
In this article we’ll discuss about the malware forensics and analysis. We’re sure that most of us have fallen victims to a system hack. And we are not talking about the basic hack like Gmail or Yahoo hack that your team mates or your partners do.
We are talking about your private information, for example your bank details or your personal data which is being stolen from your system. Our one of the colleague had suffered a same situation where he visited a website, and something automatically started to download to his system. Some file went through all of his computer security forces and managed to infect it.
So how do we analyze these types of malwares? This article describes the best malware forensics methods to analyze the different malwares with static and dynamic approach.
What Malware is ?
A malware is a type of executable program code which affects the system adversely. After originating from its source, malware propagates itself through the network infecting every host that it comes across this. The chief intent of a malware is to compromise the system by launching any of its attack vectors. It works towards compromising system’s confidentiality (unauthorized access), integrity (manipulates the data) and availability (fools the system to serve illegitimate user and thus legitimate ones are deprived of its services as in Denial of Service attacks).

The main thing that differentiates it from rest of the program is that it has a trigger which has some indirect permission. Thus it does not have direct consent from user for running. A malware once executed, takes control of the whole system and also executes other malicious programs, all under the nose of the user.
Types of Malware
According to its behavior, a malware is classified into following categories:
1. Virus: A virus is a destructiveness executable program which has the capability of attaching itself with any of the legitimate file and move with the propagation vector. It poses great harms for the system and has the capability of destroying the information in the system.
2. Worm: Worms came in category of those malwares which exhausts system memory by continuous replication. It works without any solicited permission and limits network bandwidth by consuming a large part of it.
3. Trojan: This is the most dangerous type of malware which does the task of stealing information from the system. It has the capability of replicating itself and propagating itself to other networks in an automatic manner without any support from outside programs. Bot is a type of Trojan through which whole of the control of the system is granted to a third party and he can access it through his own system through a channel.
4. Root Kit: Through root kits hackers are able to install a backdoor in the victim’s system. Hacker can then access victim’s system for his own advances.
All these types of malwares are very harmful for any network or system if they occur in them. Therefore a network and system administrator has to keep a check on their networks and systems for any kind of malicious activity to keep their systems free of malwares. For that they are required to have knowledge of malware forensics.
Malware Forensics
Malware forensics is a technique in which with the help of certain tools and practices, a malware is reverse engineered; so that its true intent, origin etc. can be determined. Many kinds of behavioral and code analysis techniques are applied on a malware for carrying out the forensics of a malware.
