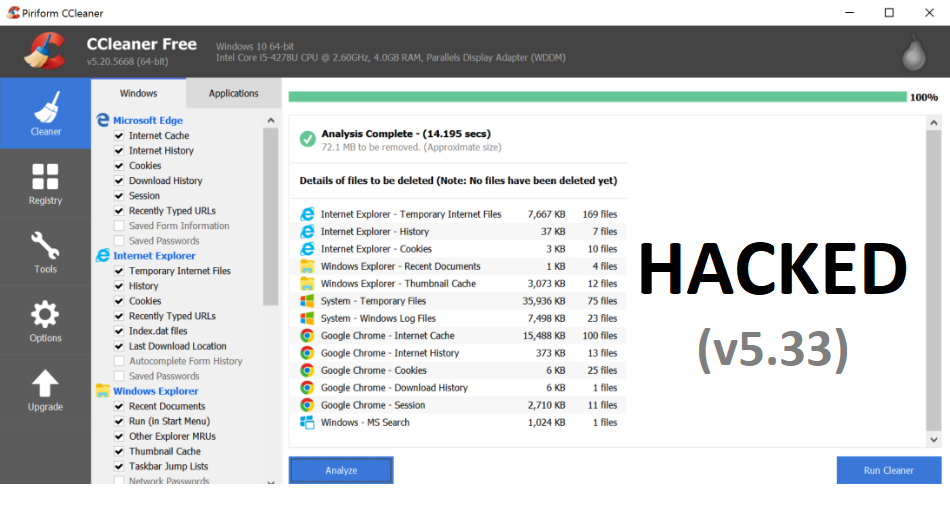
CCleaner is one of the most popular tool for cleaning for your PC. It makes it easy to speed up a slow computer and keep your activity private — automatically and in the background. It also regularly cleans junk files to keep your computer running smoothly.
Security researchers from Cisco Talos discovered that the download servers used by Avast to let users download the application were compromised by some unknown hackers, who replaced the original version of the software with the malicious one and distributed it to millions of users for around a month around 5 million people download CCleaner each week, which indicates that more than 20 Million people could have been infected with the malicious version the app.
On Sept 13, 2017, Cisco Talos identified a specific executable which was triggering their advanced malware protection systems and after complete analysis of CCLEANER of version 5.33, they’ve found that the downloaded installation exeutable was signed using a valid digital signature issued to Piriform and while installation of ccleaner, it was also contained a malicious payload that featured a Domain Generation Algorith (DGA) as well as hardcoded Command and Control functionality.
This particular affected version of CCleaner (v5.33) was released on August 15, 2017 and by 12th Sept 2017, they’ve released new version i.e. v5.44. So the malicious payload was being distributed in between these two above dates (From 15th August to 12th September).
The tool which claims more than 2 billion downloads and over 2 million active users according to parent company Avast, was infected with a malicious payload that made it possible to download and execute other suspicious software, including ransomware and keyloggers.
While developer Piriform and Avast have already confirmed the attack, the good thing is that there is currently no evidence to suggest the exploit was used to install additional malware.
For complete malware analysis details, please refer to Talos Reports.
This is the another example of Supply Chain Attack and earlier this year same supply chain attacks were happened in the form of Ransomware (Petya and Wannacry) which already infected millions of systems.

The malicious software was programmed to collect a large number of user data, including:
- Computer name
- List of installed software, including Windows updates
- List of all running processes
- IP and MAC addresses
- Additional information like whether the process is running with admin privileges and whether it is a 64-bit system.
According to Piriform, Now they’re investigating this issue that how this compromise happened and they’re also working with US Law enforcement in their investigation.
To download the latest version of Ccleaner, please refer to v5.34.
Piriform also gave a statement that – “Between the 12th and the 15th, we took immediate action to make sure that our Piriform CCleaner v5.33.6162 and CCleaner Cloud v1.07.3191 users were safe—we worked with download sites to remove CCleaner v5.33.6162, we pushed out a notification to update CCleaner users from v5.33.6162 to v5.34, we automatically updated CCleaner Cloud users from v1.07.3191 to 1.07.3214, and for users using Avast Antivirus, they received an automatic update.“
You may also like:- 30,000 Sites is in RISK, The Plus Addons for Elementor WordPress Plugin Hacked
- Facebook Pay is rolling out in US – 2019 Update
- Top 25 Reddits – SubReddits Communities [Information Security]
- List of 100+ Cyber Security RSS Feeds
- Target’s Twitter Account Compromised – Posted Fake Promoted Ad [Bitcoin Scam]
- Familiar With SQL Injection Vulnerability – Meet Ihsan Sencan
- Microsoft + 33 Other Companies Join hands to fight Cyber Attacks – Cyber Security Tech Accord
- Twitter Compromised ! Change Your Password Right Now – May 2018
- Update your Mozilla Firefox Now – 31st January 2018 Update
- Dangerous Keylogger Found – Infecting over 2000 WordPress sites