
Security testing is the process of assessing and testing a system/application to discover security risks and vulnerabilities of the system and its data. There is no universal terminology but for our purposes, we define assessments as the analysis and discovery of vulnerabilities without attempting to actually exploit those vulnerabilities. We define testing as the discovery and attempted exploitation of vulnerabilities.
Security testing is often broken out, somewhat arbitrarily, according to either the type of vulnerability being tested or the type of testing being done. A common breakout is:
- Vulnerability Assessment – The system is scanned and analyzed for security issues.
- Penetration Testing – The system undergoes analysis and attack from simulated malicious attackers.
- Runtime Testing – The system undergoes analysis and security testing from an enduser.
- Code Review – The system code undergoes a detailed review and analysis looking specifically for security vulnerabilities.
Here are the list of top 7 tools which can helps you to solve web hacking challenges in real time:
1) BurpSuite
Burp Suite is a complete platform for performing security tests on web applications. Simply put, you make all web requests by Burp so you can analyze / edit and replay them as you please. With this capture, it becomes quite simple to deepen the search for Web vulnerabilities such as SQL, XSS, CSRF, Missing Headers, etc. The tool accepts to combine manual techniques with automatic processes, with the aim of making your work faster, more efficient and more relevant.
This is one of the most versatile and powerful tool for web application testing. BurpSuite is much far better than other proxy intercepting tools like WebScarab, Paros etc. and available for all operating systems i.e. Windows/Mac/Linux.
The following incorporates the following components:
- A local proxy (in interception mode) that will allow to inspect and modify the traffic between your browser (Firefox, Chrome, Opera, etc.) and the target application.
- A powerful web application scanner.
- A tool to retrieve the fields of a Web page in order to be able to modify certain parameters automatically (spider / crawler)
- An intrusion tool, to perform specific attacks to find and exploit vulnerabilities.
- A repeater tool, allowing modification before sending your requests.
- A sequencer to test the randomization of token sessions.
- The ability to stop and resume work later.
- Burp is simple and intuitive, allowing new users to get started with the tool quickly.
Link – https://portswigger.net/burp
Burp Suite Embedded Tools –
a) Central tools
– Proxy: Proxy configuration and chronological view of observed traffic.
– Site map: Tree view of observed traffic.
b) Manual tools
– Repeater: Issuing an individual request.
– Intruder: Mass issue of requests.
c) Automatic tools
– Spider: Passive (resource detection) and active (recursive) collection.
– Scanner: Automatic search for vulnerabilities (passive and / or active mode).
d) Other Tools
– Sequencer: Analysis of the quality of a hazard.
– Decoder: URL / HTML / Base64 / Hexa / Octal / Binary / GZip + hashes conversion.
– Compare: Intuitive comparison of messages (requests or answers).
– Extender: Using plugins developed in Java, Python or Ruby.
e) Configuration
– Macros: Automatic realization of requests.
– Session Management Rules: Applying Logic to Queries and Macros.
– Various settings: Display, backup, keyboard shortcuts, SSL, proxy, …
Basically there are two versions available i.e. Professional Edition which costs around $349.00/year and other is Community Edition which is free for all.
- Free version: Limited features (proxy, repeater, sequencer, decoder etc.).
- Pro version: Complete functionalities (proxy, repeater, sequencer, decoder, scanner, target analysis, session backup etc.).
The pro version offers a number of extra features that are very useful for analyzing one target and improving others. The Pro version also allows you to save and restore the workspace, while the free version only allows you to save the configuration of the tool.
Another advantage of the Pro version is an advanced web crawler to discover content that is not linked to the pages of the target, because Burp suite Pro also tests the plausible paths on a domain.
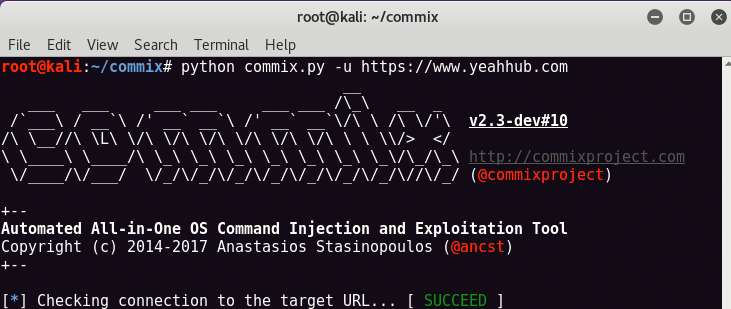
2) Commix
Commix is an automated tool for OS command injection. Commix short for comm and ix where (comm) stands for Command and (ix) stands for Injection & Exploiter developed by Anastasios Stasinopoulos.