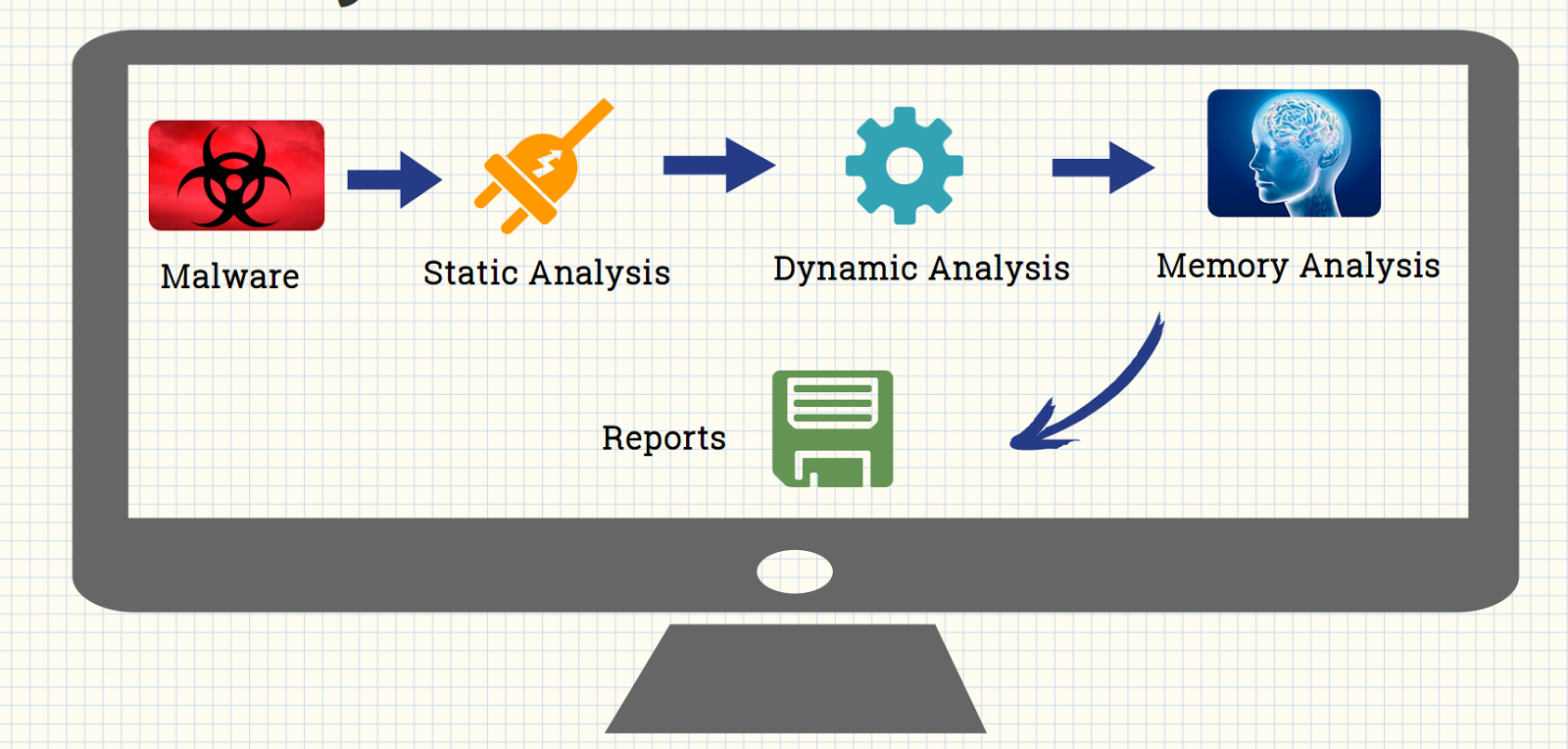
Having the knowledge of malware analysis helps greatly in determining what the purpose of malware was. It just doesn’t detect a program which is harmful, also helps in determine if there are any false positives.
Purpose of Malware Forensics
Malware forensics is the practice of identifying and type of malware and analyzing it. By the technique of malware analysis, the supposed malware can be identified in the network channel. Its detection is vital because its negative effects can be mitigated only when it can be properly detected.
Malware forensics adds sophistication to our design of algorithms for detecting malwares. Intrusions can be detected at a more accurate level when we know the kind of malware that can infect our system.
As the number of cyber crimes is on a rise, it is vital to keep hands on knowledge about malwares and their effect to secure economy of nation. Malicious intents have a wide potential to affect the nation’s economy with very worse effects. The damages thus occurred, in turn, give rise to a raised cost of realignments.
The repair needed for the damage done by such malicious acts may costs very much to the user sometimes. So malware analysis and forensics is a very important task which helps in mitigating the negative impact of a malware attack. It also helps in tracing back to its origin. Thus this technique is also very helpful in catching cyber criminals.
Malware forensics is a technique which is used by antivirus organizations to design its antivirus solutions. Their analysts detect malware and analyze them. According to their analysis results, antivirus solutions are designed. This helps in designing intrusion detection and prevention system as well.
Who writes malware?
Mostly the creators of malware go by the names of “Black Hat Hackers“. They are that person who does the task of infecting other systems either for fun, fame or money. Sometimes rival companies also take help of these methods and launch a spy program against an organization. A government can have internal or external threat by some foreign government that can trigger a malware against it to steal information or for destructive intents.
Malware Detection
Before we have a malware to analyze, first we need to detect its present in our network. There are many ways of detecting presence of a malware. We can install honey pots so that any kind of attack on our network is recorded and subsequently identified. Some of the methodologies which are employed for detection of malware are devised as follows.
- Malware & URL Scanner Online
- Free Website Malware Scanner
- Fast Online Virus Scanner with Addon
- Inspect, Detect and Protect
- Website Malware Scanner
Methodologies for Detection
1. Signature Based
2. Behavioral Based
3. Anomaly Based
Signature Based Detection
This kind of detection methodology works on binary patterns. Malwares are stored in the antivirus database by calculating a hash value according to its type. The signature of the malware is noted and is stored in the database. This works on known and pre-existing virus signatures. Now whenever a new executable functions in the system, its hash value is calculated according to a predetermined algorithm and compared with that of the hashes of stored files in virus database. If signature matches then it marks file as positive and an alarm is raised for the detected file.
