A number of different tools exist for performing automated vulnerability scans of web applications. These scanners have the benefit of being able to test a large amount of functionality in a relatively short time, and in a typical application are often able to identify a variety of important vulnerabilities.
Web application vulnerability scanners automate several of the techniques, including application spidering, discovery of default and common content, and probing for common vulnerabilities. Having mapped the application’s content, the scanner works through its functionality, submitting a range of test strings within each parameter of each request, and analyzes the application’s responses for signatures of common vulnerabilities.
The scanner produces a report describing each of the vulnerabilities it has discovered. This report usually includes the specific request and response that the application used to diagnose each reported vulnerability, enabling a knowledgeable user to manually investigate and confirm the existence of the bug.
A key requirement when you are deciding whether and when to use a vulnerability scanner is to understand the inherent strengths and weaknesses of these type of tools, and the challenges that need to be addressed in the course
of developing them. These considerations also affect how you can effectively make use of an automated scanner, and how to interpret and rely upon its results.
Here we’ve listed out top 6 Web Vulnerability Scanners which you can further use in your penetration testing projects but make sure that you must have written permission of testing from your client in the form of some document or NDA.
1. Netsparker
Netsparker finds and reports web application vulnerabilities such as SQL Injection and Cross-site Scripting (XSS) on all types of web applications, regardless of the platform and technology they are built with unique and dead accurate Proof-Based Scanning technology does not just report vulnerabilities, it also produces a Proof of Concept to confirm they are not false positives.
To get the demo of Netsparker, please click here and fill out the small form. The standard edition of Netsparker starts from $4995 USD on annually basis. Basically this tool comes with two variants i.e. Netsparker Desktop Edition and Netsparker Cloud edition.
For more information, please visit https://www.netsparker.com/
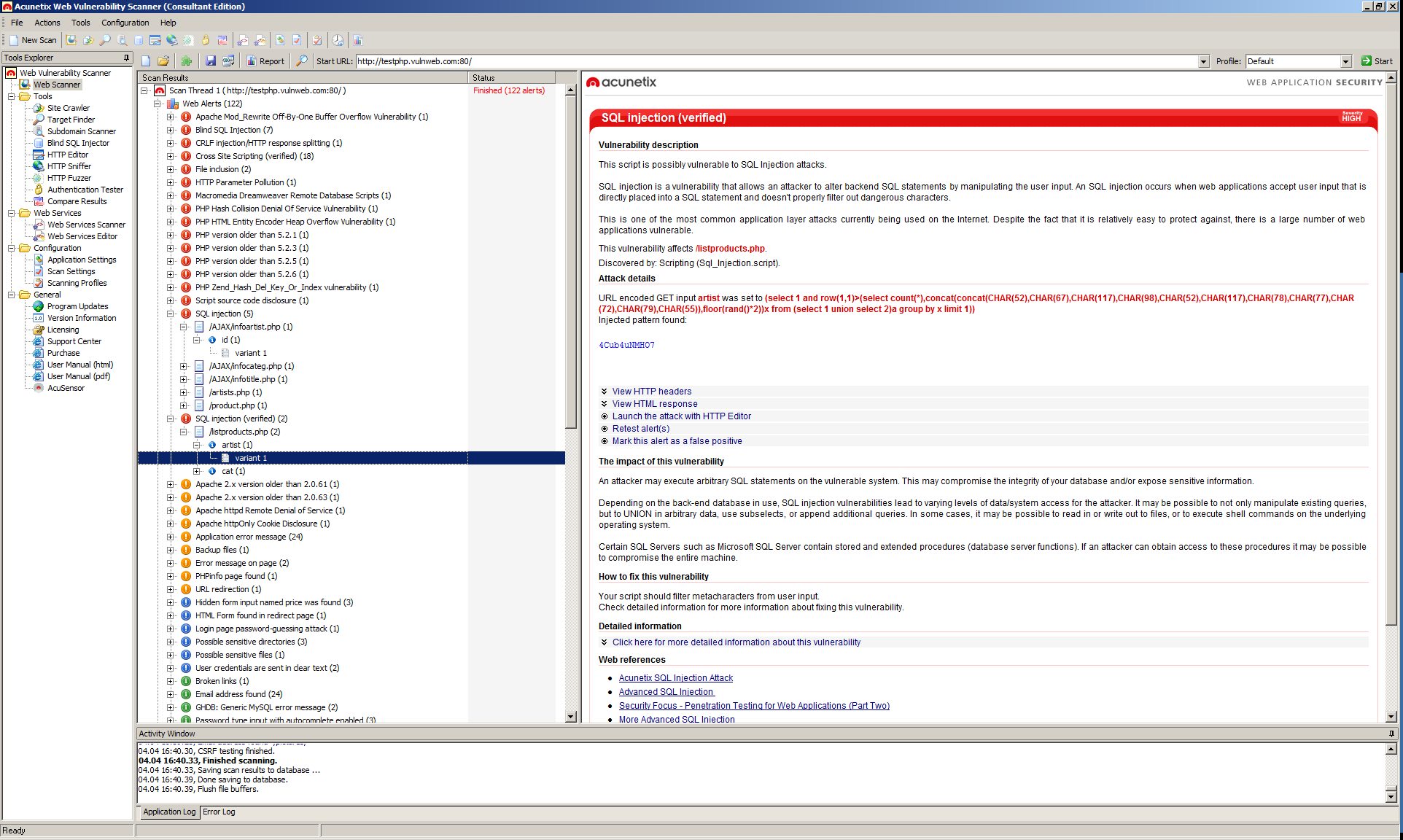
2. Acunetix
Acunetix is one of the most popular and leading web vulnerability scanner used by fortune 500 companies. It automatically crawls your websites and performs black box AND grey box hacking techniques which finds dangerous vulnerabilities that can compromise your website and data.
