If you’re using the HTTP protocol for surfing Internet, you usually use only using two of its methods i.e. GET and POST. However HTTP has a number of other methods like OPTIONS, TRACE, CONNECT, PUT and DELETE which are very risky if all these HTTP Methods are open in your web server.
According to RFC 2616, there are 8 HTTP methods for HTTP 1.1, specifically OPTIONS, GET, HEAD, POST, PUT, DELETE, TRACE, and CONNECT, and this set can be extended.
- The OPTIONS method is used to request available methods on a server, while the GET method is used to retrieve the information that is requested.
- The GET method is one of the most common ways to retrieve web resources.
- The HEAD method is similar to the GET method, but is used to retrieve only header information.
- The POST method is used to send a request with the entity enclosed in a body; the response to this request is determined by the server.
- The PUT method is used to store the enclosed entity on a server.
- The DELETE method is used to remove the resources from the server.
- The TRACE method is employed to return the request that was received by the final recipient from the client so that it can diagnose the communication.
- The CONNECT method creates a tunnel with a proxy.
There are also extended HTTP methods such as web-based distribution authoring and versioning (DAV). WEBDAV can be used by clients to publish web contents and involves a number of other HTTP methods such as PROPFIND, MOVE, COPY, LOCK, UNLOCK, and MKCOL.
As we all knows, to test methods for HTTP websites, there are alot of tools are there like NC, Curl, Nmap, BurpSuite, Telnet etc but for SSL websites, this won’t work at all.
Today we’ll discuss the best 3 methods through which you can easily test methods/services for SSL based websites.
- With OpenSSL
- With CURL
- With NMAP
Also Read: Detection and Exploitation of OpenSSL Heartbleed Vulnerability using NMAP and METASPLOIT
1. Test with OpenSSL –
The OpenSSL command line tool can be used for several purposes like creating certificates, viewing certificates and testing https services/connectivity etc.
The following command can be used to test connectivity to an https service.
Command: openssl s_client -connect example.com:443
Basically s_client attribute is used to debug SSL Servers.
Reference Link – https://ping.force.com/Support/PingIdentityArticle?id=kA3400000008RYSCA2
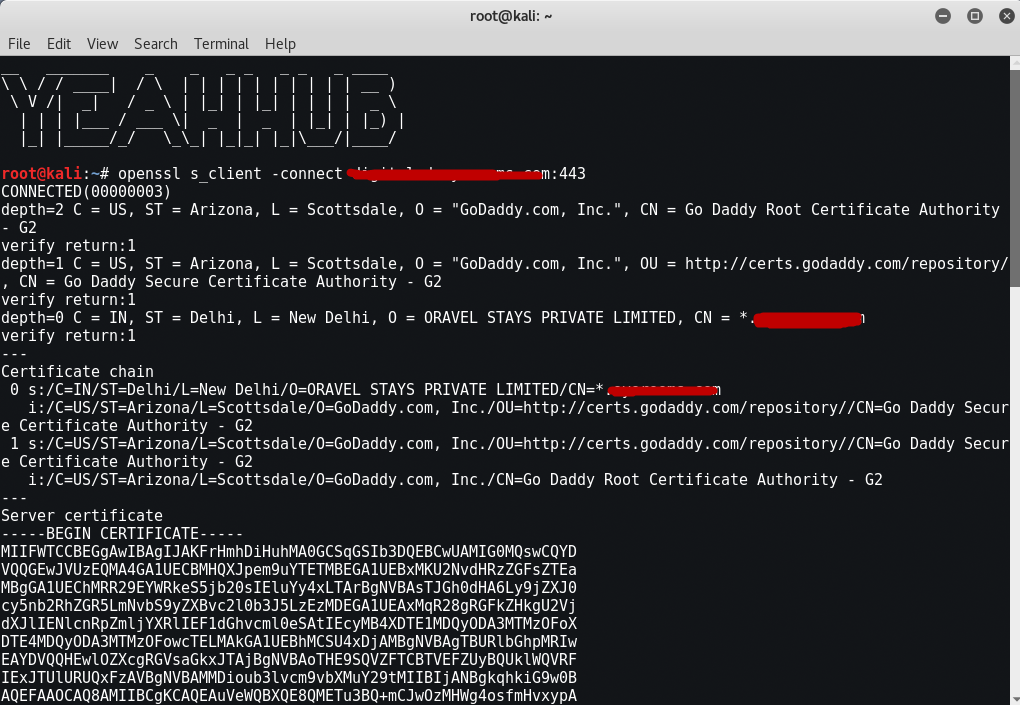
This will open an SSL connection to example.com with port 443 and print the SSL certificate used by the service. After connecting you can manually send http requests. This is similar to using telnet to connect to an http service and manually sending an http, i.e GET, OPTIONS or TRACE request.
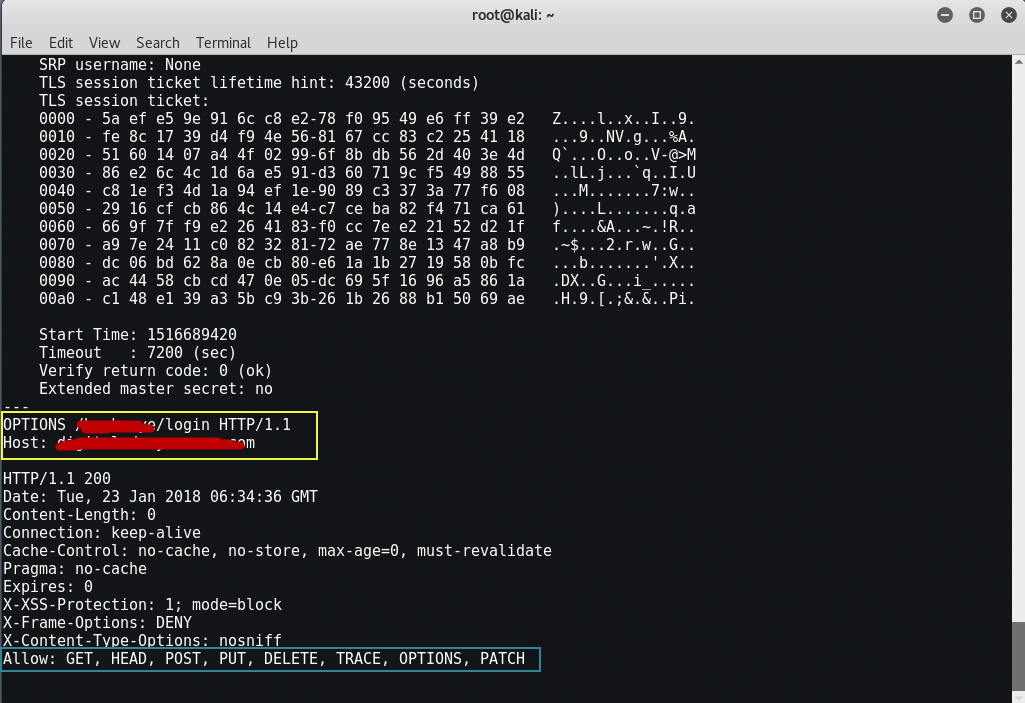
OPTIONS / HTTP/1.1
Host: example.com
Press Enter Twice:
2. Test with CURL –
CURL is the another useful utility through which you can test all methods for both http and https websites. The curl installed by default in Debian supports HTTPS since a great while back.
For HTTP –
Command: curl -i -X OPTIONS http://example.com/
For HTTPS –
Command: curl –insecure -i -X OPTIONS https://example.com/
Reference Link – https://curl.haxx.se/
You may also use -v instead of -i to see more output.