The problem with this approach is continuous updating of the malware database as it stores only the known hence the old ones. Therefore new versions of malware remains undetected if database is not properly updated. For overcoming this issue, a generic signature for a malware class is used which has an algorithm of identifying all classes of malwares. Still there are possibilities of false positives in this kind of detection algorithm.
Behavioral Based Detection
This kind of detection methodology works on a virtual environment,generally a sandbox. This sandbox provides an immune environment for the system. This checks the malware in this virtual environment and discards it if any kind of suspicion or infection is found in the executable thereby protecting the system all throughout. This technique basically analyzes the behavior of the executable under controlled conditions.
Writers of malware are packing data and using such kind of obfuscation techniques which creates more number of polymorphic instances of same malware. This means signature based detection is quite hard to implement in practice. Attacker of the malware keeps on changing the signature of the malware and thus can easily dodge signature based technique.

Therefore to overcome this problem, malware has to go through two shields in behavioral based detection. The first one is shield of host based antivirus and second one is antivirus gateway. In this kind of detection technique, false positives are more common and thus behavioral based detection is not a suitable technique to be employed in the network channel.
Anomaly Based Detection
In anomaly based detection technique, the behavior of the malware is studied and accordingly a profile is created. This approach works in two phases. In the first phase known as the “Training phase”, behavior of the attacker is learned by the system through machine learning. Nowadays this makes use of artificial neural networks like Hebb net etc. During this phase subsequent profiles of the system processes are created. These profiles are the signatures of proper work of the system. Now the work of second phase occurs. After suitable profiles are stored in the database of the detector, any kind of abnormal behavior is caught readily.
The routine system processes are compared with the profiles in the database. Until no deviations are found, everything is normal. But if any deviation from the profile is registered by comparing it with the database files, an alarm is triggered. This marks the detection of a malware or suspicious activity.
Profiles can be static or dynamic. Static profiles are those in which one time training is done and profiles are stored in the database. In the dynamic profiles, the data keeps on changing according to the system in question. This way the detector is always in some kind of training mode. This reduces the number of false positives along with making the detection more accurate.
All these kinds of detection methodologies are put together to build a strong malware forensics technique. Through these detection methodologies we are able to detect supposed malware. It is only after detection that analyses phase begins.
Mobile Malware Forensics
Nowadays malwares are not only affecting computers but cellular technology is also at a target for malwares. As phones are becoming smarter, the risk of them getting under the attack of malwares is getting higher. Smart Phones are no less than computers in the modern times.

Their advanced operating systems like android, ios, windows etc. are making the phones more tech savvy on the one place while at the same time making the applications vulnerable to malwares. These malwares affect the persons on the same level as they might have if were on a system. Web applications run on the same in mobiles and computers. Internet has a wider reach through packet data and wireless networks to all portable devices.
There are many kinds of malwares that are detected which affects especially your mobile phones. This includes reading your private messages, sniffing on your calls, hijacking sessions on cell phones etc. These malwares hides themselves in the camouflage of applications. Malwares disguise them and run on the background. Mobile malwares are more complicated to handle than system malwares. Unlike system malwares, they don’t get detected and analyzed easily. For mobile, many antivirus solutions are present which may help to protect it.
• Talking Angela Hoax
In the last year, a psychological malware posed a prominent threat to users especially kids. This malware was in the disguise of a mobile application named as “Talking Angela”. This application has an appealing interface which has a cat like creature which gives an impression that it is talking to user.
Parents who were looking for some interactive application for their children thought this app to be the one which can help in enhancing interactivity of their child. But this app was a total scare. This asks children personal questions and is known to record all the data in its database.

It even takes pictures of children or anyone using this application without consent of the user. The user does not even know of such kind of phenomenon going on. It sends those pictures to online database.
There were possibilities of serious crimes like pictures being broadcasted for pedophiles. This kind of malware does not pose as a serious threat until user interacts with it himself. So malwares does not only affects our systems, it can also affect our brains. These kinds of psychological malwares are obvious examples in support of this theory.
