
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is damn defenseless. Its main goals are to be an aid for security professionals to test their skills and tools in a…
Read more
A brute-force attack is when all possible keys are checked against encrypted data until the right key is found. Brute-force attacks are extremely costly from a resource and time perspective because the attacker…
Read more
Network Mapper (Nmap) is one of the most effective and functional tools in Kali Linux. Nmap can be used to perform a large range of different scanning techniques and is highly customizable. Nmap is…
Read more
1. Device A has been configured for IRQ 3. Which of the following devices will Device A potentially conflict with? A. COM1 B. LPT1 C. COM2 D. LPT2 2. What is the default…
Read more
Everyone who has been involved with IT for more than a few months has at least heard of MySQL. The acquisition of MySQL AB by Sun Microsystems brought a great deal of additional…
Read more
Meet Ihsan Sencan, a security researcher from Turkey who found more than 15+ SQL Injection Vulnerabilities in various Joomla Components in just one day and all related exploits have been published to various…
Read more
A security expert Belahsan Ouerghi has shed light on a new hacking tool called DVR Exploiter that exploits the CVE-2018-9995 vulnerability against IoT devices. It is able to extract account credentials of DVR…
Read more
1. Which of the following components is not usually found on a motherboard? A. Hard drive controller B. DVD drive controller C. Memory D. Video adapter 2. What type of memory is not…
Read more
Python is a general purpose programming language that is often applied in scripting roles. It is commonly defined as an object-oriented scripting language – a definition that blends support for OOP with an…
Read more
Designing the database is a key step, largely because changes to the database at a later date have far larger implications and potential complications than changing any other aspect of the site. Adding functionality through…
Read more
A hash is always a useful when you need to verify the integrity of any file. To check the integrity of your system, you can create a baseline of file hashes, and periodically…
Read more
Python is one of those rare languages which can claim to be both simple and powerful. Python is an easy to learn, powerful programming language. It has efficient high-level data structures and a simple…
Read more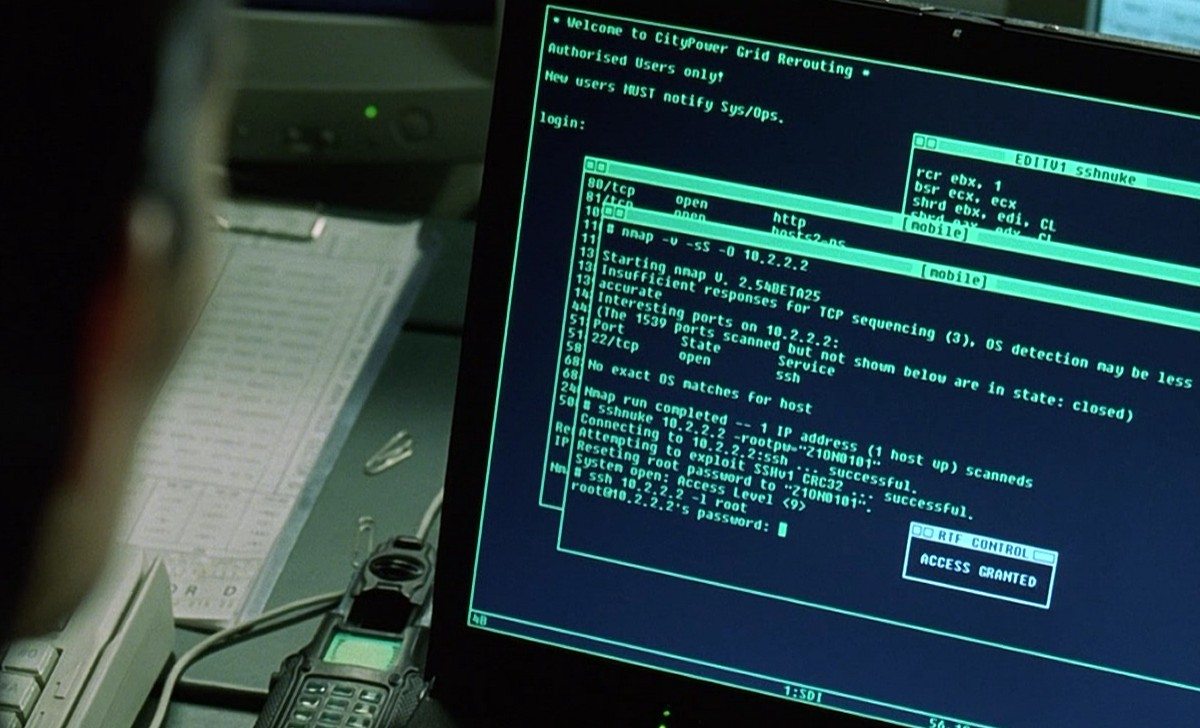
Nmap supports many scanning technologies, such as: UDP, TCP connect(), TCP SYN (half-open scan), ftp proxy (bounce attack), reverse flag, ICMP, FIN, ACK scan, Xmas Tree, SYN Scan and null scan. Nmap also…
Read more
Wireless technology has become increasingly popular as it allows you to easily access the Internet from all sorts of locations around the world without requiring a network cable. But a wireless network isn’t…
Read more
There are plenty of ways to make your password secure, but most people just don’t bother. It is much easier to set a password that is easy to remember, but hackers rely on…
Read more
UNIX treats every object in the operating system as a file. We can find the files associated with every action performed and can make use of them for different system- or process-related manipulations….
Read more





