
A sniffer is a program that monitors data traveling over a network. Unauthorized sniffers are dangerous to network security because they are difficult to detect and can be inserted almost anywhere, which makes them a favorite
weapon of hackers.
When used by malicious individuals, sniffers can represent a significant threat to the security of a network. Network intruders use sniffing to capture confidential information, and the terms sniffing and eavesdropping are often associated with this practice. However, sniffing is becoming a non-negative term; most people use the terms sniffing and network analysis interchangeably.
Using a sniffer in an illegitimate way is considered a passive attack, because it does not directly interface or connect to any other systems on the network. A sniffer can also be installed as part of the compromise of a computer on a network using an active attack.The passive nature of sniffers is what makes detecting them difficult.
Intruders use sniffers on networks for:
- Capturing clear text usernames and passwords
- Discovering the usage patterns of the users on a network
- Compromising proprietary information
- Capturing and replaying Voice over IP (VoIP) telephone conversations
- Mapping the layout of a network
- Passive OS fingerprinting
The above are all illegal uses of a sniffer unless you are a penetration tester whose job is to find and report these types of weaknesses.
The first step is to put your wireless interface into promiscuous mode by typing the following command in your terminal:
Command: ip link set wlan0 promisc on

Alternatively, you can also use the following command (optional) to put your card into promiscuous mode with ifconfig:
Command: ifconfig wlan0 promisc

To verify that whether your card in promiscuous mode or not, type the following command:
Command: netstat -i | grep -i “wlan0”

If you see letter P in last flag column, then it means you card is in promiscuous mode.
Now here’s the simple python basic script which sniffs particular requests/queries from google with parameter “/search?“.
Let’s save the below file with name sniff.py which you can also download directly from pastebin.

Initiate a google search request with curl (curl http://www.google.com/search?q=yeahhub+hacking+tutorials)

Top start the sniffer, type “python sniff.py” which shows all sniffed requests to google as shown below:

To presentable more which contains multiple words, here’s the second version of this python script which you need to save as sniff_new.py

And here you can see that all + symbols have been replaced with a blank space. And this sniffer would only works for HTTP protocol, as all the data goes in an unencrypted manner.

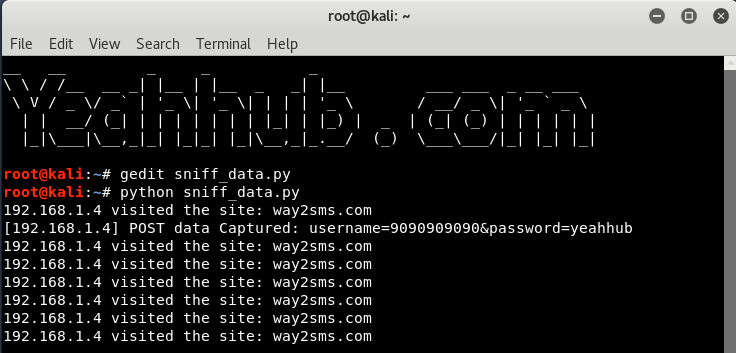
Furthermore, if you want to sniff the POST data of some particular website then here’s the third version of this sniffer named as sniff_data.py

Here, we’re trying to sniff the POST data packets of way2sms.com (because this is not on https) with action url (Login1.action) which you can easily capture through Browser Dev tools or with Burp Suite.
Now this script, what it does is basically check for visits to the target site. Next, to the line where it check for the headers to be a request, it checks for header to be generated for way2sms.com. After which the rest of our logic lies.
Navigate to the link way2sms.com, put anything into the username and password fields and press login button. As soon the request will be put on the wire, the sniffer terminal would show us the captured data in clear text format because of HTTP protocol.
Idea By: Shellvoide.com
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