To get the demo of Acunetix, please click here. The standard edition of Acunetix starts from $4495 USD.
Features –
- In depth crawl and analysis – automatically scans all websites
- Highest detection rate of vulnerabilities with low false positives
- Integrated vulnerability management – prioritize & control threats
- Integration with popular WAFs and Issue Trackers
- Free network security scanning and Manual Testing tools
- Available on Windows, Linux and online
For more information, please visit https://www.acunetix.com/
3. Nikto
Nikto is another popular and open source web scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/programs, checks for outdated items, and version specific problems.
Nikto is not designed as a stealthy tool. It will test a web server in the quickest time possible, and is obvious in log files or to an IPS/IDS. It also supports SSL, proxies, host authentication, attack encoding and more. It can be updated automatically from the command-line, and supports the optional submission of updated version data back to the maintainers.
For more information, please visit https://cirt.net/Nikto2
4. Arachni
Arachni is a feature-full, modular, high-performance Ruby framework aimed towards helping penetration testers and administrators evaluate the security of modern web applications.
Arachni’s source code is publicly available, thus, providing a verifiable, inspectable code base to ensure your results have the highest level of protection, and that all possible issues are identified.
Out of the box, Arachni has all the full featured support and vulnerability analysis that one would expect from a first class web application scanner which includes SQL Injection, XSS, NoSQL Injection, Code Injection, File Inclusion Variants etc.
For more information, please visit http://www.arachni-scanner.com/
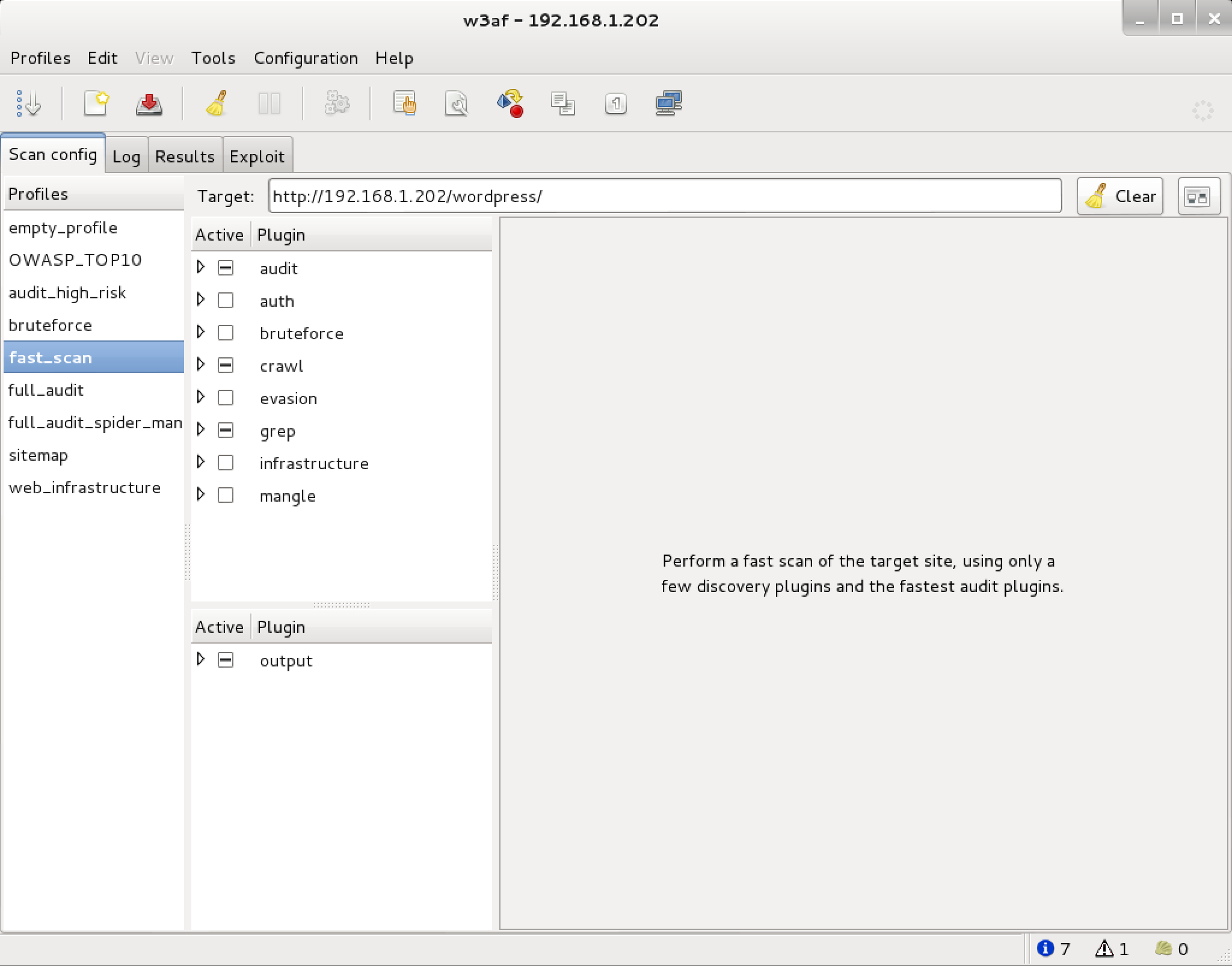
5. W3af
w3af is an open source Web Application Attack and Audit Framework. The project’s goal is to create a framework to help you secure your web applications by finding and exploiting all web application vulnerabilities.
Features –
Identify and exploit a SQL Injection
Easy to use for novice users
Fully customizable
Plugin architecture
Awesome fuzzing engine
For more information, please visit http://w3af.org/
