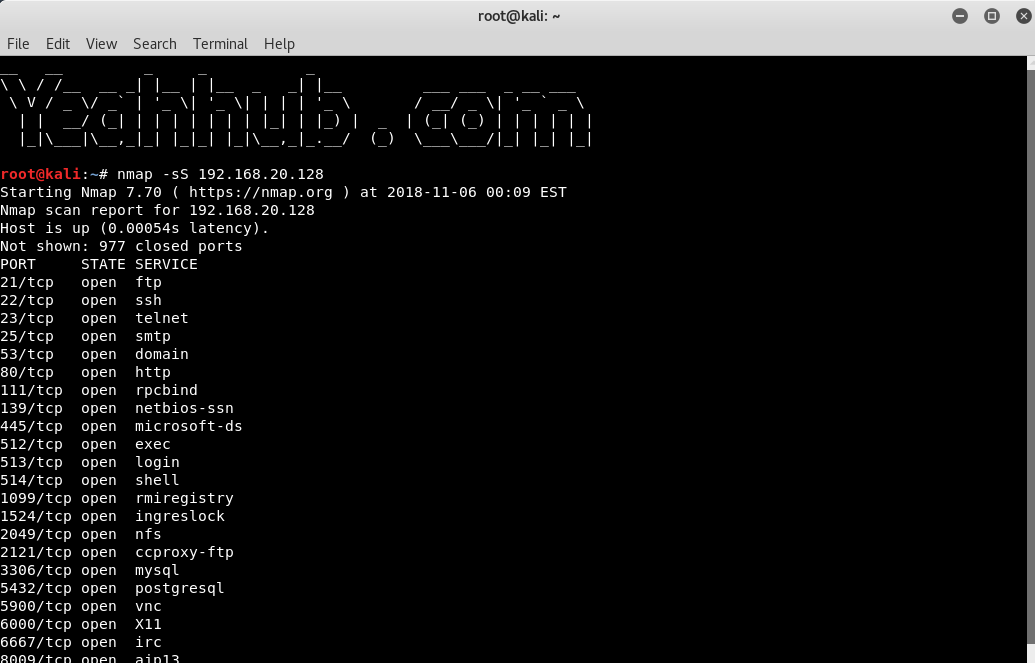
The thing to remember is that running different types of scans may produce different results as firewalls may limit the responses allowed from the specific hosts it protects.
More References –
- 19 Useful NMAP Commands You Should Know
- 5 Most Commonly Used Nmap Commands
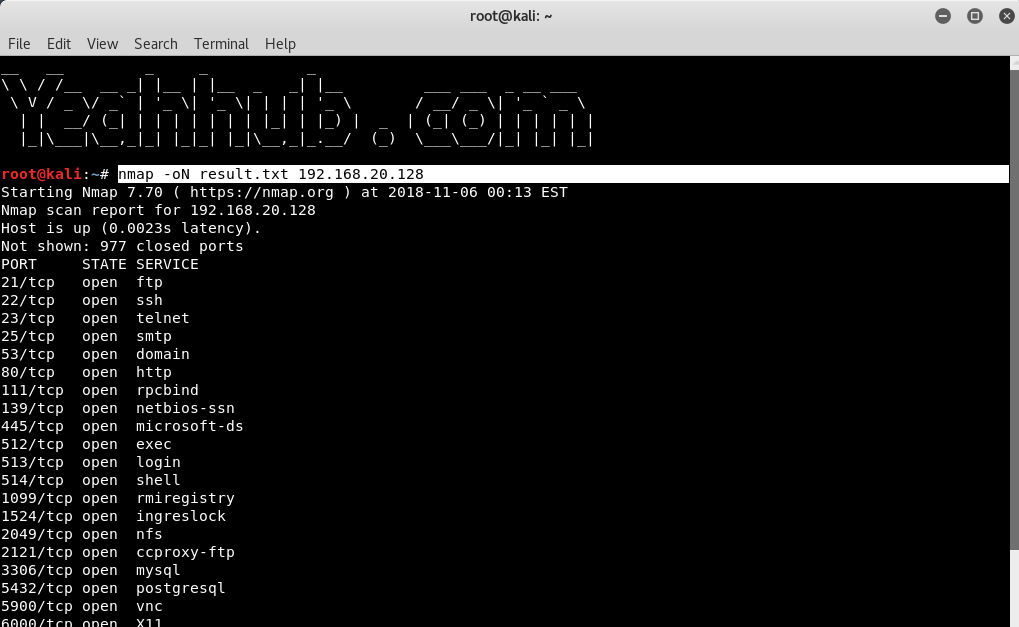
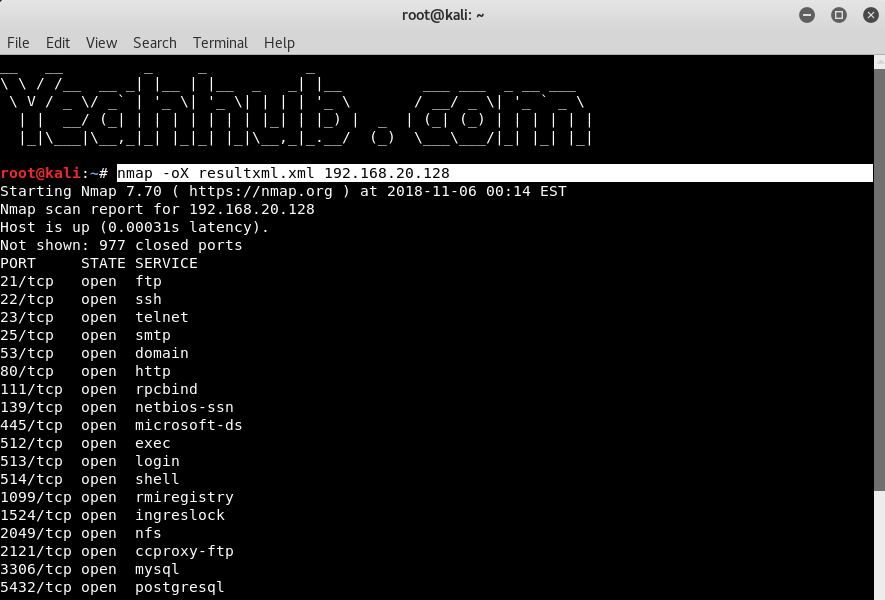
- Save Nmap Output To A File With 4 Different Ways
- Testing Methods For HTTPS With OpenSSL, Curl And Nmap
- 5 Books Considered The “Best Nmap Books Ever Written”
- Nmap Gets A New Look And Feel With NMapGUI
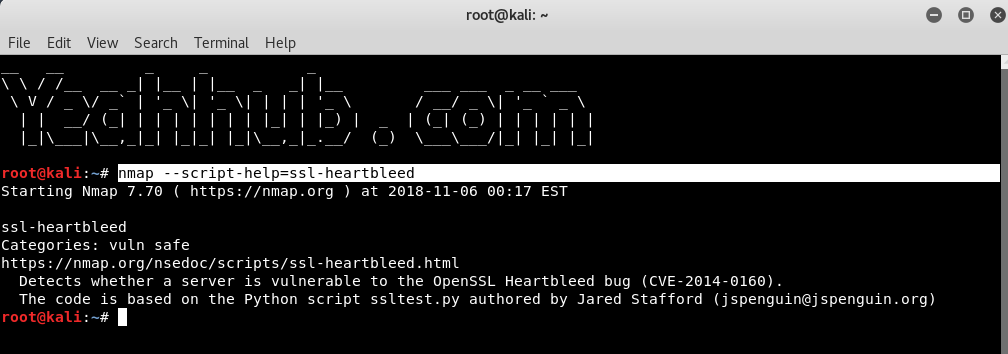
- Detection And Exploitation Of OpenSSL Heartbleed Vulnerability Using NMAP And METASPLOIT
- Top 7 Commercial Linux Distributions
- Why Do I Need a Website?
- Reinforcement Learning in Real-world Applications: The Latest Successes and Challenges
- Various Python Libraries for developing RESTful APIs
- Top 7 NodeJS Frameworks You Need To Know
- How Buying Instagram Followers Can Help Businesses Soar
- How To Find Gaps In Your Cybersecurity And How To Address Them
- How to close the site from indexing using robots.txt
- Internet Security With VPN – Why Do You Need It
- How to Fix The DLL Missing Error in Windows 7?