3. Test with NMAP –
Another method of checking which HTTP methods are enabled is using an NMAP script called http-methods.nse, which can be obtained from https://nmap.org/nsedoc/scripts/http-methods.html. This script is useful when multiple targets or ports need to be checked.
Command: nmap –script http-methods -p443 –script-args http-methods.url-path=’/page’ example.com
Reference Link – https://nmap.org/nsedoc/scripts/http-methods.html

Also Read: 5 Books Considered the “Best Nmap Books Ever Written”
Apache implements all relevant HTTP methods for static content (actual files served directly by Apache). For dynamic content, Apache does not care what the HTTP method is (unless it is explicitly restricted with a <Limit> directive), and passes the request to the appropriate handler as it is.
Upcoming Protocol HTTP/2 –
HTTP/2 is the first major upgrade to the HTTP protocol in over 15 years. Websites have changed dramatically, with the number of external image, CSS, and JavaScript assets growing by the year.
- HTTP/1.1 wasn’t designed for this kind of complexity.
HTTP/2 is optimized for the modern website, improving performance without complicated hacks like domain sharing and file concatenation.
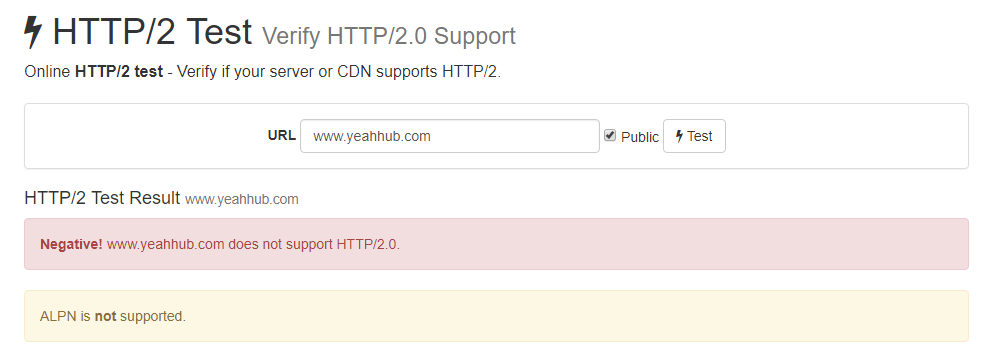
To check whether your site/server supports HTTP/2 or not, visit https://tools.keycdn.com/http2-test

For HTTP Testing, you could use a proxy, like Burp Suite or Zap, and follow the below steps:
- a) Set up your browser to pass through the chosen proxy.
- b) Make a normal HTTP request (e.g. GET /index.php HTTP/1.1) and intercept it.
- c) Forward that request to Repeater Tab and then change the GET method to OPTIONS and click the GO button which shows at top left corner.
- d) Analyze the HTTP response on other side.
If the HTTP response contains 200 OK, then it means that particular OPTIONS method is enabled on that web server.
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








