
In the world today mobile has become a vital possession. It is not just your cellphone. It has become more than that. It compensates for so many things that you cannot just afford to lose it. In the same way it holds so much of your confidential data that you cannot afford to get your data compromised as well.
Mobile hackers today are no longer lone cyber criminals; rather they have grown themselves into well-versed business professionals dedicated to some serious operations.
In this article, we’re going to enlighten you with latest kinds of malware threats that have started to emerge in smartphone industries now. With the knowledge of these trends you can try to protect your phone with all kinds of potential threats.
What Mobile Malware is ?
Malware is software which when executed affects our device adversely. A mobile malware is a program code which is created for the purpose of affecting mobile devices like cellphones, wireless devices like PDA (Personal Digital Assistants) in a manner to disable it, control it remotely or steal your valuable and confidential information.
In its most fundamental senses, Mobile malwares are just the same as PC malwares just that their mode and target of operation is mobile device rather than computers.
Mobile malware are increasing at a rapid rate with both technological and structural aspects. It is estimated that in the year 2013 mobile cyber-attacks has risen at large rates. Nowadays smartphones and mobile devices are being used for the same purpose as computers are.
Addition: Read More about Mobile Malware Threats
Therefore like computers, smartphones etc. are also vulnerable in same ways to malware threats like virus, Trojans etc. As a large portion of population use smartphones; they are becoming potential targets for hackers for compromising sensitive information.
Potential Threats from Mobile Malware
First threat on mobile device was registered in year 2004. By the year 2010 the threat factor increased to 250% and first bank phishing attack was registered from official app market. According to researchers these attacks are only going to get more sophisticated as by the year 2011 botnets were detected in mobile phones. Mobile phones malware threat is fastest growing in recent years and approximately double over the year.
Mobile phones are necessary companions in our modern time lifestyle nowadays.If your mobile device gets compromised than one or more of the following things can happen.
- Banking credentials can be stolen.
- Data in phone can be deleted by operating it remotely.
- Text messages or calls can be sent to premium numbers.
- Phone can be bricked and needs replacement as its dead.
- Owners of botnet can turn your phone into their bot and then use it for launching remote digital attacks like Denial of Service etc.
- Your private information can be compromised. Attacker can intercept your messages and sniff on your phone calls.
Some facts & figures about Mobile Malware
According to security magazines, mobile malwares threat families have shown an increment of 26 % in the third quarter of previous year. According to latest reports more than 300 families of mobile threats are discovered till date this paper is written. As of first month of 2014, a total of 143,211 instances of modified malicious programs have been detected which are affecting and targeting mobile devices.
Cyber criminals use installation packages to distribute malware. Last year close to 4,000,000 installation packages of such kind were used by attackers. About 10,000,000 unique infected installation packages were detected in the year 2012-2013.

The installation packages differ only in terms of application interface etc. that is malicious but installs same kind of programs with little different functionalities.
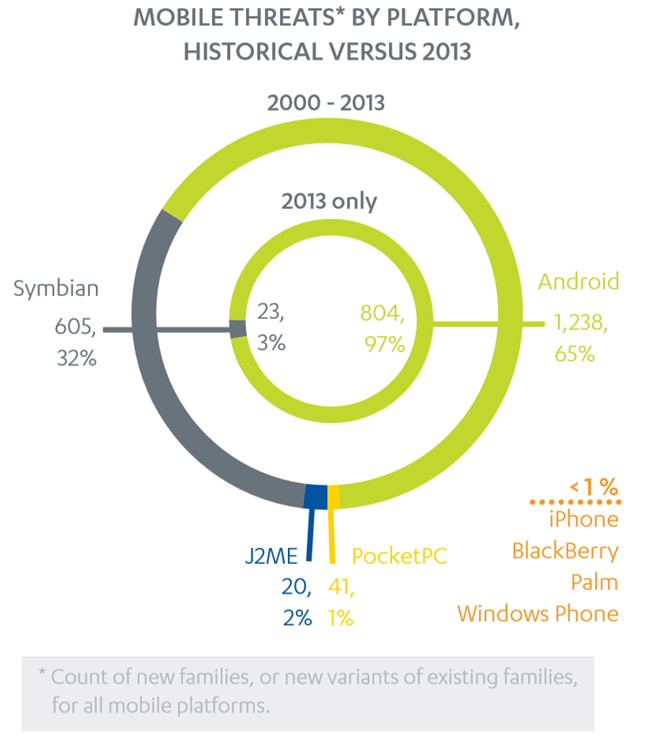
Out of all operating systems, android ruled the kingdom becoming a target of about 98 % of all malicious attacks launched in the previous year. Android being a prime target laid the confirmation of its popularity. But also discovering of so many vulnerabilities revealed the architectural flaws it bears. Most mobile malware was designed to rob users for their money.
