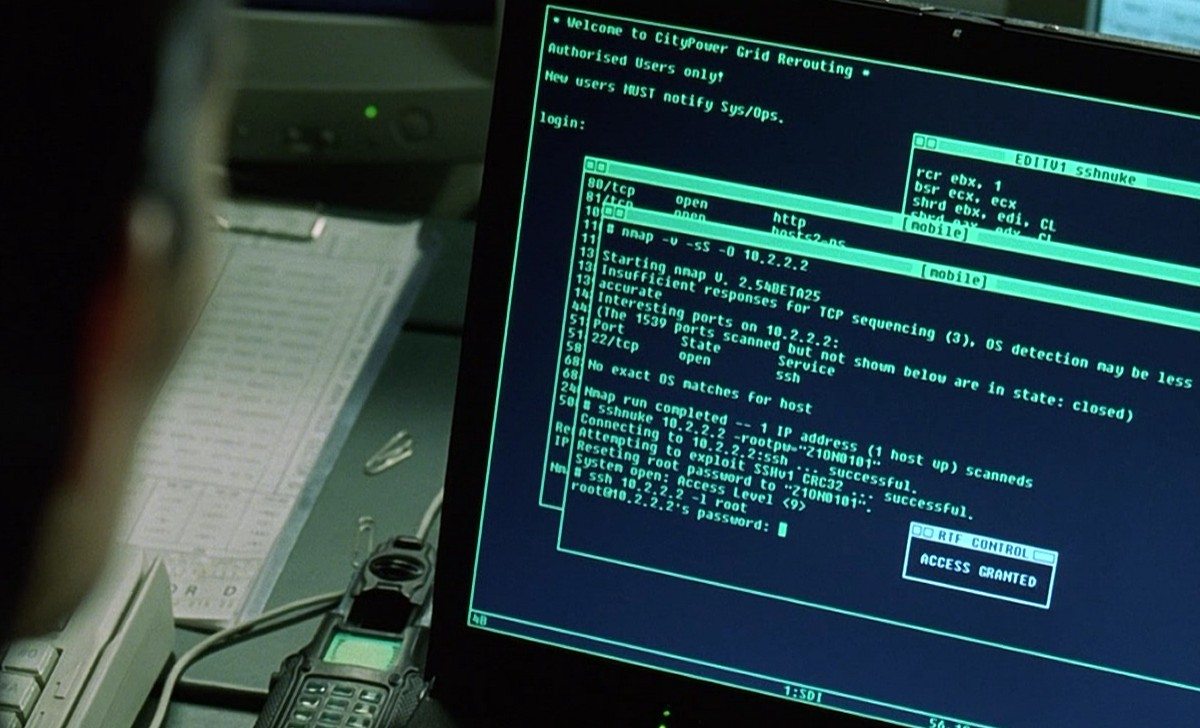
Nmap supports many scanning technologies, such as: UDP, TCP connect(), TCP SYN (half-open scan), ftp proxy (bounce attack), reverse flag, ICMP, FIN, ACK scan, Xmas Tree, SYN Scan and null scan. Nmap also…
Read more
Nmap supports many scanning technologies, such as: UDP, TCP connect(), TCP SYN (half-open scan), ftp proxy (bounce attack), reverse flag, ICMP, FIN, ACK scan, Xmas Tree, SYN Scan and null scan. Nmap also…
Read more