6. Wapiti
Wapiti allows you to audit the security of your websites or web applications. Basically it performs “black-box” scans of the web application by crawling the web pages of the deployed web app, looking for scripts and forms where it can inject data. Once it gets the list of URLs, forms and their inputs, Wapiti acts like a fuzzer, injecting payloads to see if a script is vulnerable.
Wapiti can detect the following vulnerabilities –
- File disclosure (Local and remote include/require, fopen, readfile…)
- Database Injection (PHP/JSP/ASP SQL Injections and XPath Injections)
- XSS (Cross Site Scripting) injection (reflected and permanent)
- Command Execution detection (eval(), system(), passtru()…)
- CRLF Injection (HTTP Response Splitting, session fixation…)
- XXE (XML External Entity) injection
- SSRF (Server Side Request Forgery)
- Use of know potentially dangerous files (thanks to the Nikto database)
- Weak .htaccess configurations that can be bypassed
- Presence of backup files giving sensitive information (source code disclosure)
- Shellshock (aka Bash bug)
For more information, please visit http://wapiti.sourceforge.net/
Limitations of Scanners
The best vulnerability scanners on the market have been designed and implemented by experts who have given serious thought to the possible ways in which all kinds of web application vulnerabilities can be detected. It is no accident that the resulting scanners remain unable to reliably detect many categories of vulnerability. There are various inherent barriers to a fully automated approach to web application testing.
These barriers will only be effectively addressed by systems with full-blown artificial intelligence engines, going far
beyond the capabilities of today’s scanners.
- Top 7 Commercial Linux Distributions
- Why Do I Need a Website?
- Reinforcement Learning in Real-world Applications: The Latest Successes and Challenges
- Various Python Libraries for developing RESTful APIs
- Top 7 NodeJS Frameworks You Need To Know
- How Buying Instagram Followers Can Help Businesses Soar
- How To Find Gaps In Your Cybersecurity And How To Address Them
- How to close the site from indexing using robots.txt
- Internet Security With VPN – Why Do You Need It
- How to Fix The DLL Missing Error in Windows 7?