
Netstat is truly a very overlooked tool for network troubleshooting so I believe that it would be beneficial to post all of the switches and options available with NETSTAT.
Netstat displays protocol statistics and current TCP/IP network connections.
Netstat can be run in any version of Windows/Linux by opening a Command window and using the following:
Syntax: netstat [-a] [-b] [-e] [-n] [-o] [-p protocol] [-r] [-s] [-v] [interval]
Another reason we find Netstat such a useful tool is that it can be found on almost any computer by default, from Unix and Linux machines through to Windows and Macs. The fact you don’t have to install and run a separate diagnostic tool can be a life saver when dealing with a client’s PC or a quarantined machine.
Also Read: Top 5 useful netstat commands on windows
This tool is very important and much useful for Linux network administrators as well as system administrators to monitor and troubleshoot their network related problems and determine network traffic performance. This article shows usages of cool netstat commands with their examples which may be useful in daily operation.
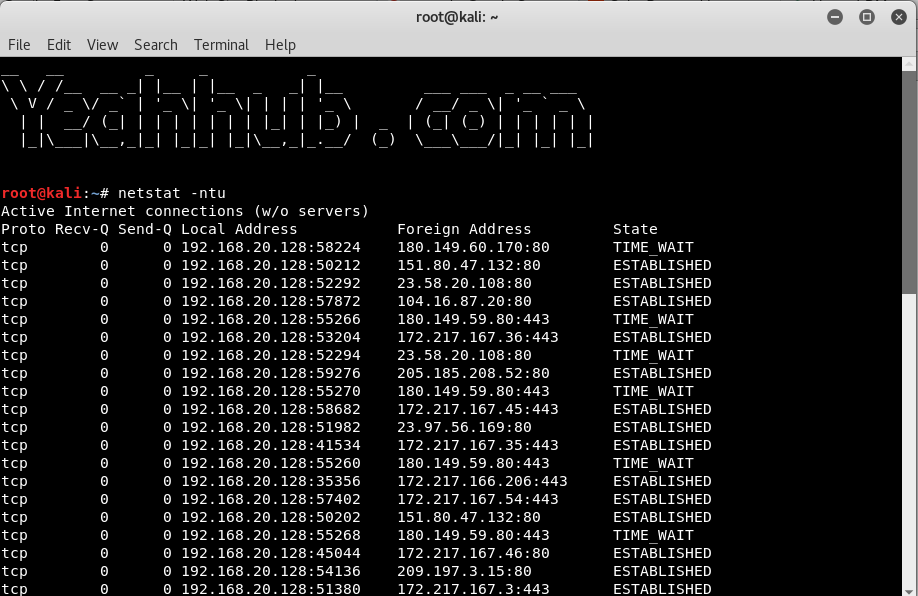
Show Active TCP and UDP Connections –
Command: netstat -ntu
Show All Active TCP/UDP Connections –
Command: netstat -antu

Show All Active Connections to Web Server (E.g. Port 80 Only)
Command: netstat -antu | grep :80

Show All Active Connections to Web Server Excluding Self IP’s (E.g. Port 80 Only)
Command: netstat -antu | grep :80 | grep -v LISTEN

Show All Active Connections to Web Server Excluding Self IP’s (E.g. Port 80 Only)(IP:PORT Format Only)
Command: netstat -antu | grep :80 | grep -v LISTEN | awk ‘{print $5}’
Here, awk has the capability to do data extraction on the basis of below syntax:
| (1)tcp | (2)0 | (3)0 | (4)127.0.0.1:80 | (5)205.185.208.52:80 | (6)ESTABLISHED |

Show All Active Connections to Web Server Excluding Self IP’s (E.g. Port 80 Only)(IP Only)
Command: netstat -antu | grep :80 | grep -v LISTEN | awk ‘{print $5}’ | cut -d: -f1

Show All Active Connections to Web Server Excluding Self IP’s (E.g. Port 80 Only)(IP Only)(Sorted and Unique)
Command: netstat -antu | grep :80 | grep -v LISTEN | awk ‘{print $5}’ | cut -d: -f1 | sort | uniq -c

Show All Active Connections to Web Server Excluding Self IP’s (E.g. Port 80 Only)(IP Only)(Sorted and Unique)(With Connection Count)
Command: netstat -antu | grep :80 | grep -v LISTEN | awk ‘{print $5}’ | cut -d: -f1 | sort | uniq -c | sort -rn

Show All Active Connections to Web Server Excluding Self IP’s (E.g. Port 80 Only)(IP Only)(Sorted and Unique)(With Connection Count)(Exclude Self IP’s)
Command: netstat -antu | grep :80 | grep -v LISTEN | awk ‘{print $5}’ | cut -d: -f1 | sort | uniq -c | sort -rn | grep -v 127.0.0.1

Show All Active Connections to Web Server Excluding Self IP’s (E.g. Port 80 Only)(IP Only)(Sorted and Unique)(With Connection Count)(Exclude Self IP’s)(Final Count)
Command: netstat -antu | grep :80 | grep -v LISTEN | awk ‘{print $5}’ | cut -d: -f1 | sort | uniq -c | sort -rn | grep -v 127.0.0.1 | wc -l

- Top 7 Commercial Linux Distributions
- Why Do I Need a Website?
- Reinforcement Learning in Real-world Applications: The Latest Successes and Challenges
- Various Python Libraries for developing RESTful APIs
- Top 7 NodeJS Frameworks You Need To Know
- How Buying Instagram Followers Can Help Businesses Soar
- How To Find Gaps In Your Cybersecurity And How To Address Them
- How to close the site from indexing using robots.txt
- Internet Security With VPN – Why Do You Need It
- How to Fix The DLL Missing Error in Windows 7?








