
Hacking the WordPress Core can make it very difficult to upgrade to the latest version of WordPress. Keeping WordPress current is an important step in overall web site security. If any security vulnerability is…
Read more
SQL injection is a technique, used to attack data-driven applications. Using this method, hackers will try to execute their SQL statements within your application and access your database data. Here is an example…
Read more
Malware is unfortunately far too common to ignore or be unaware of in this day and age. So this article should hopefully remedy some of the common questions. We guess the first one…
Read more
Enumeration is defined as the process of extracting user names, machine names, network resources, shares and services from a system. In this phase, the attacker creates an active connection to the system and…
Read more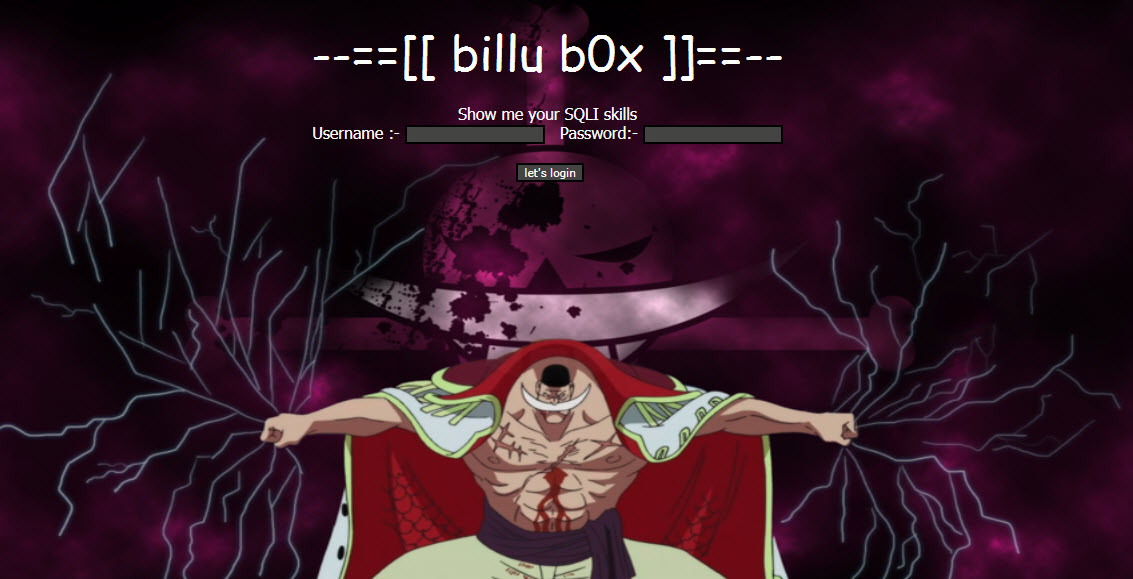
Billu:B0x VM is created by one of the most popular Indian Ethical Hacker named as “Manish Kishan Tanwar” (a.k.a Indishell Hacker) who has created so many web shells in PHP language hosted at…
Read more
PHP is a general-purpose scripting language especially suited for Web development. It is open-source and can be deployed on all major operating systems and web servers free of charge. It is imperative, reflective and…
Read more
1. What are the two types of paper feeder mechanisms? A. Continuous tractor feed B. Continuous form feed C. Friction feed D. Injected 2. What type of printer is most likely to use…
Read more
Being as popular cms, it is no surprise that WordPress is often always under attack. Some 70% of Techno’s top 100 blogs are using WordPress as a Content Management System. XML-RPC on WordPress…
Read more
Many aspects of our lives rely on the Internet and computers, including communications (email, cell phones, texting), transportation (traffic control signals, car engine systems, airplane navigation), government (birth/death records, social security, licensing, tax…
Read more
Error reporting is a good thing, right? It gives you valuable insight into why your application failed. It gives you useful information such as what happened and where it happened. This information is…
Read more
Computer Networking Questions which we mentioned here in below article will definitely helps you to crack all kind of technical Interviews. Question 1: What is an Internet service provider? Answer: Internet service providers…
Read more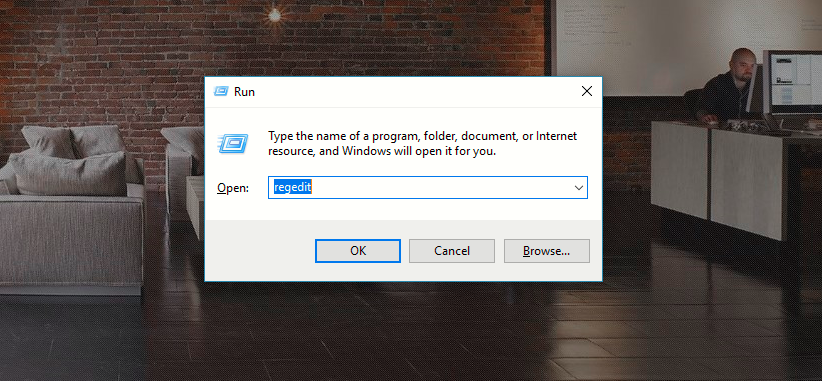
The Windows Registry is a database where all the information about a computer is stored. The Registry is used to store: Operating system configuration Application configuration information Hardware configuration information User security information Current…
Read more
File systems in the UNIX family have never been very well organized. Various incompatible naming conventions are used simultaneously, and different types of files are scattered randomly around the namespace. In many cases,…
Read more
SEO Keywords are very important for web content which enables people to find your website through search engines. The good website which generates high traffic are well optimized for search engines , the…
Read more
Microsoft join hands with other 34 global leading tech companies like Facebook, Google, Dell etc to fight with Cyber Attacks. We can’t deny that, cyber attacks are increasing day by day. Cyber Criminals…
Read more
Writing PHP applications is pretty easy. Most people grasp the syntax rather quickly and will within short time be able to produce a script that works using tutorials, references, books, and blogs like the one…
Read more
Microsoft Windows 10 brings a long list of important changes that any IT pro should look forward to, including major improvements in the user experience, significant security enhancements, and a new web browser…
Read more
Just when we thought the heat has finally settled on the Bitcoin debate, it looks like Blockchain has opened new doors for more feverish arguments and ideas on what the future of tech…
Read more



