
The Tor Project just announced the launch of a public bug bounty program where you can easily earn the money in between $2,000 and $4,000 for high severity flaws.
The Tor’s Bug Bounty Program is now available on Hackerone where you can easily submit your all vulnerabilities which you’ll find in TOR project. The Tor Project is offering bug bounties for two of its core products, Tor (the network daemon) and the most popular Tor Browser.
For Tor the tiers, price ranges and restrictions look like this:
- Low Severity ($100 – $500)
- Medium Severity ($500 – $2000)
- High Severity ($2000 – $4000)
For Tor Browser the tiers, price ranges and restrictions are the following:
- Low Severity ($100 – $1000)
- Medium Severity ($1000 – $2000)
- High Severity ($2000 – $3000+)
Till date they’ve received around 15 Reports which they’ve already resolved and had paid a lumsum amount of $3800 so far.
Here’s How To Get Started
Sign up for an account at HackerOne. Visit https://hackerone.com/torproject for the complete guidelines, details, terms, and conditions of our bug bounty. Then, start finding and reporting bugs to help keep Tor and Tor Browser safe.
You can easily earn thousands of dollars if you find any serious vulnerabilities in the Tor network that could be exploited to track its users.
This isn’t the first time the Tor Project announces the launch of a bounty program, the Tor Project first announced it in December 2015. The Tor Project launched a private program in January 2016 and bug hunters reported three denial-of-service (DoS) flaws, and four memory corruption issues.
Bug bounties are payments made by companies or organisations to researchers who find problems in their website or products, and who then report them. For example, Microsoft/Google/Facebook/Twitter/Instagram etc also offers bounties.
In 2014, Facebook paid a total of $1.3 million in bounties.
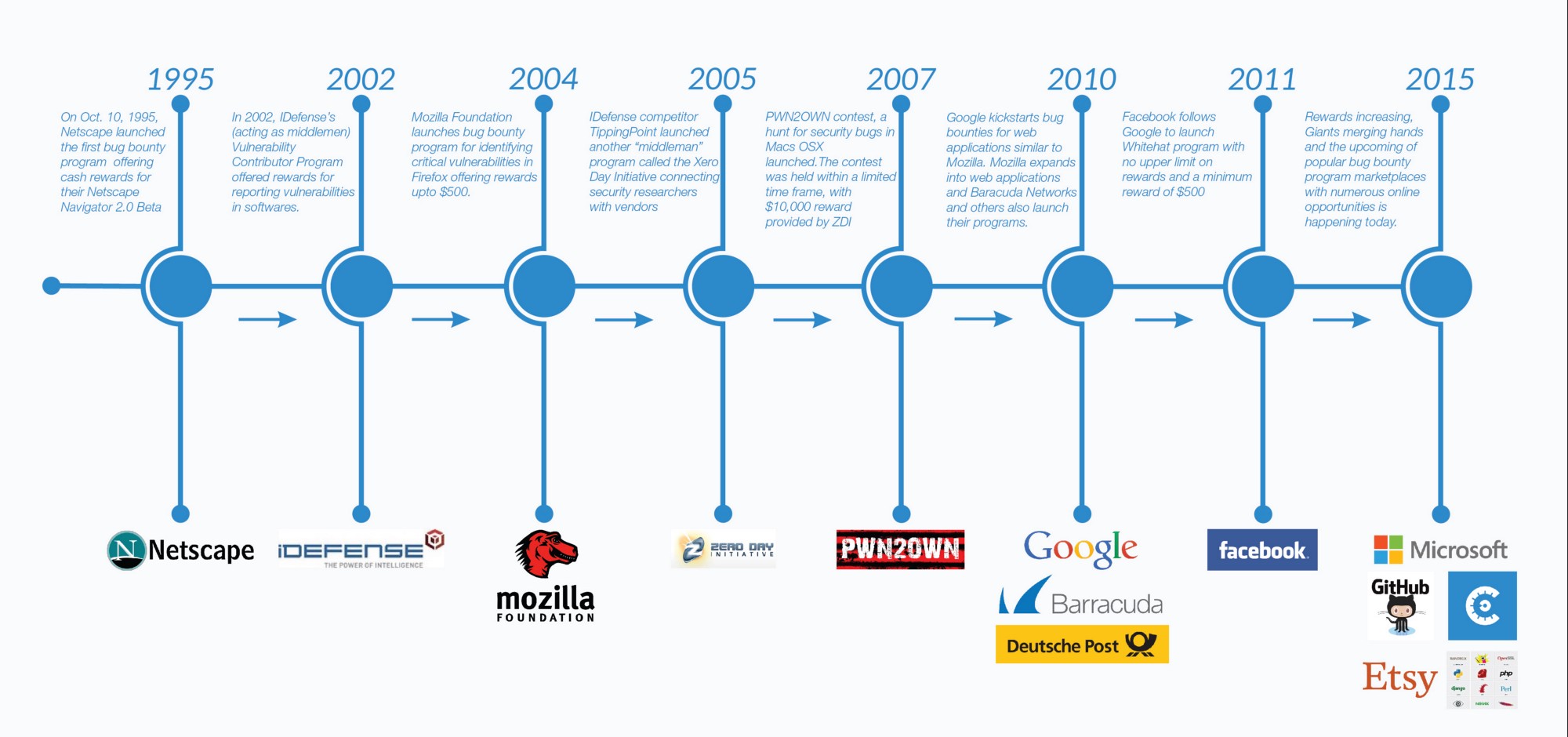
Here are the platforms list where you can participate on similar bug bounty programs:
- a) HackerOne
- b) BugCrowd
- c) FireBounty
- d) GitHub
- e) Facebook
- f) PayPal
- g) United Airlines
- h) Google
- i) Zerodium
- j) Microsoft
- k) Mozilla
- l) Ubuntu
- m) Pidgin
- n) Royal Bank of Scotland
- o) Vodaphone DE
- p) Yandex
- q) Vimeo
- r) Tumblr
- s) Tesla
- t) Symantec
- u) Sony
- v) Shopify
- w) Samsung
- x) Redhat
- y) Rackspace
- z) Oracle
Happy bug hunting!
You may also like:- Top 8 Softwares Free Download – No Credit Card Needed [2021 Update]
- Fonts Hub Collection (Free Design Resources)
- Top 10 Best WordPress Themes From Template Monster
- Get Free Linux VPS – 2019 Limited Offer
- How To Get 5TB Free Cloud Storage Lifetime – 100% Working Method
- Get Windows RDP FREE for one Month – No Credit Card Required
- Freaky! Join Samsung Bug Bounty Program – $200,000 Reward
- Get Free WordPress Hosting – 2017 Lifetime Offer
- 2017: 24 Microsoft Hidden Offers – Claim It Now!
- Get .xyz and .top domain FREE for one Year – Limited Offer 2016-2017