They contain malwares like sms-trojans which spreads through simple text messaging and are capable of stealing confidential user data. Along with this loads of backdoors,worms, rootkits were also found to be affecting mobile devices worldwide. The threat of phishing etc. for bank credentials through mobile devices was raised by a factor of 19.7 last year. Anti-viruses caught such infections and prevented thousands of banking Trojans to steal customer data.
Kinds of Malware Threats to Mobile Devices
Phishing
It is creating fake instances of real and legitimate websites and luring the users to enter their credentials in these web forms. Information entered in these are intercepted my malicious attackers who use this information for their monetary gains.
Spywares
This kind of malwares run silently in the system in stealth mode and keep on collecting user data and send them to third party like intercepting your text messages.
App Stores Threats
Many fake copies of legit applications are created by hackers by injecting it with malware code and distributed to users mostly via third party app stores.
Acquiring Access
Some malware instances will exploit architectural vulnerabilities in your device to gain complete control over the device.
Worm
A program code designed to replicate itself in a way to exhaust device memory.
Trojan Horses
These are software which seems to be legit but are built completely to compromise integrity of device.
MITM
This threat mostly works in unsecured wireless channels which are monitored by hackers to get any information that is transmitted through that channel. Accessing public Wi-Fi in any hotspot can make you vulnerable to Wi-Fi snooping attacks.
Direct Attacks
Most of the malware can come directly in your device through files and downloads. SMS can contain Trojans which can act as theft agent. Bluetooth also has a significant role to play in damaging device integrity and spreading malwares.
Malvertising
Made with combination of two words “Malware” and “Advertising“, malvertising is a modern kind of malware distribution technique which is used by hackers to spread their viruses. Basically it is exploiting online advertising methods. In this illegitimate virus, codes etc. are obfuscated with legitimate and genuine advertisements displayed on web pages.
Online ads pass as a solid candidate for spreading malwares as advertisement gurus put loads of effort in making them attractive. These advertisements are designed specifically for the purpose of attracting customers in order to sell product.

All kinds of websites especially the highly celebrated & reputed ones extensively use advertising content for making money online. Therefore, Malvertising provides malicious attackers good opportunities for injecting their malwares into these ads and thereby pushing their attack to web users.
Although using some advance firewall options and shield controls, some of the malicious ads can be blocked but the danger still persists.
Malvertising is a new concept which does not even require compromising whole website. It is much harder to deal with because it can work inside a system without getting noticed and work its way around a webpage. Infections spread through Malvertising silently spread through web pages to user’s systems. The most interesting thing about this kind of infection is that it does not need to exploit any vulnerability in any website. Hence it does not need to compromise server on which website is hosted or performs any kind of attack.
That’s why phenomena of Malvertising are hard to combat with. It is capable of exposing millions of web users to malware no matter how cautious they are. These attacks have a wider reach and are reaching billions of users through advertisement network channels. An estimation of more than 10 billion ad impressions was infected by malware in last year. With such high magnitude of infections, malvertising is such kind of attack vector which does not seems to be disappearing any sooner.
Malvertising in Mobile Devices
In mobile devices, Malvertising is playing a significant role in letting hackers compromise the mobile data. Malvertising smart phones have become the biggest hacking threat and have replaced pornography which used to be biggest threat before. According to report on mobile security by Blue Coat Security Labs, Malvertising threats have increased to three folds in the year 2013 and even more in 2014.
On an average Malvertising is used to direct users to mobile malware through a web ad once in every five times. Last year pornography was held as the leading threat vector amongst all possible threat possibilities but this year it has downgraded to third most threatening attack vector in mobile malwares.

Without proper installation and configuration of security mechanisms, users are far more vulnerable to Malvertising infection. Of all the requested content, 12 % is served as web ads which carry as much as 20 % infected files in all. With increase in traffic and content on mobile devices, infections are also increasing on the same rate. Ad servers has network of largely unregulated systems which can be easily manipulated to distribute malwares to masses.
Threat from Web Apps
In security reports, however Malvertising tops the list but still other threats like web application threats cannot be dismissed. Still most dangerous content category for mobile users is pornography. Although pornography accounts for only 1 % of all the requested content but still it accounts for more than 16 % of all the cyber-attacks. The breach in web applications also posesas quite a potential threat for mobile users. Humans are the weakest link which causes most security breaches. This is done through social engineering.