Commix tool is Written in Python Language in which you don’t need to compile anything and can easily be installed on Linux, MacOSX and Windows. It is fully compatible with multiple penetration testing tools and frameworks (i.e Metasploit Framework, BurpSuite, SQLMap etc).
Github Link – https://github.com/commixproject/commix
Commix Tool can be used from web developers, penetration testers or even security researchers in order to test web-based applications with the view to find bugs, errors or vulnerabilities related to command injection attacks. By using this tool, it is very easy to find and exploit a command injection vulnerability in a certain vulnerable parameter or HTTP header.
To install Commix, just use below command:
git clone https://github.com/commixproject/commix.git commix
And to get a list of all options, just type
python commix.py -h
3) Hackbar Addon
This toolbar will helps you in testing various web application attacks such as SQL Injections, XSS and other File Inclusion attacks. It is NOT a tool for executing standard exploits and it will NOT teach you how to hack a site.
Hackbar is a Firefox extension for web developers, administrators or more broadly for people with a foot in the system security (white hat & co). Its main purpose is to help a developer do security audits on his code. If you know what your doing, this toolbar will help you do it faster.
Tool Link – https://addons.mozilla.org/en-US/firefox/addon/hackbar/
Features of Hackbar Addon –
- Spoofer its referrer (fake referrer)
- Encode / decode an url (url_encode, url_decode)
- Add or escape characters (addslashes, stripslashes)
- Delete spaces
- Send form data (GET / POST)
- Separate all variables from one URL, line by line and access the URL without having to reform the URL
- Convert a string to MD5, SHA1, ROT13, Base64, hex, etc.
- Perform operations, instructions or SQL commands: conversion of charset, injection, etc.
- And many other things just a click away!

The use of this extension requires a certain amount of knowledge, it is not an extension capable of performing an attack for you, but it will simplify the task of certain operations requiring a PHP script for example.
4) OWASP ZAP