Malware Analysis Lab
After we have a malware to analyze we need to create a virtual environment so that it does not affect out system anyhow in real time. Therefore, for performing any kind of malware analysis or forensics, a malware analysis lab is set up at first. It consists of virtual hosts which are infected and on which the effect of the malware is studied.
These virtual hosts contain virtual machines, different operating systems with different configurations. In this lab, the malware is allowed to act in a controlled manner and behavior of malware is studied in various conditions.The setup of the lab is done as according to the guidelines specified for a protected malware forensics. Same kind of hardware is utilized again and again by using virtual machines so that effect of the malware is studied.
Types of Analysis
There are two types of malware analysis techniques that are carried out.
• Behavioral Analysis
• Code Analysis
Behavioral Analysis
In this kind of detection technique the behavior of the malware is studied. For performing behavioral analysis, in malware testing lab, virtual hosts are set up. The environment is subject to get affected by malware and subsequent effects are noticed.

It includes various phases like noting the effect of malware on registry upon execution, its effect in network traffic, data packets it sends and receive, processes it creates in the system, new files it creates, destruction it does in the system etc. This kind of analysis is done chiefly to notice the operations carried out by malware. It lets the user know of the changes that malware brings into the system.
Tools Used
Various tools are available for behavioral analysis of malware. This gives a deeper insight into the processes carried out by the malware. This places solid grounds for establishing the fact that the supposed executable is indeed a malware and can harm our system adversely if not checked on time. Some of the tools are explained below.
• RegShot
This tool is used for noticing the changes that are made in the registry of the system by malware. For using this tool first of all a clean environment is created having nothing else other than basic functionalities.
Then regshot is launched and a shot of the clean system is taken. Then the supposed malware is launched and second shot is taken. Then two files are compared and the changes done to the system is noticed. This gives a rough idea of what files malware are adding or deleting from the registry.
Similar to regshot, process monitor helps in identifying the processes that malware adds in the system. While operating this all other utilities and software must be closed. Then only malware is launched and process monitor is made to work out. Through this tool, newly added processes can be determined.
This helps in determining the class of malware. Like if it starts processes like svchost.exe then it concludes that it is a Trojan which is giving access of our system to foreign host. Similarly if replicated processes are there then it is class of worm. If some kind of malfunctions is occurring in file; like modifications in contents of operating system especially system32 files then malware can be classified as a virus. Similar to process monitor, process explorer can be used for the same purpose.
Using wire shark, the network traffic produced is analyzed. This tool helps in determining the type of traffic the malware is creating at network channels. This helps in analyzing the network packets that malware is creating. So if a malware is a Trojan and sending your system data to a third party then it is detected at network level by analyzing data packets.

This tool is a powerful packet analyzer that can be used for various purposes like capturing network headers and analyzing HTTP requests in plain text. This is also used for reverse engineering network protocols.
There are many other tools which can be used for determining behavior of the malware like Capture Bat etc. Generally phases of malware analysis contain these basic operations.
Code Analysis
After the fact is established that the supposed executable is a malware and has subsequent effect on the system environment then code of the malware is analyzed. . In code analysis, actual task of the malware is studied by the technique of reverse engineering. Through this analysis,the executable can be totally autopsied and a suitable report can be generated for the analysis of malware.
• Reverse Engineering
Generally, we have the executable of the malware which does not provide us with the original program code through which we can gather sufficient data about malware. The publisher of the malware is of course not going to provide us with the code. Therefore, a technique known as reverse engineering is employed for the same.
In this technique, the code of the executable file is opened in assembly language using suitable software like olly debugger. Assembly language is the language of mnemonics which has a set of instructions for each program line. This is the language prior to the conversion of the code into binary code. This is also the technique through which course of the normal program execution can be altered.
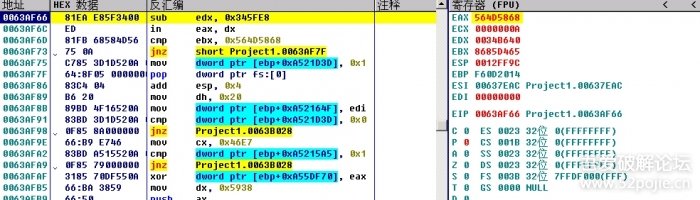
Reverse Engineering is a methodology in which whole of the assembly language code of the software is studied which can be obtained through an executable. It includes various operations to be carried out on the malware for determining its actual functioning.