This tricks mobile users in entering their confidential data to fake pages thereby leaking their information from their own hands unknowingly. Most of the backdoors, Trojans etc. are installed in user’s systems because they are unaware of the content they are browsing or clicking. They easily get lured by fancy advertisements or nice graphics. There are many web pages and advertisements claiming to give away free stuff to users and when users click on the pages, this causes them to get hacked in return.
Threat from Mobile Games
Many security reports says that huge success of mobile games easily and by default makes them prime target for sending malware through them. Mobile consumers do not even have an idea that on the name of a game what they are installing in their device. Mobile entertainment packages like games, recreational categories etc. accounts of around 12 % of all the requested content my mobile users.
Banking Trojan Threat
According to latest mobile threat landscape report by Kaspersky Lab, the numbers of attempts to steal mobile user’s banking data through phishing, Trojan etc. kind of attacks has increased by a factor of 20 last year. In 2013, number of the malicious programs designed for targeting smartphones and tablets doubled to nearly one tenth of a million.
This large variety of mobile malware modifications widely targets carding information of user. More than a quarter hundred infections were blocked by the security software in the last year alone. Amongst the countries in which these attacks were performed, Russia tops the list followed by India, Vietnam, Ukraine and the United Kingdom. Svpeng, perkele and wroba are some notable examples of banking Trojans which has affected mobile banking in a dreadful manner.
We cannot underestimate capability of hackers because it is just a matter of time for them until they discover some other more powerful attack vectors and more lucrative methods for compromising mobile information security.
Mobile Platform Vulnerabilities
Android has been undoubtedly mostly affected and popular platform for mobile devices. Blackberry mostly suffers from spyware applications. Windows and Symbian are the oldest operating systems for mobile phones and are researched widely since.
In Iphones using loose password schemes has been chief candidate in compromising its data. Jail breaking Iphones or Ipad leaves the device with a standard root password which can grant admin access to any attacker easily. This also makes the device susceptible to more malware attacks. Vulnerabilities in android are worth discussing separately.
Vulnerabilities in Android
Android is the chiefly used smartphones and tablets operating system and it claims a lion’s share in the industry of smart devices. Probably because of its popularity it has been the target 98% of all the cyber-attacks in last year. It has many holes in its architecture which accounts for such large number of attacks against it. The interesting thing to be noted is that out of all those infections only 0.1 % can be found on Google play applications.
That means installing applications from unknown sources indeed leverages your system on the surge of attacks. Therefore third party stores are totally loaded up with the content which is not worth stuffing up your smartphones with as they carry malwares.
Android markets like android159 are the carrier of most percentage of mobile malware i.e. 33.3 %. Fake versions of original applications are created by malware writers and fused with malwares to affect mobile devices. Spoofed applications are increasing carrying botnet enabled devices which gives remote access of the phones to attackers.

The reason for play store having least number of infected applications is that Google itself eradicates nefarious applications from its database. Due to this malware applications tend to have shorter shelf life at official Google store and get removed easily.
According to F secure about 804 new families and modified versions of android malware was detected last year. No new malware dysfunctions or vulnerabilities were found in any other smartphone platform other than Symbian. Most of the android attacks are originating from India and Saudi Arabia that accounts for about 75 % of all the attacks. European countries only contribute around 15 % in this list.
It might be considered a security breach on part of Google as it is not paying as much attention towards securing android as it should have. It could bring store to more websites so that malware writers find it harder to infect mobile devices so easily.
Having a non-android device does not keep you at par from these mobile malware either. You are still under the target of various other kinds of security threats.
Psychological Malware
Till now we have been talking about kind of malware threats that steal your information, compromise your device etc. but now we’re going to throw light on another aspect of mobile malwares. This category has no generic classification but you can refer it as “psychological malware”. Talking Angela is a strong candidate in this category.
Talking Angela
On the very first glance Talking Angela is just like any other virtual chat bot program in the form of a cat but if you dig deeper you would know of an entirely different aspect of this application.
Talking Angela is another addition to Outfit7 Talking Tom series which is widely popular; not just among kids and teenagers but also in adults. This application has been downloaded more than 1.5 billion times since its inception and currently more than 230 Million people are using these kinds of applications. Talking Angela was released on December 2012 for IPhones and in January 2013 for android. It spread really fast because its preceding application talking tom was popular as well.