ZAP is one of the world’s most popular website vulnerability scanner and is actively maintained by hundreds of international volunteers. It can help you automatically find security vulnerabilities in your web applications while you are developing and testing your applications.
Github Link – https://github.com/zaproxy/zaproxy
ZAP is designed specifically for testing web applications and is both flexible and extensible. At its core, ZAP is what is known as a “man-in-the-middle proxy.” It stands between the tester’s browser and the web application so that it can intercept and inspect messages sent between browser and web application just like BurpSuite, modify the contents if needed, and then forward those packets on to the destination. It can be used as a stand-alone application, and as a daemon process.
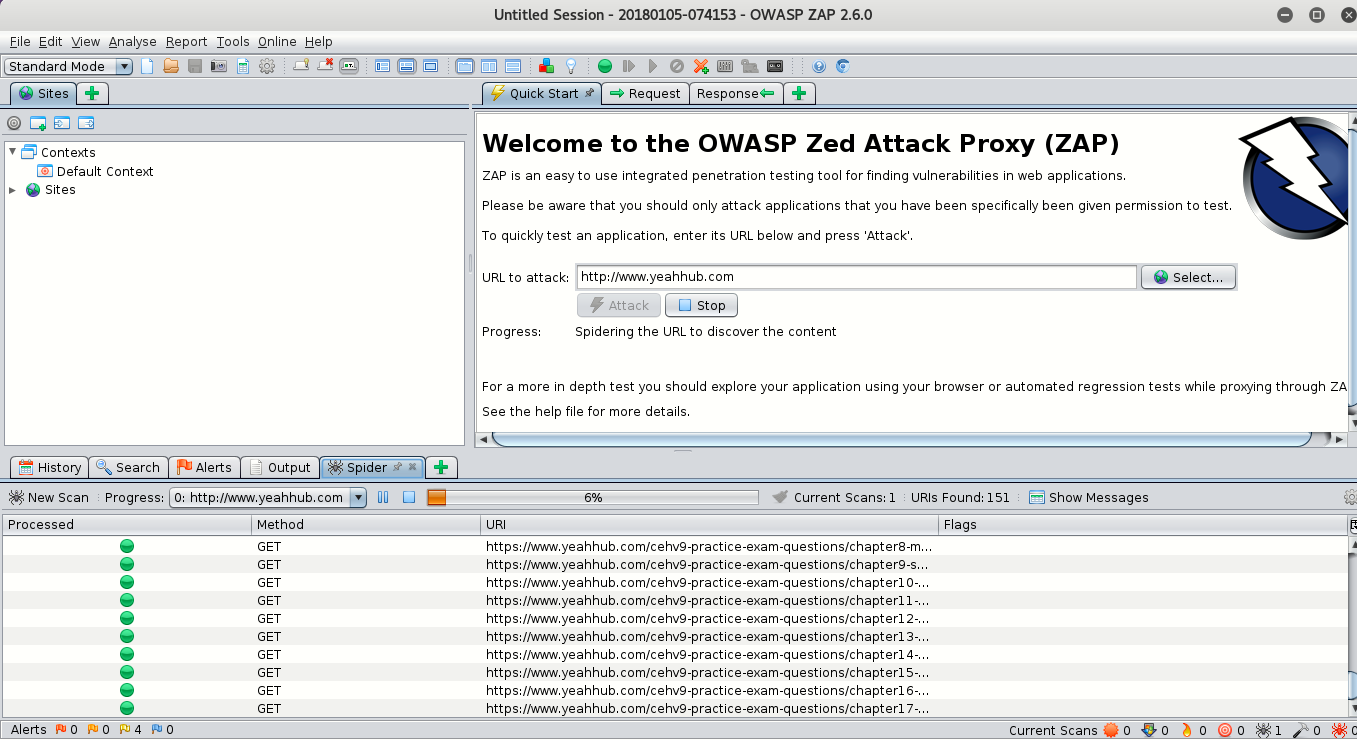
The ZAP UI is composed of the following elements:
- Menu Bar – Provides access to many of the automated and manual tools.
- Toolbar – Includes buttons which provide easy access to most commonly used features.
- Tree Window – Displays the Sites tree and the Scripts tree.
- Workspace Window – Displays requests, responses, and scripts and allows you to edit them.
- Information Window – Displays details of the automated and manual tools.
- Footer – Displays a summary of the alerts found and the status of the main automated tools.
To run ZAP, just type “zaproxy” in your command line terminal.
5) SQLMap
SQLMap is a tool for performing SQL queries in automated ways to find and exploit misconfiguration on your Web server. The latter was developed in Python by Bernardo Damele and Miroslav Stampar. The choice of this programming language is interesting because it allows the tool to be used on any operating system.
As a reminder, SQL injection techniques consist of introducing additive code into a basic SQL query. This will allow a malicious user to recover certain data such as table names, logins, passwords or even worse, to take control of the system.
Github Link – https://github.com/sqlmapproject/sqlmap
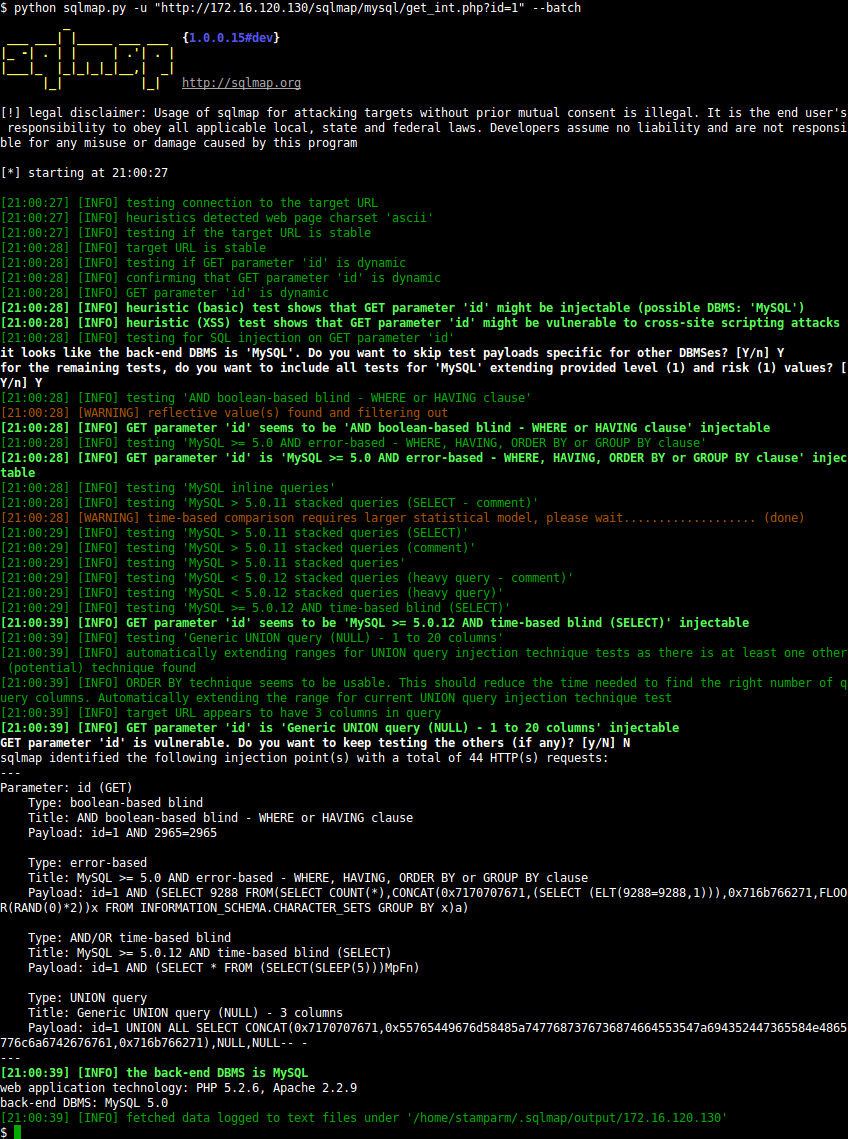
Here are some features of the tool:
- Support for MySQL, Oracle, PostgreSQL and Microsoft SQL Server. In addition to these four database management systems (DBMS), SqlMap also identifies Microsoft Access, DB2, Informix, Sybase and Interbase.
