
Typically, a Penetration Testing exercise is focused on identifying the gaps in security rather than harming a system. This is a key feature that separates a real attacker from an authorized Penetration Tester. Real hackers don’t follow the rules and are not concerned about interrupting business if it can improve their situation.
In some cases, a hacker is looking to create any form of negative impact on a target, including taking down critical systems. For this reason, it makes sense in some cases to test systems for the risk of Denial of Service (DoS) type attacks. This is commonly termed as stress testing your Internet facing services.
The most common DoS attack involves flooding a target with external communication requests. This overload prevents the resource from responding to legitimate traffic, or slows its response so significantly that it is rendered unavailable. DoS attacks can target system resources (IE disk space, bandwidth, and so on), configuration information (IE remove route tables), state information (TCP session resetting), or anything that can harm system operation.
Categories of DOS/DDOS Attack –
- Volume Based Attacks: It involves UDP floods, ICMP floods, and other spoofed packet-based floods. The purpose is to saturate the bandwidth of the victim website.
- Protocol Attacks: It consumes resources of servers or intermediate communication equipment, such as routers, firewalls, load balancers, and so on. Examples are SYN floods, Ping of death, Smurf, Teardrop, fragmented packets, and so on.
- Application Layer Attacks: It leverages legitimate traffic to crash a web service. The examples include Zero-day attacks, vulnerability exploitation, and so on.
- Session Exhaustion: Abusing session limitations by repeatedly establishing but not closing new sessions with the goal of consuming resources.
Kali Linux contains multiple vulnerability exploitation tools that also can be used for Application Layer DOS attacks such as Ettercap, Metasploit Framework, Nmap etc.
Here we’ve a vulnerable machine so called Metasploitable2 hosted in our VMware workstation whose Local IP address is 192.168.36.132 (It might be different in your case).

1. DOS Attack with Slowloris.pl Script –
Slowloris is a low bandwidth HTTP Client that can issue DOS attacks but is very effective. Slowloris holds connections open by sending partial HTTP requests which continues to send several hundred subsequent headers at regular intervals to keep sockets from closing.
You can directly install the slowloris.pl script from Github Repository available at https://github.com/llaera/slowloris.pl
Command: git clone https://github.com/llaera/slowloris.pl

To run this script, type the following command:
Command: perl slowloris.pl -dns <IP/domain>

You’ll see slowloris consume available sockets, which will eventually take down the target.
This behavior will overwhelm the target’s resources, making it unable to respond to legitimate traffic. Even slowloris will flood all the available sockets, killing service to the victim website.

2. DOS Attack with Metasploit Framework –
Metasploit Framework which is one of the most popular post exploitation framework having so many exploitation/scanning tools inside it. The below scanning module basically used for testing IPS Protection at defending SYN floods.
Open the terminal and type “msfconsole” which opens your Metasploit Framework in a console and load the module named as “auxiliary/dos/tcp/synflood”
To use the above module, type use auxiliary/dos/tcp/synflood and further type “show options” to see all available options which this module requires.

After that, you need to set your target IP with command (set RHOST 192.168.36.132) with (set RPORT 80) and execute the exploit by typing either exploit or run command as shown below:

You can even monitor all the packets with the help of Wireshark Tool where you can actually see the packets sends from attacker network to targets network.
For Syn-FIN/Push-Ack Flooding, the another popular tool is also available called as Hping3 which is a free packet generator and analyzer for TCP/IP protocol distribution and is very effective to launch DOS/DDOS attacks against the target.
3. DOS Attack with XERXES –
Xerxes is another popular and powerful DOS tool written in C language which is available at https://github.com/zanyarjamal/xerxes
To download the above script, type “git clone https://github.com/zanyarjamal/xerxes.git” as shown below:

To run Xerxes, run the following command in your terminal:
Command: ./xerxes 192.168.36.132

As you can see that, the above command will sent thousands of packets within seconds and for more powerful attack, you should run this command in next 2-3 terminals with same syntax so that more packets will sent to target which actually increases the congestion level.
The same can also be done with the help of Ping Command. In Windows, we know that we can only sent 4 packets and so received only 4 acknowledgements but you can actually increase this size and define the custom packet size with the help of (-l) option, l means length.
Command: ping 192.168.36.132 -t -l 500

If you are using ping command to take down any server/machine, you really need to wait so much time for result.
With the help of LBD (Load Balancing Detector) which is an open source script and already available in Kali Linux, can easily detects if a domain/IP uses DNS or HTTP load balancing server or not.
Command: lbd 192.168.36.132

As you can see that in above screenshot, there is no load balancing server, so you can easily take down the machine.
4. DOS Attack with Ettercap –
Ettercap is one of the best tool for MITM attacks and can be used for computer network protocol analysis and security auditing. Ettercap supports both active and passive dissection of many protocols and includes many feature for network and host analysis.
Ettercap has many built-in tools/plugins to allow all sorts of network activity from sniffing to ARP Spoofing.
In DOS kind of attacks, an attacker attempts to make a machine or network resource unavailable for users. The goal is interrupted or suspended services that connect to the internet.
To start the Ettercap in graphical mode, type “ettercap -G‘ in your terminal.