Talking Angela has a child mode which can be turned on or off very easily. Now the crux is that many people claim that this application is operated by a pedophile that interacts with children and asks them weird questions. There is a report that a 7 Year old boy went missing after installing this app.
But none of the security firm confirms any of this to be true. It is classified as psychological malware because irrespective of it being a threat or not but due to spreading of hoax messages through social media channels, this app has forced parents to uninstall this app. No security researcher has yet found anything which can be classified as truly malicious.
Spreading of the Meme
The only problem which created the hoax was that this application text chats on its own. But this can also be controlled by keeping child mode on. The messages posted on social websites like Facebook causes this hoax to become popular instantly. This idea spread really on a rapid rate because people are spreading the hoax messages without even testing the application.
This is just like an advertising campaign which went viral online. As soon as people start getting news they start posting same kind of content and it kind of made a chain reaction. So it can be said that psychological malwares might not exist for real but people made them up to exist.

This causes applications to affect people adversely without even original intentions from app developers. Therefore social media can provide a suitable platform for people to spread their views about any application without properly carrying out behavioral analysis of the app.
These kinds of hoaxes are made up or used by cyber criminals to lure their victims to some kind of webpage. The messages post on Facebook says that it seemed that some human took control of the application in the absence of children’s parents. There are flaws in architecture of the application though which makes turning child mode on and off very easy even for children.
All these kind of hoaxes have a negative impact on children. It is just a cartoon bot which works on completely random ways and claims to delete all the user data that it registers while interacting with kids. According to outfit7 it is totally impossible for a human to take control over the application said Sambo Login, co-founder of the company Outfit7. Its voice changes to something weirdly robotic which seems totally ridiculous as said by Login.
Preventive measures from Mobile Malwares
Now that you are aware of the security breaches and threats that pertain for your mobile devices here is a look at some of the tips that can be used for securing your devices.
Awareness among Users
![]() Most of the threats can easily back out if user is properly informed and alarmed about his devices. Users must understand that applications, games etc. can contain malwares and therefore while installing you should verify the source. Also verify the app permissions and data it is requesting to use. If you find anything suspicious, the rule of thumb, do not install that application and look for an alternative.
Most of the threats can easily back out if user is properly informed and alarmed about his devices. Users must understand that applications, games etc. can contain malwares and therefore while installing you should verify the source. Also verify the app permissions and data it is requesting to use. If you find anything suspicious, the rule of thumb, do not install that application and look for an alternative.
Don’t Use unsecured Wi Fi Networks
![]() Generally, unprotected over the air networks are unsecure and are very much susceptible to malware attacks. There is very high probability that such networks are monitored by attackers and are used for Man in the Middle (MITM) attacks. Therefore mobile users should not just use any Wi Fi network without having proper authentication and knowledge of the source.
Generally, unprotected over the air networks are unsecure and are very much susceptible to malware attacks. There is very high probability that such networks are monitored by attackers and are used for Man in the Middle (MITM) attacks. Therefore mobile users should not just use any Wi Fi network without having proper authentication and knowledge of the source.
Restrict Device access among organization
![]() Although bringing your own device can be an added advantage to company and employee both, but it can add a substantial risk factor to organization integrity. Therefore organization can restrict users from opening some certain kind of web pages, user portals etc. on company devices only. If allowed on employee devices, then they should be aware of how they are using it.
Although bringing your own device can be an added advantage to company and employee both, but it can add a substantial risk factor to organization integrity. Therefore organization can restrict users from opening some certain kind of web pages, user portals etc. on company devices only. If allowed on employee devices, then they should be aware of how they are using it.
Use trusted source for apps
![]() As mentioned in this article as well, a trusted source is less likely to send malware into your mobile device than an unverified one. Therefore to install applications to your mobile phones always use trusted and verified sources. Organization can create a store of their own so that their data is at a lesser risk of getting compromised by third party sources. Users should also be aware of the malware attacks and modifications in applications of their interests.
As mentioned in this article as well, a trusted source is less likely to send malware into your mobile device than an unverified one. Therefore to install applications to your mobile phones always use trusted and verified sources. Organization can create a store of their own so that their data is at a lesser risk of getting compromised by third party sources. Users should also be aware of the malware attacks and modifications in applications of their interests.
Don’t Root your Device
![]() Rooting or jail breaking your device means you are inviting malwares to your device. It voids security of your device because it gives you access to all kinds of applications most of which are infected with malwares.
Rooting or jail breaking your device means you are inviting malwares to your device. It voids security of your device because it gives you access to all kinds of applications most of which are infected with malwares.