- Support for enumerating users, passwords, privileges, tables, columns, etc.
- Support for multiple SQL injection techniques: blind, UNION, etc.
- Web server fingerprinting
- Integration with other projects such as w3af and Metasploit
- Support authentication methods: HTTP Basic , NTLM and certificate
- etc.
To use SQLMap, just type “sqlmap -u “http://www.example.com/index.php?id=1” –dbs”
6) W3af
W3af is an open source web application security scanner which helps developers and penetration testers identify and exploit vulnerabilities in their web applications. W3af is composed of plugins in 7 different categories: audit, bruteforce, discovery, evasion, grep, mangle and output.
Github Link – https://github.com/andresriancho/w3af
The framework can work on all platforms supported by Python, and w3af has been tested on GNU / Linux, Windows XP, Windows Vista and OpenBSD.

There are two ways to install w3af: from a package (w3af setup for Windows and tgz package for unix-based systems), or from SVN. At the first use; users should use the latest package, while users more Advanced should perform an SVN checkout to get the latest version of the framework.
7) XSSer – Automated XSS testor
Cross Site “Scripter” (aka XSSer) is an automatic framework to detect, exploit and report XSS vulnerabilities in web-based applications. It contains several options to try to bypass certain filters, and various special techniques of code injection.
Website Link – https://xsser.03c8.net/#intro
To use Xsser, just type “xsser -h” in your terminal.

And for Graphical usage, type “xsser –gtk” in your terminal.
- Top 50 Most Popular Cybersecurity Tools
- How Paraphrase Tool Helps To Optimize Content
- Best 20 Kali Linux Tools for Hacking and Penetration Testing
- Top 25 Open Source Intelligence Tools
- Online Domain Authority (DA) Rank Checker Websites
- Top 50 Hacking and Penetration Testing Tools [Compiled List 2019]
- Top 10 Essential CTF Tools for Solving Reversing Challenges
- Windows and Linux Privilege Escalation Tools – Compiled List 2019
- Subdomain Enumeration Tools – 2019 Update
- Top 10 Most Popular Bruteforce Hacking Tools – 2019 Update