The last resort used in malware analysis is altering the normal program execution in such a manner that malware itself specifies the function for which it is designed. Chiefly the tool olly debugger is used for malware forensics through reverse engineering.
• Ollydbg
Ollydbg is an open source tool freely available for all popular versions of operating systems like Windows, Linux, and Macintosh etc. This is a multipurpose tool which has various functionalities like making changes in the executable through assembly language. The instructions can be altered and thus functionalities of the malware can be determined.
Thus there are various methods of analyzing a malware. In this article we’ve mentioned only the fundamental ones. Apart from these techniques malware analysis can be done from a very basic to a very advanced level.
In the entire scenario, one thing to bear in mind is that analysis of the malware should be done carefully. Only then suitable signatures can be designed which forms the grounds of virus detection by antivirus solutions and intrusion detection systems.
Other Tools Used
Apart from all these tools, some other tools which are used for analyzing network channels and investigating malware functions are as follows.
• Grep
This is command line utility in UNIX/LINUX systems which are used for searching for particular strings. It is a powerful utility and if used properly can provide result of complicated problems.
• Antivirus Solutions
Many antivirus solutions like Avira, Avast, Norton, MacAfee, Quick heal, Anti malware bytes etc. are used for scanning and locating the malwares. It detects presence of a malicious activity and prevents system from any kind of infection.
• Whois
This tool is used for putting queries in RIPE database and retrieving information from the database like registration information of domains etc. It also gives information about IP addresses and domain names.
• IDA Pro
This tool is used like Ollydbg to disassemble and debug the software executable through assembly language.
• Hexedit
This is used for viewing raw data of the file in hex format. Binaries are changed to hex mode which can also be edited.
• VMware
This tool is used for providing virtual environment to the user and creating proper malware testing lab. This creates a sand box environment for the malware to run.
• File Analyzer
A safer networking tool used for analyzing files.
• Helix
It is a Linux based platform which acts as a malware forensics toolkit.
• Sys Internals
This system utility is designed by Microsoft Corporation to troubleshoot, manage, and diagnose various system issues in Windows.
Significance of Malware Forensics
The task of malware analysis is becoming more and more difficult because with the technology, writers and coders of malware are also becoming more sophisticated. Many forensics methods are in use for the detection of malware. Most common type of malware is HTTP based malware which affects web and communicates through command and control server.
HTTP based behavioral clustering is one of those techniques which are used for detecting malwares. Anomaly based botnet detection systems like Bot Miner are used for detecting botnet compromised networks in the enterprise. Although it uses high level statistics for network flows clustering, it is only limited to detecting Bot compromised networks.
Conclusion
The general malware analysis approach includes behavioral& code analysis phase. The phase begins with observing the specimen’s behavior in an isolated lab using several monitoring tools. Then these observations are used to determine how to interact with the malware, which produced additional results.
Additional malicious characteristics are evoked by gradually molding the laboratory environment to match the world within which the specimen is expected to operate. Having an initial understanding of the capabilities of program, various code analysis techniques are used to further understand the program’s characteristics. In this phase, strings of the program are analyzed by placing memory access breakpoints.
After static analysis, dynamic analysis can be carried out to advance levels. At binary levels, dissection and disassembly of the malware is performed. Debugging is an important process through which such information can be obtained which is difficult to be obtained otherwise.
A properly done malware forensics has a nice role to play in securing your enterprise. It can be used to add sophistication to antivirus solutions. In modern forensics, malware analysis has a vital role to play.
You may also like:- Top 7 Commercial Linux Distributions
- Why Do I Need a Website?
- Reinforcement Learning in Real-world Applications: The Latest Successes and Challenges
- Various Python Libraries for developing RESTful APIs
- Top 7 NodeJS Frameworks You Need To Know
- How Buying Instagram Followers Can Help Businesses Soar
- How To Find Gaps In Your Cybersecurity And How To Address Them
- How to close the site from indexing using robots.txt
- Internet Security With VPN – Why Do You Need It
- How to Fix The DLL Missing Error in Windows 7?