Click on “Sniff” Tab and start Unified Sniffing which will further asks you to select the Network Interface.

Select eth0 as an interface if you are using NAT mode(LAN).

Furthermore, you need to move onto Plugins tab and select the dos_attack plugin which will asks you to enter your target IP as “Insert Victim IP“.

As you can see that, unified sniffing has been started and your target will be down instantly after some few minutes.

Basically, Ettercap can work with these 4 models:
- a) IP based
- b) Mac based
- c) ARP based
- d) PublicARP based
5. DOS attack with Nmap –
Nmap (Network Map), a favourite tool for pentesters and security researchers to find out the open ports against any target.
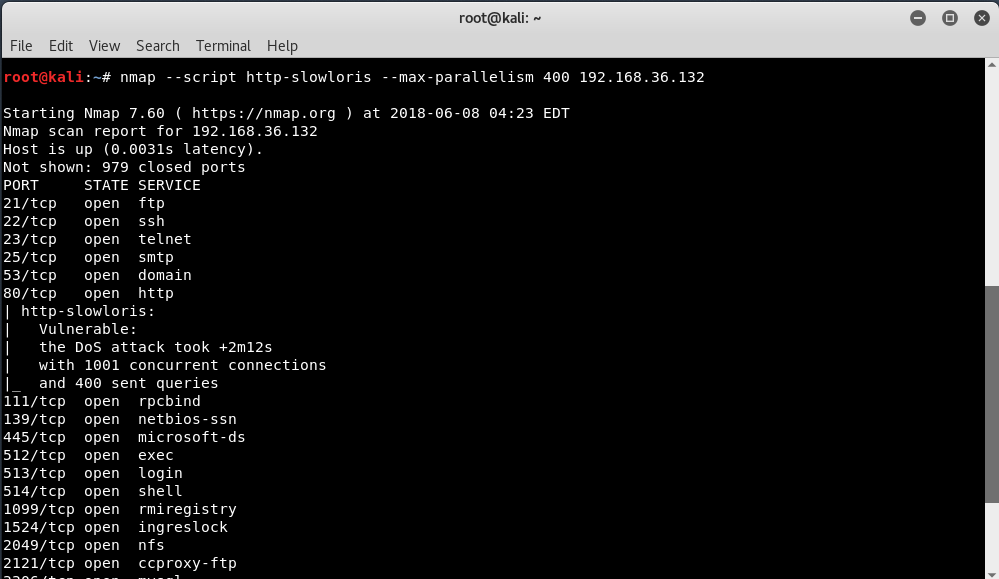
This http-slowloris-check script opens and maintains numerous “half-HTTP” connections until the server runs out of resources, leading to a denial of service. When a successful attack is detected, the script stops the attack and returns these pieces of information (which may be useful to tweak further filtering rules).
Below is the example of the command with nmap’s NSE script. This script tests a web server for vulnerability to the DoS attack without actually launching a DoS attack.
Syntax: nmap –script http-slowloris-check <Target IP/domain>
By default, the script runs for 30 minutes if DoS is not achieved. Please note that the number of concurrent connections must be defined with the option –max-parallelism (default is 20, suggested is 400 or more)
Read More: 5 Books considered the Best Nmap Books
Also, be advised that in some cases this attack can bring the web server down for good, not only while the attack is running. Also, due to OS limitations, the script is unlikely to work when running from Windows.
Command: nmap –script http-slowloris –mac-parallelism 400 <Target IP/domain>
- Top 50 Most Popular Cybersecurity Tools
- How Paraphrase Tool Helps To Optimize Content
- Best 20 Kali Linux Tools for Hacking and Penetration Testing
- Top 25 Open Source Intelligence Tools
- Online Domain Authority (DA) Rank Checker Websites
- Top 50 Hacking and Penetration Testing Tools [Compiled List 2019]
- Top 10 Essential CTF Tools for Solving Reversing Challenges
- Windows and Linux Privilege Escalation Tools – Compiled List 2019
- Subdomain Enumeration Tools – 2019 Update
- Top 10 Most Popular Bruteforce Hacking Tools – 2019 Update