Use proper Antimalware
![]() Using updated antivirus solutions can prevent your device from falling victims of malware attacks. Therefore there should always be antimalware, antivirus, antispyware etc. installed in your mobile device.
Using updated antivirus solutions can prevent your device from falling victims of malware attacks. Therefore there should always be antimalware, antivirus, antispyware etc. installed in your mobile device.
Entailing Encryptions
![]() Using strong passwords and encryption schemes for your device especially SIM card etc. can make breaking in and stealing your information a very tedious task. Therefore you are protected by completely encrypting your device.
Using strong passwords and encryption schemes for your device especially SIM card etc. can make breaking in and stealing your information a very tedious task. Therefore you are protected by completely encrypting your device.
Avoid Cloud Sharing Networks
![]() Although sharing your data on cloud makes it accessible to you from any location but still without proper cloud security this data is subject to getting compromised. Organizations can provide cloud sharing alternatives to its employees so that sensitive information can be prevented from leaking out.
Although sharing your data on cloud makes it accessible to you from any location but still without proper cloud security this data is subject to getting compromised. Organizations can provide cloud sharing alternatives to its employees so that sensitive information can be prevented from leaking out.
Update your Operating System
![]() IOS and Blackberry use such kind of application interface which does not support malwares. Therefore only android users are targeted highly by malicious users. You should keep your system up to date so that new modifications and security patches are applied to your devices. You are therefore recommended to keep checking your operating system for any new updates that might be occurring in your software.
IOS and Blackberry use such kind of application interface which does not support malwares. Therefore only android users are targeted highly by malicious users. You should keep your system up to date so that new modifications and security patches are applied to your devices. You are therefore recommended to keep checking your operating system for any new updates that might be occurring in your software.
Conclusion
The trend of attacking smartphones is skyrocketing. It is really dangerous now to use your phone especially for sensitive data exchange like banking transactions without proper precautions. Malicious software that is specifically designed to target valuable customer information is growing rapidly.
More and more of such techniques are raising their heads in the last couple of years. Malware writers are heading towards more sophisticated approach of coding malwares that reduces chances of their detection and removal.
Numerous categories of malwares are detected in recent months. Most prominent was the category of bots because attackers can pursue their interests a big deal through these mobile botnets. Cyber criminals today spread their malwares to earn profits. Therefore mobile phones are at a greater risk of being subject to malware attack.

Android being the mostly used mobile platform is the most affected by malware attack as well. It is primarily due to architectural flaws which require modification on the part of Google itself. Still most of the threat belongs to third party applications which are unauthorized and generally whose writers are unknown.
In the coming years mobile malwares are expected to take a giant leap and go as far to root phones so that malware removal and detection even becomes much harder. Mobile devices can even be used for PCI attacks; first of this kind was registered in 2013.
Therefore it won’t be very much surprising in near future if most of the Wi-Fi attacks is launched through mobile devices only. Along with this SMS Trojans remain a real threat and poses as a challenge to mobile malware forensics that is going to be active in new territories if not controlled on time.
It is not just obvious threats that are marking the emergence of malware threats but some hidden ones like psychological malwares have an equal part to play. A very clear instance we discussed was Talking Angela. There are many such kinds of applications which can be categorized as threats and affected human brains very adversely.
Not just writing but also spreading malwares has taken a leap.
Earlier it used to be only pornography which was considered as a threat and a highly positive malware carrying content category. But in recent times this trend has shifted to Malvertising. The adware’s are posing as a prominent security challenge to information security researchers.The trend is developing rapidly and more and more of the devices are falling victims of infected advertisements.
Lastly, the only way to keep your mobile devices protected from all kinds of threats is to use proper precautions and safeguards. Smartphone users must be aware of secure browsing so that they can identify if their device is victimized or not. Proper antivirus solutions must be installed and updated as they prevent enormous amount of malwares to affect your device.
You may also like:- Top 7 Commercial Linux Distributions
- Why Do I Need a Website?
- Reinforcement Learning in Real-world Applications: The Latest Successes and Challenges
- Various Python Libraries for developing RESTful APIs
- Top 7 NodeJS Frameworks You Need To Know
- How Buying Instagram Followers Can Help Businesses Soar
- How To Find Gaps In Your Cybersecurity And How To Address Them
- How to close the site from indexing using robots.txt
- Internet Security With VPN – Why Do You Need It
- How to Fix The DLL Missing Error in Windows 7?








