
A Penetration test is the process of actively evaluating company’s information security measures. Security measures are actively analyzed for design weakness, technical flaws and vulnerabilities. The results are delivered comprehensively in a report, to executive, management, and technical audiences.
An organisation should conduct a risk assessment operation before the penetration testing that will help to identify the main threats such as –
- Communication failure, e-commerce failure and loss of confidential information.
- Public facing systems, websites, email gateways, and remote access platforms.
- Mail, DNS, Firewalls, Passwords, FTPs, IIS and web servers.
Here below we are listing the best penetration testing resources from where you can easily enhance your skills:
1. Metasploit Unleashed (MSFU)
The Metasploit Unleashed (MSFU) course is provided free of charge by Offensive Security in order to raise awareness for underprivileged children in East Africa.
Topics which includes: Metasploit Fundamentals, Information Gathering, Vulnerability Scanning, Writing a Simple Fuzzer, Exploit Development, Web App Exploit Development, Client Side Attacks, MSF Post Exploitation, Meterpreter Scripting, Maintaining Access, MSF Extended Usage, Metasploit GUIs, Post & Auxiliary Module Reference.
Link – https://www.offensive-security.com/metasploit-unleashed/
The full version of this course includes a PDF guide and a set of flash videos which walk you though the modules.

This course opens up a new Metasploit Framework Certification track – the OSMP, Offensive Security Metasploit Professional. The certification exam will be based on hands-on exercises requiring the student to prove they have mastered the MSF in all aspects. The Certification will only be available to those who purchase the videos – our way of encouraging donations to HFC (Hackers for Charity).
2. Penetration Testing Execution Standard (PTES)
Precisely in early 2009 a group of researchers and professionals discussed the value (or lack thereof) of intrusion testing in the industry and created “Penetration Testing Execution Standard“.
Penetration Testing Execution Standard (PTES) is a new standard designed to offer both companies and security service providers a common language and scope for intrusion testing (We prefer to say “intrusion” to “penetration” but in the end finally, it’s all about security assessments).

Following are the main sections defined by the standard as the basis for the execution of intrusion tests:
- Pre-engagement Interactions
- Intelligence Gathering
- Threat Modeling
- Vulnerability Analysis
- Exploitation
- Post Exploitation
- Reporting
For PTES Technical guide, visit pentest-standard.org
3. Open Web Application Security Project (OWASP)
The Open Web Application Security Project (OWASP) is a worldwide not-for-profit charitable organization focused on improving the security of software. Their mission is to make software security visible, so that individuals and organizations are able to make informed decisions.
OWASP is in a unique position to provide impartial, practical information about AppSec to individuals, corporations, universities, government agencies and other organizations worldwide. Operating as a community of like-minded professionals, OWASP issues software tools and knowledge-based documentation on application security.
The OWASP Top 10 is a powerful awareness document for web application security. It represents a broad consensus about the most critical security risks to web applications. Project members include a variety of security experts from around the world who have shared their expertise to produce this list.

For latest OWASP Top 10 (PDF Guide), refer to this link. Not only for Web Application Security, they’ve also published such information for OWASP Mobile Top 10 Risks.and this latest version i.e. OWASP Top 10 – 2017 is fully sponsored by AutoDesk.
Till then they’ve also released two more versions i.e. OWASP Top 10 – 2010 and OWASP Top 10 – 2013
4. PENTEST-WIKI
PENTEST-WIKI is a free online security knowledge library for pentesters / researchers.
Here in this Wiki, you can find various topics related to Vulnerability Assessment and Penetration Testing like Information Gathering, Vulnerability Assessment, Exploitation Tools, Post Exploitation, Privilege Escalation, Maintaining Access and Reporting.
Along with these topics, you can also find useful Books related to information security and some CTF challenge stuff. Due to opensource, you can even directly contribute your stuff to Pentest-Wiki on Github.
5. Penetration Testing Framework 0.59 (PTF)
This is the another useful wiki link where you can find various information related to Network Scanning, Exploitation, Cheatsheets and some other useful commands. This framework is more or less an outline of a penetration test which lists associated tools and results in each section of the test.
Link – http://www.vulnerabilityassessment.co.uk/Penetration%20Test.html
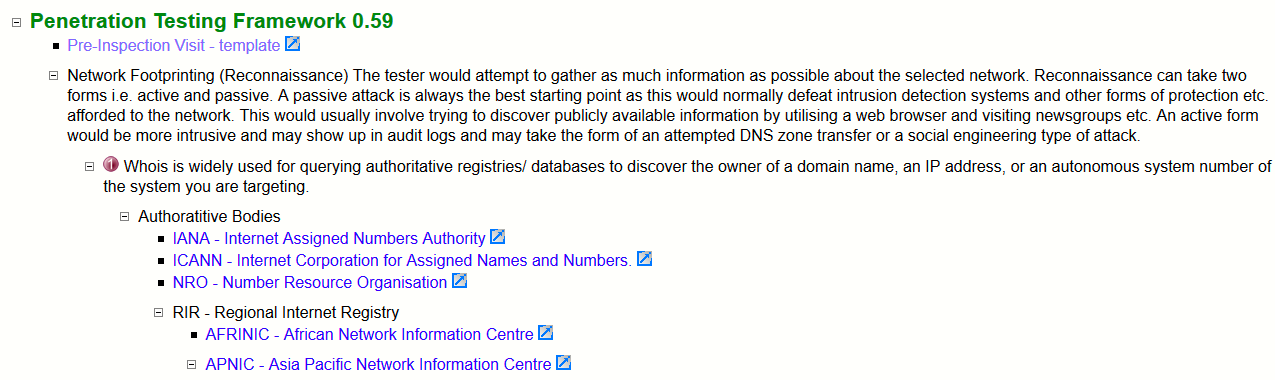
This is not claimed as a standard, but it could be called like that because it shows a systemized approach to penetration testing along with some hints/commands/tools that can be used on various stages.
You may also like:
- Top 7 Commercial Linux Distributions
- Why Do I Need a Website?
- Reinforcement Learning in Real-world Applications: The Latest Successes and Challenges
- Various Python Libraries for developing RESTful APIs
- Top 7 NodeJS Frameworks You Need To Know
- How Buying Instagram Followers Can Help Businesses Soar
- How To Find Gaps In Your Cybersecurity And How To Address Them
- How to close the site from indexing using robots.txt
- Internet Security With VPN – Why Do You Need It
- How to Fix The DLL Missing Error in Windows 7?








